Exam Details
Exam Code
:1Z0-460Exam Name
:Oracle Linux 6 Implementation EssentialsCertification
:Oracle CertificationsVendor
:OracleTotal Questions
:71 Q&AsLast Updated
:Jun 29, 2025
Oracle Oracle Certifications 1Z0-460 Questions & Answers
-
Question 61:
Identify the option with two files that are found in the /etc/sysconfig directory.
A. /etc/sysconfig/autofs and/etc/sysconfig/authconfig
B. /etc/sysconfig/ifcfg-eth0 and/etc/sysconfig/atd
C. /etc/sysconfig/resolv.conf and/etc/sysconfig/network
D. /etc/sysconfig/resolv.conf and/etc/sysconfig/grub.conf
-
Question 62:
DTrace is being ported from Solaris to Oracle Linux. Which three statements are true for the DTrace tool?
A. DTrace allows static and dynamic tracing of your applications and your kernel.
B. DTrace tool is used to compile debug kernel modules and device drivers
C. DTrace allows you to dynamically define probe points on the fly.
D. DTrace probes and probe points are usually defined by the user using scripts written in a language called D.
E. DTrace tool is based on the strace Linux tool and includes both user and kernel strace features.
-
Question 63:
On your Oracle Linux 6 system, you have to configure the eth0 network interface to 100 MB/sec, half duplex without trying to autonegotiate. Which command will help you configure this requirement?
A. # ifconfig eth0 speed 100 autoneg off duplex half
B. # ethtool interface eth0 speed 100 autoneg off duplex half
C. # ifconfig interface eth0 speed 100 autoneg off duplex half
D. # ethtool s eth0 speed 100 autoneg off duplex half
-
Question 64:
As user bob, you have logged in to the system on a terminal and issued the following command to make the top command run in the background.
[bob@host - ] topand
You exit from the terminal and log back as bob into the system at the same terminal. How is the background job affected?
A. The background job gets the foreground as soon as bob logs into the system.
B. The background job is suspended temporarily from the job and resumes when user bob logs back in to the system.
C. The background job starts running in the background again as soon as bob logs into the system.
D. The background job will not be affected.
E. The background job is deleted from the job pool and does not get listed using jobs command.
-
Question 65:
Which rpm command can be used to find the package that owns the /etc/rsyslog.conf file?
A. rpm query /etc/rsyslog.conf
B. rpm gf /etc/rsyslog.conf
C. rpm q1 /etc/rsyslog.conf
D. rpm q /etc/rsyslog.conf
-
Question 66:
View the exhibits.
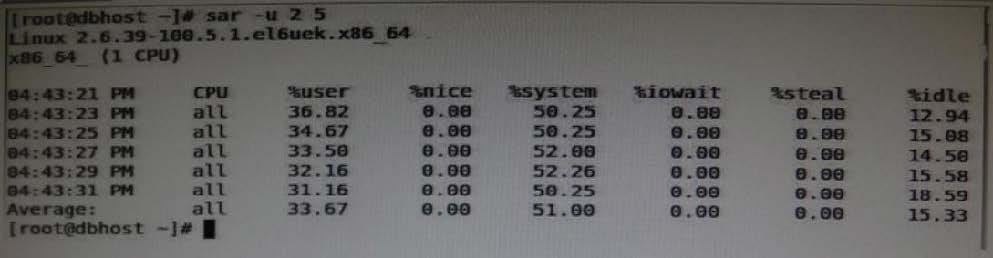
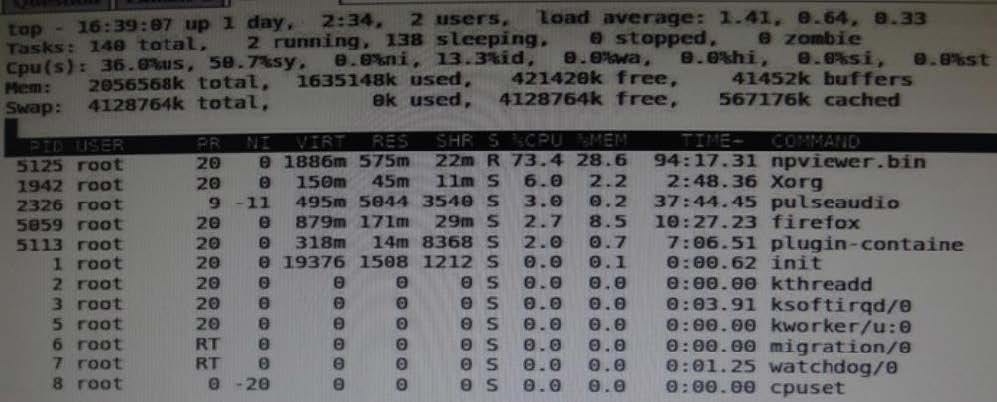
Examine the output of sar command and the top command in the Exhibits. Which statement is the correct interpretation of this data?
