Exam Details
Exam Code
:101Exam Name
:Application Delivery FundamentalsCertification
:F5 CertificationsVendor
:F5Total Questions
:699 Q&AsLast Updated
:Apr 13, 2025
F5 F5 Certifications 101 Questions & Answers
-
Question 511:
If LTM uses the least connections load balancing method, which pool member in the following diagram receives the next request?
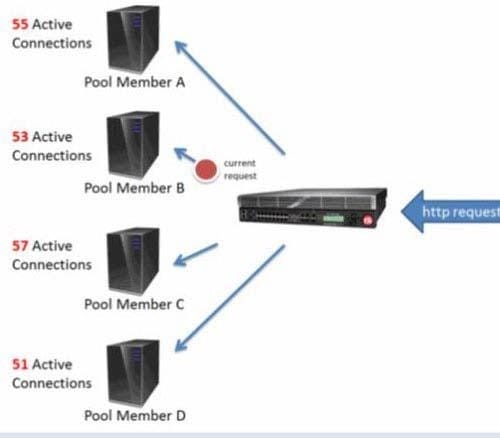
A. A
B. B
C. C
D. D
-
Question 512:
Which of the following can be associated with an XML profile?
A. Flow
B. Method
C. Parameter
D. File type
-
Question 513:
Which of the following does NOT describe network performance management?
A. Updating software on various devices
B. Seeing graphs in near real-time
C. Visibility into multiple network devices
D. Being alerted to an issue as it happens
E. Viewing virtual server statistics
-
Question 514:
Another name for the F5 OneConnect feature is TCP multiplexing.
A. True
B. False
-
Question 515:
When initially configuring the GTM System using the config tool, which two parameters can be set? (Choose two.)
A. System hostname
B. IP Address of management port
C. IP Address of the external VLAN
D. Default route for management port
E. Port lockdown of management port
-
Question 516:
When using a routed configuration, the real server must point to the LTM as the ________.
A. NTP Server
B. DNS Server
C. Virtual IP
D. WINS server
E. Default gateway
-
Question 517:
Which two of the following statements about how TMOS typically manages traffic between a client and server are accurate? (Choose two.)
A. It changes the destination address before forwarding a request to the server.
B. It changes the destination address before sending a response to the client.
C. It changes the source address before sending a response to the client.
D. It changes the source address before forwarding a request to the server.
-
Question 518:
Which three of these file types work well with HTTP compression? (Choose three.)
A. MP4 videos
B. Digital photos
C. Text files
D. Static HTML Web pages
E. CD quality songs
F. Microsoft Word documents
-
Question 519:
The production version of BIG-IP Virtual Edition is limited to 200 Mbps throughput.
A. True
B. False
-
Question 520:
Which of the following statements are correct regarding positive and negative security models?
(Choose two.)
A. Positive security model allows all transactions by default.
B. Negative security model denies all transactions by default.
C. Negative security model allows all transactions by default and rejects only transactions that contain attacks.
D. Positive security mode l denies all transactions by default and uses rules that allow only those transactions that are considered safe and valid.
Related Exams:
101
Application Delivery Fundamentals201
TMOS Administration301A
BIG-IP LTM Specialist: Architect, Set up and Deploy301B
BIG-IP Local Traffic Manager (LTM) Specialist: Maintain & Troubleshoot771-101
Application Delivery FundamentalsF50-506
F5 FirePass 600 V5F50-531
BIG-IP v10.x LTM Essentials V10.xF50-536
BIG-IP ASM v10.x
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only F5 exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 101 exam preparations and F5 certification application, do not hesitate to visit our Vcedump.com to find your solutions here.