Exam Details
Exam Code
:101Exam Name
:Application Delivery FundamentalsCertification
:F5 CertificationsVendor
:F5Total Questions
:699 Q&AsLast Updated
:Apr 13, 2025
F5 F5 Certifications 101 Questions & Answers
-
Question 201:
in which scenario is a full proxy TCP connection required?
A. when compression is actuated
B. When Source NAT configured
C. when a virtual server is configured
D. When Source IP persistence is required
-
Question 202:
The use of attack signature within an intrusion Detection System (IDS) is an application of which security model?
A. Positive
B. Context-based
C. Negative
D. Role-based
-
Question 203:
An administrator needs to protect a web application from cross-site scripting (CSS) exploits. Which F5 protocol provide this functionality
A. ASM
B. APM
C. AFM
D. GTM
-
Question 204:
What is the correct procedure to comply with the recommendation?
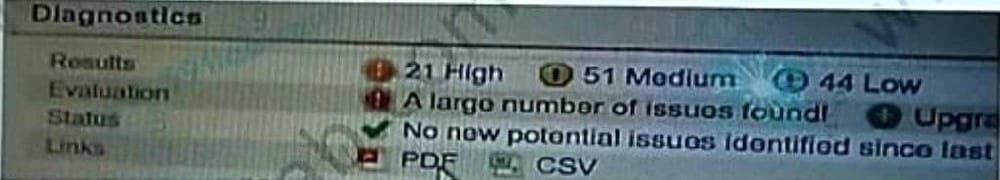
A. Download the product version image from ihealth f5 com
B. Download the product version image from support 6 com
C. Download the product version image from dovcentral f5.com
D. Download the product version image from downloads f5.com
-
Question 205:
If there are multiple applications authenticated against a single identity store, which technology solution will simplify access to all applications?
A. RADIUS
B. single sign on
C. multifactor authentication
D. LDAP
-
Question 206:
An administrator needs to load balance connections to the application server with the lowest number of
Which load balancing method meets these requirements?
A. Least Sessions
B. Ratio Least Connections (member)
C. Least Connections (member)
D. Least Connections (node)
-
Question 207:
Which HTTP response code is returned when a web server requires authentication to access a resource?
A. 500
B. 401
C. 302
D. 100
-
Question 208:
A BIG IP Administrator reviews the Virtual Server configuration and sees the object status represented by a blue square tor an unknown status. How should the administrator change the unknown status?
A. restart the BIG-IP device
B. assign a monitor to the pool
C. restart the backend webserver
D. run a packet capture on the BIG-IP device
-
Question 209:
HTTPs traffic is not working properly. What is the likely reason for the issue?
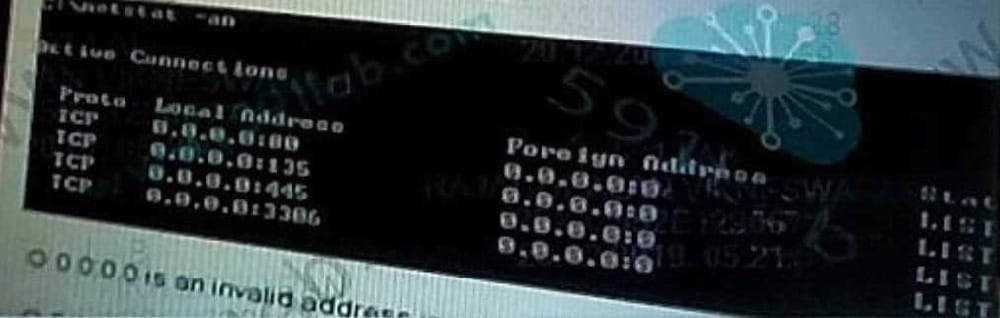
A. 0. 0 0.0 0 is an invalid address in netstat.
B. 0. 0. 0. 0.0 80 should be in an active stale
C. The server is not listening on TCP 443
D. The server is not listening on UDP 80
-
Question 210:
A client needs to learn if a web server supports POST Which HTTP method is used?
A. OPTIONS
B. TRACE
C. LIST
D. GET
Related Exams:
101
Application Delivery Fundamentals201
TMOS Administration301A
BIG-IP LTM Specialist: Architect, Set up and Deploy301B
BIG-IP Local Traffic Manager (LTM) Specialist: Maintain & Troubleshoot771-101
Application Delivery FundamentalsF50-506
F5 FirePass 600 V5F50-531
BIG-IP v10.x LTM Essentials V10.xF50-536
BIG-IP ASM v10.x
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only F5 exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 101 exam preparations and F5 certification application, do not hesitate to visit our Vcedump.com to find your solutions here.