A. The system is running low on swap space and memory.
B. CPU is Idle and the system has plenty of free memory available.
C. The CPU utilization is high and one process is using most of the CPU.
D. The system is idle with very little memory, CPU, and I/O utilization.
-
Question 67:
Which three steps are involved in the installing Ksplice on servers that will be updated?
A. You have to be logged as user "ksplice" on the server you want to prepare and install Oracle Ksplice on.
B. The Uptrack package needs access directly or through a proxy to the Oracle public yum repository (http://public-yum.oracle.com/) to download the required packages for the uptrack-* utilities to be able to work correctly.
C. Download the install-uptrack script using the "wget N http://www.ksplice.com/uptrack/install-uptrack" command.
D. You have to be logged in as user "root" on the server you want to prepare and install Oracle ksplice on.
E. The uptrack package will set up a yum repository (/etc/yum.repos.d/ksplice-uptrack.repo) and download the required package for the uptrack-* utilities to be able to work correctly.
F. Download the ksplice ISO image from https://edelivery.oracle.com/linux and then run the "sh installuptrack" script from the ISO image.
-
Question 68:
What happens when the following command is run?
# authconfig - - passalgo = md5 - - update
A. It produces the MD5 checksum of the input data.
B. It configures the MD5 checksum for newly authored documents
C. It converts the stdio input to MD5 algorithm.
D. It changes the user password hashing algorithm to MD5.
-
Question 69:
Finding a directive issued by your organization listing several important CVEs (Common Vulnerability and Exposures), you find one for Linux OpenSSH (CVE-2006-5764), which might apply to your oracle Linux systems. What command would help ensure that a patch has been applied to close this vulnerability on an Oracle Linux 6 system running OpenSSH server?
A. yum listcves openssh
B. rpm qa | grep openssh | grep 5794
C. rpm q - - changelog openssh | grep 5794
D. yum sec list cves | grep 5794
E. yum sec list cvesApplied
-
Question 70:
Which three parameters of a network interface can you modify by using the NetworkManager tool on your Oracle Linux 6 system?
A. IPv4 settings
B. IPv6 settings
C. Netconsole settings
D. MTU settings
E. IP Proxy settings
Related Exams:
1Z0-020
Oracle8i: New Features for Administrators1Z0-023
Architecture and Administration1Z0-024
Performance Tuning1Z0-025
Backup and Recovery1Z0-026
Network Administration1Z0-034
Upgrade Oracle9i/10g OCA to Oracle Database OCP1Z0-036
Managing Oracle9i on Linux1Z0-041
Oracle Database 10g: DBA Assessment1Z0-052
Oracle Database 11g: Administration Workshop I1Z0-053
Oracle Database 11g: Administration II
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Oracle exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 1Z0-460 exam preparations and Oracle certification application, do not hesitate to visit our Vcedump.com to find your solutions here.