Exam Details
Exam Code
:1V0-81.20Exam Name
:Associate VMware SecurityCertification
:VMware CertificationsVendor
:VMwareTotal Questions
:54 Q&AsLast Updated
:Apr 08, 2025
VMware VMware Certifications 1V0-81.20 Questions & Answers
-
Question 41:
VMware's Intrinsic Security layer includes functionality for which control points?
A. networks, workloads, endpoints, identity, and clouds
B. applications, workloads, devices, identity, virtual infrastructure
C. networks, containers, devices, users, and VMware Cloud
D. applications, users, networks, data center perimeter, vSphere
-
Question 42:
Which three Workspace ONE UEM capabilities are used to configure security policies on Windows 10 desktops? (Choose three.)
A. Application Profiles
B. Custom XML
C. Custom Attributes
D. Baselines
E. Native Profiles
-
Question 43:
A technician has been asked to confirm a specific browser extension does not exist on any endpoint in their environment. Which is the VMware Carbon Black tool to use for this task?
A. Enterprise EDR
B. EDR
C. Audit and Remediation
D. Endpoint Standard
-
Question 44:
Which of the following is true about VMware Carbon Black Cloud Enterprise EDR watchlists?
A. They only update annually
B. You cannot customize them
C. They are made up of reports
D. Each watchlist is user specific
-
Question 45:
Which two are true about a VMware Service-defined Firewall? (Choose two.)
A. A firewall that allows you to use 3rd party features like IDS/IPS, threat protection, anti-bot, and anti-virus solutions
B. A firewall that blocks external access into your internal network based on IP services
C. A firewall that enforces policy for North-South traffic
D. A firewall that is auto scalable as new workloads are deployed
E. A firewall that provides East-West protection between internal applications
-
Question 46:
Which four alert filters are available in the VMware Carbon Black Cloud Investigate page? (Choose four.)
A. Watchlist
B. Target Value
C. Policy
D. Security Alert List
E. Effective Reputation
F. Alert Severity
-
Question 47:
Which is a common solution to implement for inbound network attacks?
A. Load Balancer
B. Firewall
C. Proxy
D. Reverse Proxy
-
Question 48:
Refer to the exhibit.
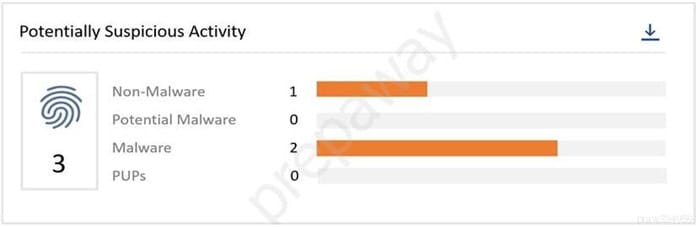
From the VMware Carbon Black Cloud console, what page do you go to after clicking the Non-Malware bar in the Potentially Suspicious Activity chart?
A. Notifications page with the selected alert filtered
B. Reputations page with the selected reputation filtered
C. Investigate page with the selected reputation filtered
D. Alerts page with the selected alert filtered
-
Question 49:
Refer to the exhibit.
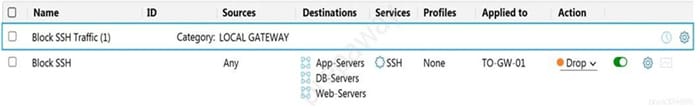
Which statement is true about the firewall rule?
A. It is a gateway firewall applied to a Tier-0 gateway that drops traffic on port 22
B. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that rejects traffic on port 22
C. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that drops traffic on port 22
D. It is a gateway firewall applied to a Tier-0 gateway that rejects traffic on port 22
-
Question 50:
Which three are industry best practices of Zero Trust framework? (Choose three.)
A. Employee machines need to have a passcode profile setup
B. Employee machines on Internal network are trusted and have access to all internal resources
C. Employee machines are checked for compliance before they get access to applications
D. Employees are not required to provide MFA to access internal resources over VPN
E. Employees get access to only the required resources to get their job done
Related Exams:
1V0-21.20
Associate VMware Data Center Virtualization1V0-31.21
Associate VMware Cloud Management and Automation1V0-41.20
Associate VMware Network Virtualization1V0-61.21
Associate VMware Digital Workspace1V0-71.21
Associate VMware Application Modernization1V0-81.20
Associate VMware Security2V0-21.20
Professional VMware vSphere 7.x2V0-21.23
VMware vSphere 8.x Professional2V0-31.21
Professional VMware vRealize Automation 8.32V0-31.23
VMware Aria Automation 8.10 Professional
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only VMware exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 1V0-81.20 exam preparations and VMware certification application, do not hesitate to visit our Vcedump.com to find your solutions here.