Exam Details
Exam Code
:156-215.80Exam Name
:Check Point Certified Security Administrator (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:535 Q&AsLast Updated
:Mar 03, 2025
CheckPoint Checkpoint Certifications 156-215.80 Questions & Answers
-
Question 71:
Choose what BEST describes users on Gaia Platform.
A. There is one default user that cannot be deleted.
B. There are two default users and one cannot be deleted.
C. There is one default user that can be deleted.
D. There are two default users that cannot be deleted and one SmartConsole Administrator.
-
Question 72:
R80 Security Management Server can be installed on which of the following operating systems?
A. Gaia only
B. Gaia, SPLAT, Windows Server only
C. Gaia, SPLAT, Windows Server and IPSO only
D. Gaia and SPLAT only
-
Question 73:
What port is used for delivering logs from the gateway to the management server?
A. Port 258
B. Port 18209
C. Port 257
D. Port 981
-
Question 74:
Bob and Joe both have Administrator Roles on their Gaia Platform. Bob logs in on the WebUI and then Joe logs in through CLI. Choose what BEST describes the following scenario, where Bob and Joe are both logged in:
A. When Joe logs in, Bob will be log out automatically.
B. Since they both are log in on different interfaces, they both will be able to make changes.
C. If Joe tries to make changes, he won't, database will be locked.
D. Bob will be prompt that Joe logged in.
-
Question 75:
Fill in the blank: When LDAP is integrated with Check Point Security Management, it is then referred to as
A. UserCheck
B. User Directory
C. User Administration
D. User Center
-
Question 76:
Which Check Point software blade provides protection from zero-day and undiscovered threats?
A. Firewall
B. Threat Emulation
C. Application Control
D. Threat Extraction
-
Question 77:
Which of the completed statements is NOT true? The WebUI can be used to manage user accounts and:
A. assign privileges to users.
B. edit the home directory of the user.
C. add users to your Gaia system.
D. assign user rights to their home directory in the Security Management Server
-
Question 78:
Look at the following screenshot and select the BEST answer.

A. Clients external to the Security Gateway can download archive files from FTP_Ext server using FTP.
B. Internal clients can upload and download any-files to FTP_Ext-server using FTP.
C. Internal clients can upload and download archive-files to FTP_Ext server using FTP.
D. Clients external to the Security Gateway can upload any files to the FTP_Ext-server using FTP.
-
Question 79:
Fill in the blanks: A security Policy is created in _________ , stored in the _________ , and Distributed to the various __________ .
A. Rule base, Security Management Server, Security Gateways
B. SmartConsole, Security Gateway, Security Management Servers
C. SmartConsole, Security Management Server, Security Gateways
D. The Check Point database, SmartConsole, Security Gateways
-
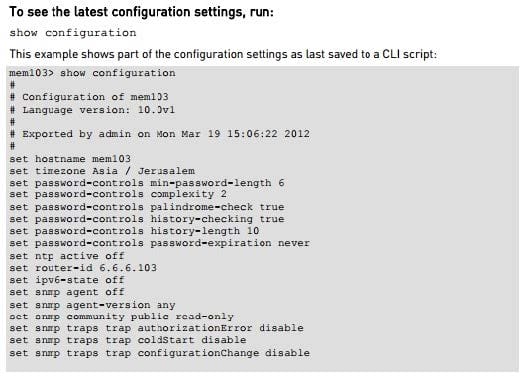
Question 80:
Look at the screenshot below. What CLISH command provides this output?
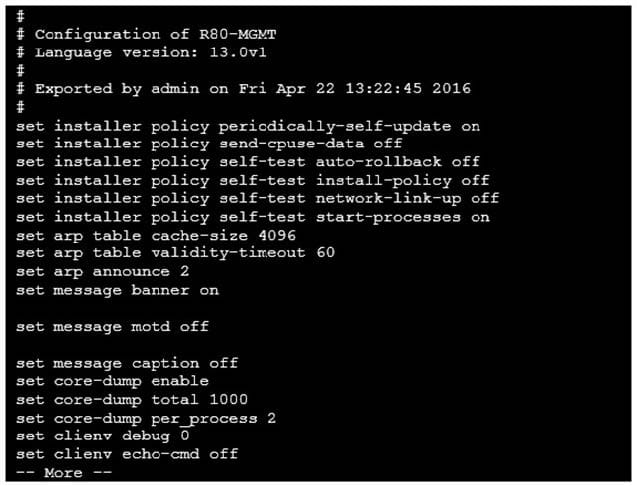
A. show configuration all
B. show confd configuration
C. show confd configuration all
D. show configuration
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.80 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.