Exam Details
Exam Code
:156-315.81Exam Name
:Check Point Certified Security Expert - R81 (CCSE)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:624 Q&AsLast Updated
:Mar 11, 2025
CheckPoint Checkpoint Certifications 156-315.81 Questions & Answers
-
Question 41:
What is the name of the secure application for Mail/Calendar for mobile devices?
A. Capsule Workspace
B. Capsule Mail
C. Capsule VPN
D. Secure Workspace
-
Question 42:
Which command gives us a perspective of the number of kernel tables?
A. fw tab -t
B. fw tab -s
C. fw tab -n
D. fw tab -k
-
Question 43:
Under which file is the proxy arp configuration stored?
A. $FWDIR/state/proxy_arp.conf on the management server
B. $FWDIR/conf/local.arp on the management server
C. $FWDIR/state/_tmp/proxy.arp on the security gateway
D. $FWDIR/conf/local.arp on the gateway
-
Question 44:
SecureXL improves non-encrypted firewall traffic throughput and encrypted VPN traffic throughput.
A. This statement is true because SecureXL does improve all traffic.
B. This statement is false because SecureXL does not improve this traffic but CoreXL does.
C. This statement is true because SecureXL does improve this traffic.
D. This statement is false because encrypted traffic cannot be inspected.
-
Question 45:
To add a file to the Threat Prevention Whitelist, what two items are needed?
A. File name and Gateway
B. Object Name and MD5 signature
C. MD5 signature and Gateway
D. IP address of Management Server and Gateway
-
Question 46:
When setting up an externally managed log server, what is one item that will not be configured on the R81 Security Management Server?
A. IP
B. SIC
C. NAT
D. FQDN
-
Question 47:
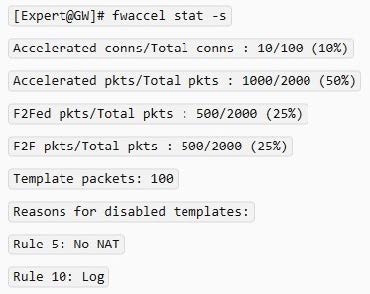
An administrator would like to troubleshoot why templating is not working for some traffic. How can he determine at which rule templating is disabled?
A. He can use the fw accel stat command on the gateway.
B. He can use the fw accel statistics command on the gateway.
C. He can use the fwaccel stat command on the Security Management Server.
D. He can use the fwaccel stat command on the gateway
-
Question 48:
You have existing dbedit scripts from R77. Can you use them with R81.20?
A. dbedit is not supported in R81.20
B. dbedit is fully supported in R81.20
C. You can use dbedit to modify threat prevention or access policies, but not create or modify layers
D. dbedit scripts are being replaced by mgmt_cli in R81.20
-
Question 49:
What is the benefit of "tw monitor" over "tcpdump"?
A. "fw monitor" reveals Layer 2 information, while "tcpdump" acts at Layer 3.
B. "fw monitor" is also available for 64-Bit operating systems.
C. With "fw monitor", you can see the inspection points, which cannot be seen in "tcpdump"
D. "fw monitor" can be used from the CLI of the Management Server to collect information from multiple gateways.
-
Question 50:
What is the purpose of a SmartEvent Correlation Unit?
A. The SmartEvent Correlation Unit is designed to check the connection reliability from SmartConsole to the SmartEvent Server.
B. The SmartEvent Correlation Unit's task it to assign severity levels to the identified events.
C. The Correlation unit role is to evaluate logs from the log server component to identify patterns/threats and convert them to events.
D. The SmartEvent Correlation Unit is designed to check the availability of the SmartReporter Server.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-315.81 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.