Exam Details
Exam Code
:156-915.77Exam Name
:Check Point Certified Security Expert UpdateCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:233 Q&AsLast Updated
:Mar 04, 2025
CheckPoint Checkpoint Certifications 156-915.77 Questions & Answers
-
Question 21:
If Jack was concerned about the number of log entries he would receive in the SmartReporter system, which policy would he need to modify?
A. Log Sequence Policy
B. Report Policy
C. Log Consolidator Policy
D. Consolidation Policy
-
Question 22:
Control connections between the Security Management Server and the Gateway are not encrypted by the VPN Community. How are these connections secured?
A. They are encrypted and authenticated using SIC.
B. They are not encrypted, but are authenticated by the Gateway
C. They are secured by PPTP
D. They are not secured.
-
Question 23:
If Bob wanted to create a Management High Availability configuration, what is the minimum number of Security Management servers required in order to achieve his goal?
A. Three
B. Two
C. Four
D. One
-
Question 24:
David wants to manage hundreds of gateways using a central management tool. What tool would David use to accomplish his goal?
A. Smart Provisioning
B. Smart Blade
C. Smart Dashboard
D. Smart LSM
-
Question 25:
From the following output of cphaprob state, which Cluster XL mode is this?
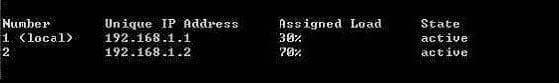
A. New mode
B. Multicast mode
C. Legacy mode
D. Unicast mode
-
Question 26:
Which of the following is NOT a feature of Cluster XL?
A. Enhanced throughput in all Cluster XL modes (2 gateway cluster compared with 1 gateway)
B. Transparent failover in case of device failures
C. Zero downtime for mission-critical environments with State Synchronization
D. Transparent upgrades
-
Question 27:
In which case is a Sticky Decision Function relevant?
A. Load Sharing - Unicast
B. Load Balancing - Forward
C. High Availability
D. Load Sharing - Multicast
-
Question 28:
You configure a Check Point QoS Rule Base with two rules: an HTTP rule with a weight of 40, and the Default Rule with a weight of 10. If the only traffic passing through your QoS Module is HTTP traffic, what percent of bandwidth will be allocated to the HTTP traffic?
A. 80%
B. 40%
C. 100%
D. 50%
-
Question 29:
You have pushed a policy to your firewall and you are not able to access the firewall. What command will allow you to remove the current policy from the machine?
A. fw purge policy
B. fw fetch policy
C. fw purge active
D. fw unload local
-
Question 30:
How do you verify the Check Point kernel running on a firewall?
A. fw ctl get kernel
B. fw ctl pstat
C. fw kernel
D. fw ver -k
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-915.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.