Exam Details
Exam Code
:156-727.77Exam Name
:Threat PreventionCertification
:CheckPoint CertificationVendor
:CheckPointTotal Questions
:53 Q&AsLast Updated
:Mar 04, 2025
CheckPoint CheckPoint Certification 156-727.77 Questions & Answers
-
Question 11:
What is the most common way a computer can become infected with a bot?
A. Malvertising
B. Users accessing malicious web sites
C. Adobe file vulnerabilities
D. Microsoft file vulnerabilities
-
Question 12:
Bots and viruses appear as __________ in the reporting blade.
A. Threats
B. Incidents
C. Malware
D. Infections
-
Question 13:
Joey is the MegaCorp Firewall administrator. Which options does he have for the configuration of the Threat Emulation Analysis Location on his gateway?
A. Only Check Point Threat Cloud
B. Upload the Files to the Check Point SFTP-Server
C. It depends on the operating systems that need to be supported
D. Either Check Point Threat Cloud or locally (dedicated or existing gateway)
-
Question 14:
When is the default Threat Prevention profile enforced?
A. At the first Security Policy installation.
B. Only after SensorNET participation is enabled.
C. When the profile is assigned to a gateway.
D. When the administrator installs the profile on Security Gateway.
-
Question 15:
Which of the following statements regarding the threat prevention database is NOT correct?
A. The Security management server connects to the internet to get Malware Database updates.
B. By default, updates run on the security gateway every two hours.
C. The malware database only updates if you have a valid Anti-Bot/ or Anti-Virus contract.
D. The security gateway contains a local cache of the malware requests.
-
Question 16:
When configuring Anti-Bot and Anti-Virus, you notice the following error in the Update Status of the Gateways page:
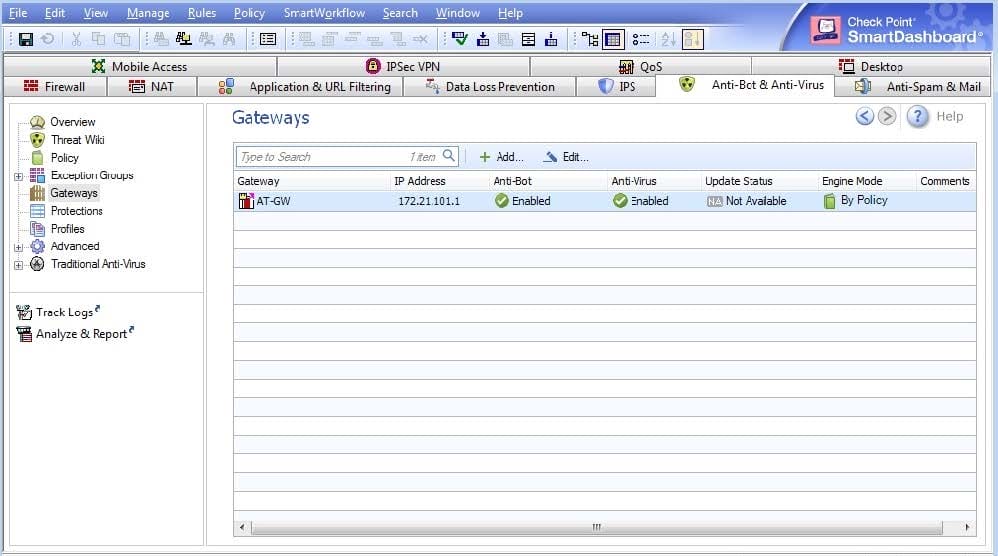
What is the most likely cause of this error?
A. The Security Gateway is not licensed for Anti-Bot and Anti-Virus inspection.
B. There are no updates available for the participating gateway.
C. The Anti-Bot and Anti-Virus policy is not installed on the gateway.
D. You do not have DNS or proxy settings configured for the gateway.
-
Question 17:
Put these HTTPS traffic inspections steps in the correct order.
a.
Validates the web site's server certificate
b.
Intercepts HTTPS requests
c.
Decrypts data from client and inspects clear text content
d.
Decrypts response from server and inspects clear text content
e.
Creates a certificate for use between gateway and client
f.
Encrypts data and sends data to web server
g.
Encrypts data and sends data to client
h.
Establishes a secure connection to the requested web site
A.
a, e, b, h, c, f, d, g
B.
a, b, f, d, c, g, h, e
C.
b, h, a, e, c, f, d, g
D.
a, b, e, f, d, c, g, h
-
Question 18:
If a bot is detected on your network, which of the following statements is correct regarding anti- bot blade.
A. outbound connections from the infected client are blocked to prevent further infection.
B. outbound connections from the infected client are blocked;, expect the connection to the Check Point ThreatCloud.
C. outbound connections from the infected client to the command and control center, are blocked.
D. outbound connections from every client are blocked, to prevent further data breaches.
-
Question 19:
Damage from a bot attack can take place after the bot compromises a machine. Which of the following represents the order by which this process takes place? The bot:
A. infects a machine, communicates with its command and control handlers, and penetrates the organization.
B. penetrates the organization, infects a machine, and communicates with its command and control handlers.
C. communicates with its command and control handlers, infects a machine, and penetrates the organization.
D. penetrates the organization, communicates with its command and control handlers, and infects a machine.
-
Question 20:
The Threat Prevention software blade:
A. Is configured in one unified policy for Anti-Bot and Anti-virus functions and uses the same threat repository.
B. Can only be deployed as part of SensorNET.
C. Is a free function that does not require additional licensing.
D. Can only be deployed on a Security Gateway running GAiA.
Related Exams:
156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-315
Check Point Security Administration NGX II (156-315.1)......156-315.1
Check Point Certified Security Expert NGX156-315.65
Check Point Certified Expert NGX R65156-315.75
Check Point Security Expert R75156-410.12
Check Point Certified Security Instructor156-510
VPN-1/FireWall-1 Management III156-706
CPCS - PointSec 6.1
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-727.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.