1Z0-821 Exam Details
-
Exam Code
:1Z0-821 -
Exam Name
:Oracle Solaris 11 System Administration -
Certification
:Oracle Certifications -
Vendor
:Oracle -
Total Questions
:243 Q&As -
Last Updated
:Jan 12, 2026
Oracle 1Z0-821 Online Questions & Answers
-
Question 1:
Select two statements that correctly describe the capabilities of the Distribution Constructor.
A. ISO images for use with the Automated Installer (AI) can be created.
B. Bootable USB images can be created for SPARC and x86 architectures.
C. A single installation server can be used to create ISO images for SPARC and x86 architectures.
D. Checkpoints can be used to pause the build, allowing scripts to run that modify the resulting ISO Image.
E. A single Installation server can be used to create ISO images for Solaris 10 and Solaris11 operating systems. -
Question 2:
You have a user that needs to use the cron tool to schedule some repetitive tasks. When the user enters the crontab command in a terminal window, the following error appears: crontab: you are not authorized to use cron. Sorry In order to troubleshoot this issue, in what directory would you start your invest
A. /etc/cron.d
B. /var/spool/cron
C. /var/spool/cron/crontable
D. /var/spool/cron/atjobs -
Question 3:
Which two options accurately describe the network characteristics of a zone?
A. DHCP address assignment cannot be configured in a shared IP zone.
B. Shared IP is the default type of network configuration.
C. Exclusive IP is the default type of network configuration.
D. By default, all IP addresses, netmasks, and routes are set by the global zone and cannot be altered in a non global zone.
E. IPMP cannot be managed within the non-global zone.
F. Commands such as snoop and dladm cannot be used on datalinks that are in use by a running zone. -
Question 4:
User1 is attempting to assist user2 with terminating user2's process 1234.
User1 entered the following: kill -9 1234
Why does the process continue to run?
A. You can kill a process only if you are root.
B. You can kill only a process that you own.
C. You can kill the process only with the pkill command.
D. You need to kill the process with a stronger kill signal. -
Question 5:
You are setting up an automated installer (AI) install server and issue the following command:
installadm create-service -n prod_ai -s /repo/prod_ai.iso \
-i 192.168.1.100 -c 5 -d /export/repo
Which four options describe the install server that you have configured?
A. The service name is prod_ai.
B. DHCP base IP address is 192.168.1.100
C. The initial IP address for the install clients will be 192.168.1.100. This IP address is temporary. After the client is booted, it will use IP addresses in the following range: 192.168.1.101-105.
D. Five IP addresses are allocated for DHCP clients, starting with 192.168.1.100.
E. The Install server will support up to five clients.
F. The AI net image ISO file is located in /repo/prod and the net image ISO will be unpacked in /export/repo.
G. The AI net image ISO file is located in /repo/repo and is named /repo/prod/_ai.iso. -
Question 6:
You upgraded your server to Oracle Solaris 11 and you imported zpool (pool1) that was created in Solaris 10. You need to create an encrypted ZFS file system in pool1, but first you need to make sure that your server supports ZFS encryption.
Which four statements are true for support of ZFS encryption?
A. The encrypted file system must have been created in Oracle Solaris11. To encrypt a ZFS file system from a previous version of Solaris, upgrade the zpool and create a new encrypted ZFS file system into the encrypted ZFS file system.
B. If you plan to create an encrypted file system in an existing zpool, the zpool must be upgraded to ZFS version 30.
C. ZFS encryption is integrated with the ZFS command set and no additional packages need to be installed.
D. ZFS encryption requires that the ZFS Dataset Encryption package be installed.
E. If you plan to create an encrypted file system in an existing zpool, the pool must be upgraded to ZFS version 21, minimum.
F. Encryption is supported at the pool or dataset (file system) level.
G. Encryption is supported at the pool level only for every file system in the pool will be encrypted.
H. You cannot create an encrypted file system in a zpool that was created prior to oracle Solaris11. Create a new zpool in Solaris11, create an encrypted ZFS file system in the new zpool, and move or copy the data from the existing file system into the new encrypted file system. -
Question 7:
Select two correct statements about the authentication services available in Oracle Solaris 11.
