Exam Details
Exam Code
:101Exam Name
:Application Delivery FundamentalsCertification
:F5 CertificationsVendor
:F5Total Questions
:699 Q&AsLast Updated
:Apr 13, 2025
F5 F5 Certifications 101 Questions & Answers
-
Question 261:
A BIG-IP has the following objects configured: A SNAT pool with 2 members:
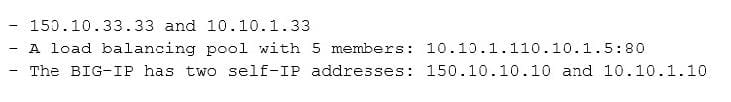
A virtual server at 150.10.30.30:80 that is associated with both the SNAT pool and the load balancing pool. If a client at IP address 200.10.10.10 initiates a connection to the virtual server, what will the source IP address be in the packets sent
to the chosen pool member?
A. 150.10.30.30
B. 150.10.33.33
C. 10.10.1.10
D. It could be any of the addresses of the members of the load balancing pool.
E. 10.10.1.33
F. 200.10.10.10
-
Question 262:
Which statement is true regarding OneConnect processing?
A. The virtual server must have UDP profile.
B. Server-side request can utilize existing client-side connections.
C. The number of client connection is reduced.
D. Client-side request can utilize existing server-side connections.
-
Question 263:
The F5 Application Delivery Firewall has the ability to outperform traditional and next generation firewalls during DDoS attacks by leveraging the performance and scalability of BIG-IP to hand extremely high loads, including high throughput, high connection count, and high number of connections per second.
A. True
B. False
-
Question 264:
On a standalone BIG-IP ASM system, which of the following configuration is valid?
A. Pool named http_pool with 1 pool member, no persistence, and no load balancing method
B. Pool named http_pool with 3 pool members, cookie persistence, and ratio load balancing method
C. Pool named http_pool with 2 pool members, source IP persistence, and least connections load balancing method
D. Pool named http_pool with 3 pool members, cookie persistence, and least connections load balancing method
-
Question 265:
Which three of these scenarios should you identify as being an APM opportunity? (Choose three.)
A. An organization using Novell Netware for authentication.
B. An organization that has been recently fined for failing security compliance.
C. An organization with a traveling sales force.
D. An organization with a single location and no remote employees.
E. An organization that needs to ensure users are using Symantec antivirus software.
F. An organization sharing a public Web site for all Internet users.
-
Question 266:
The BIG-IP ASM System is configured with a virtual server that contains an HTTP class profile and the protected pool members are associated within the HTTP class profile pool definition. The status of this virtual server is unknown (Blue). Which of the following conditions will make this virtual server become available (Green)?
A. Assign a successful monitor to the virtual server
B. Assign a successful monitor to the members of the HTTP class profile pool
C. Associate a fallback host to the virtual server and assign a successful monitor to the fallback host
D. Associate a default pool to the virtual server and assign a successful monitor to the pool members
-
Question 267:
Learning suggestions in the Policy Building pages allow for which of the following? (Choose two.)
A. XML-based parameters and associated schema are automatically learned.
B. Blocking response pages can be automatically generated from web site content.
C. Flow level parameters are displayed when found and can be accepted into the current policy.
D. The administrator may modify whether the BIG-IP ASM System will learn, alarm, or block detected violations.
E. Maximum acceptable values for length violations are calculated and can be accepted into the security policy by the administrator.
-
Question 268:
True or False, WOM speeds up large file data transfer across the WAN between a Windows client and a Windows file Server.
A. True
B. False
-
Question 269:
Which method of protection is not provided by the Rapid Deployment policy template?
A. Data leakage
B. Buffer overflow
C. HTTP protocol compliance
D. Dynamic parameter validation
-
Question 270:
Which of the following is NOT a method that TMOS uses to improve the performance of applications?
A. Caching HTTP data
B. Optimizing the TCP connection between the client and the BIG-IP device
C. Offloading SSL decryption from downstream servers
D. Discarding unnecessary data from server responses before sending to the client
E. Compressing HTTP data
Related Exams:
101
Application Delivery Fundamentals201
TMOS Administration301A
BIG-IP LTM Specialist: Architect, Set up and Deploy301B
BIG-IP Local Traffic Manager (LTM) Specialist: Maintain & Troubleshoot771-101
Application Delivery FundamentalsF50-506
F5 FirePass 600 V5F50-531
BIG-IP v10.x LTM Essentials V10.xF50-536
BIG-IP ASM v10.x
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only F5 exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 101 exam preparations and F5 certification application, do not hesitate to visit our Vcedump.com to find your solutions here.