Exam Details
Exam Code
:156-915.77Exam Name
:Check Point Certified Security Expert UpdateCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:233 Q&AsLast Updated
:Mar 04, 2025
CheckPoint Checkpoint Certifications 156-915.77 Questions & Answers
-
Question 51:
Fill in the blanks. To view the number of concurrent connections going through core 0 on the firewall, you would use the command and syntax __ __ _ ___ __ ___________ __ .
A. fw –i 0 tab –t connections –s
-
Question 52:
You want VPN traffic to match packets from internal interfaces. You also want the traffic to exit the Security Gateway bound for all site-to-site VPN Communities, including Remote Access Communities. How should you configure the VPN match rule?
A. internal_clear > All_communities
B. Internal_clear > External_Clear
C. Communities > Communities
D. internal_clear > All_GwToGw
-
Question 53:
Fill in the blank. To save your OSPF configuration in GAiA, enter the command ___________ .
A. save config
-
Question 54:
Fill in the blank. To verify SecureXL statistics, you would use the command ________ .
A. fwaccel stats
-
Question 55:
Fill in the blank.
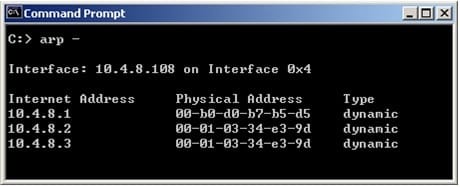
In Load Sharing Unicast mode, the internal cluster IP address is 10.4.8.3. The internal interfaces on two members are 10.4.8.1 and 10.4.8.2. Internal host 10.4.8.108 Pings 10.4.8.3, and receives replies. The following is the ARP table from the internal Windows host 10.4.8.108. Review the exhibit and type the IP address of the member serving as the pivot machine in the space below.
A. 10.4.8.2
-
Question 56:
Select the command set best used to verify proper failover function of a new ClusterXL configuration.
A. reboot
B. cphaprob -d failDevice -s problem -t 0 register / cphaprob -d failDevice unregister
C. clusterXL_admin down / clusterXL_admin up
D. cpstop/cpstart
-
Question 57:
Which three of the following are ClusterXL member requirements? 1) same operating systems 2) same Check Point version 3) same appliance model 4) same policy
A. 1, 3, and 4
B. 1, 2, and 4
C. 2, 3, and 4
D. 1, 2, and 3
-
Question 58:
Your organization maintains several IKE VPN's. Executives in your organization want to know which mechanism Security Gateway R77 uses to guarantee the authenticity and integrity of messages. Which technology should you explain to the executives?
A. Certificate Revocation Lists
B. Application Intelligence
C. Key-exchange protocols
D. Digital signatures
-
Question 59:
Match the VPN-related terms with their definitions. Each correct term is only used once. Exhibit:

A. A-3, B-4, C-1, D-5
B. A-4, B-3, C-5, D-2
C. A-2, B-5, C-4, D-1
D. A-3, B-2, C-1, D-4
-
Question 60:
Use the table to match the BEST Management High Availability synchronication-status descriptions for your Security Management Server (SMS).
Exhibit:
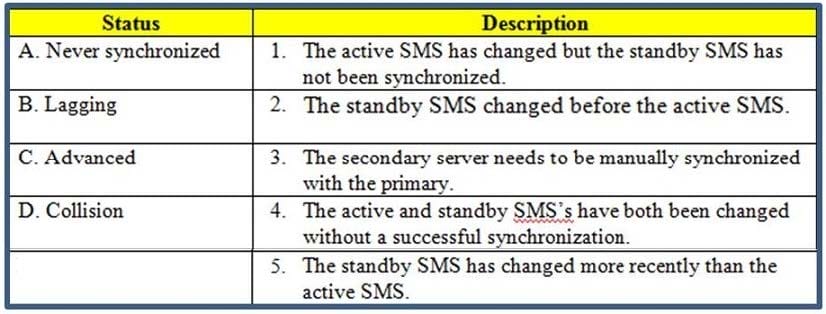
A. A-5, B-3, C-1, D-2
B. A-3, B-1, C-4, D-2
C. A-3, B-5, C-2, D-4
D. A-3, B-1, C-5, D-4
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-915.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.