A. Pluggable Authentication Modules (PAM) is used to control the operation of services such console logins and ftp.
B. The Secure Shell can be configured to allow logins across a network to remote servers without transmitting passwords across the network.
C. Secure Remote Procedure Calls (Secure RPC) provides a mechanism to encrypt data on any IP Socket connection.
D. Pluggable Authentication Modules (PAM) is used to implement the Secure Shell in Oracle Solaris 11.
E. Simple Authentication and Security Layer (SASL) provides a mechanism to authenticate and encrypt access to local file system data. -
Question 8:
Review the storage pool information:
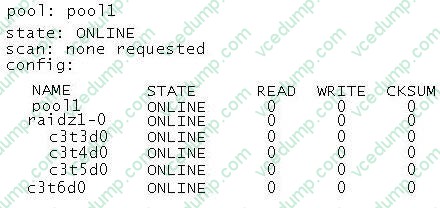
Which statement describes the status of this storage pool?
A. It is a RAIDZ storage pool and can withstand a single disk failure; data will be striped at: disk components.
B. It is a double-parity RAIDZ storage pool and can withstand two disk failures; data will be striped across four disk components.
C. It is an improperly configured RAIDZ storage pool; data will be striped across four disk components, but only three drives are protected with redundancy.
D. It is an improperly configured RAIDZ storage pool; data will be striped across three disk components, but only three drives are protected with redundancy. -
Question 9:
Before booting test zone a non-global zone, you want to connect to the zone's console so that you can watch the boot process.
Choose the command used to connect to testzone's console.
A. zoneadm -C testzone
B. zoneadm -console testzone
C. zlogin - z testzone console
D. zlogin - z testzone - C
E. zlogin -C testzone
F. zoneadm - testzone - c -
Question 10:
View the Exhibit to see the information taken from the installation log file.
Based on the information presented in the Exhibit, which two options describe the state of the system when the server is booted for the first time after the installation is complete?
A. NWAM will be used to configure the network interface.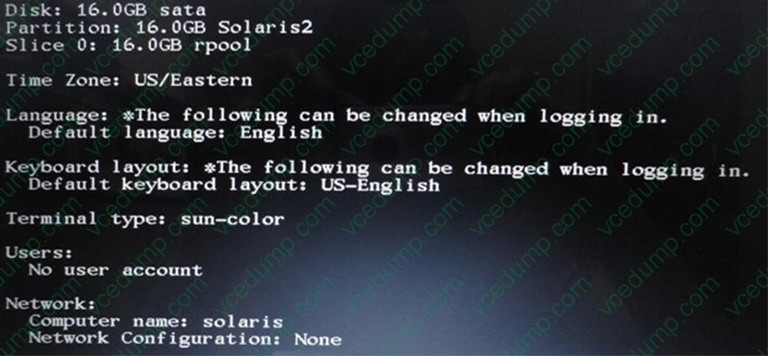
B. The network/physical service is offline.
C. You cannot log in from the console as root. You must first log in as a user and then su to root account.
D. The root user can log in from the console login.
E. You will be prompted to configure the network interface after the initial login.
Related Exams:
-
1Z0-020
Oracle8i: New Features for Administrators -
1Z0-023
Architecture and Administration -
1Z0-024
Performance Tuning -
1Z0-025
Backup and Recovery -
1Z0-026
Network Administration -
1Z0-034
Upgrade Oracle9i/10g OCA to Oracle Database OCP -
1Z0-036
Managing Oracle9i on Linux -
1Z0-041
Oracle Database 10g: DBA Assessment -
1Z0-052
Oracle Database 11g: Administration Workshop I -
1Z0-053
Oracle Database 11g: Administration II
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Oracle exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 1Z0-821 exam preparations and Oracle certification application, do not hesitate to visit our Vcedump.com to find your solutions here.