Exam Details
Exam Code
:156-215.80Exam Name
:Check Point Certified Security Administrator (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:535 Q&AsLast Updated
:Mar 03, 2025
CheckPoint Checkpoint Certifications 156-215.80 Questions & Answers
-
Question 471:
Which deployment adds a Security Gateway to an existing environment without changing IP routing?
A. Distributed
B. Bridge Mode
C. Remote
D. Standalone
-
Question 472:
Fill in the blank: An identity server uses a ___________ for user authentication.
A. Shared secret
B. Certificate
C. One-time password
D. Token
-
Question 473:
You can see the following graphic:
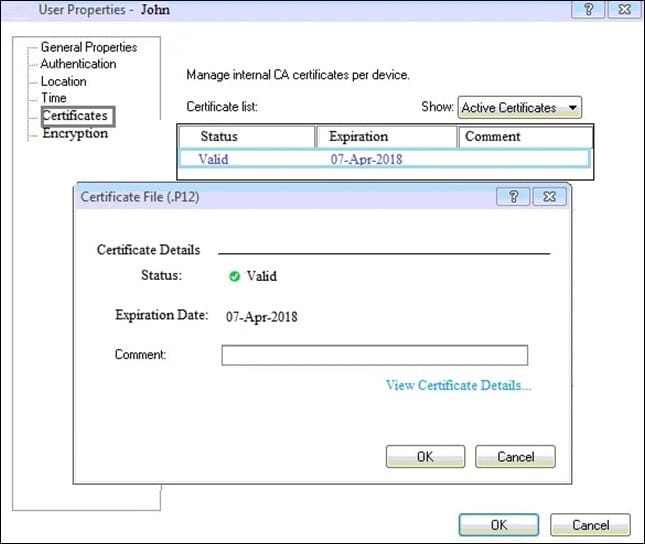
What is presented on it?
A. Properties of personal .p12 certificate file issued for user John.
B. Shared secret properties of John's password.
C. VPN certificate properties of the John's gateway.
D. Expired .p12 certificate properties for user John.
-
Question 474:
True or False: In R80, more than one administrator can login to the Security Management Server with write permission at the same time.
A. False, this feature has to be enabled in the Global Properties.
B. True, every administrator works in a session that is independent of the other administrators.
C. True, every administrator works on a different database that is independent of the other administrators.
D. False, only one administrator can login with write permission.
-
Question 475:
After trust has been established between the Check Point components, what is TRUE about name and IP-address changes?
A. Security Gateway IP-address cannot be changed without re-establishing the trust
B. The Security Gateway name cannot be changed in command line without re-establishing trust
C. The Security Management Server name cannot be changed in SmartConsole without re-establishing trust
D. The Security Management Server IP-address cannot be changed without re-establishing the trust
-
Question 476:
Which two Identity Awareness commands are used to support identity sharing?
A. Policy Decision Point (PDP) and Policy Enforcement Point (PEP)
B. Policy Enforcement Point (PEP) and Policy Manipulation Point (PMP)
C. Policy Manipulation Point (PMP) and Policy Activation Point (PAP)
D. Policy Activation Point (PAP) and Policy Decision Point (PDP)
-
Question 477:
Which is NOT an encryption algorithm that can be used in an IPSEC Security Association (Phase 2)?
A. AES-GCM-256
B. AES-CBC-256
C. AES-GCM-128
-
Question 478:
Fill in the blank: To create policy for traffic to or from a particular location, use the _____________.
A. DLP shared policy
B. Geo policy shared policy
C. Mobile Access software blade
D. HTTPS inspection
-
Question 479:
You have discovered suspicious activity in your network. What is the BEST immediate action to take?
A. Create a policy rule to block the traffic.
B. Create a suspicious action rule to block that traffic.
C. Wait until traffic has been identified before making any changes.
D. Contact ISP to block the traffic.
-
Question 480:
Tom has connected to the R80 Management Server remotely using SmartConsole and is in the process of making some Rule Base changes, when he suddenly loses connectivity. Connectivity is restored shortly afterward. What will happen to the changes already made:
A. Tom's changes will have been stored on the Management when he reconnects and he will not lose any of this work.
B. Tom will have to reboot his SmartConsole computer, and access the Management cache store on that computer, which is only accessible after a reboot.
C. Tom's changes will be lost since he lost connectivity and he will have to start again.
D. Tom will have to reboot his SmartConsole computer, clear the cache and restore changes.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.80 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.