Exam Details
Exam Code
:1Z0-888Exam Name
:MySQL 5.7 Database AdministratorCertification
:Oracle CertificationsVendor
:OracleTotal Questions
:155 Q&AsLast Updated
:Mar 28, 2025
Oracle Oracle Certifications 1Z0-888 Questions & Answers
-
Question 121:
An admin attempts to enforce stronger security by using these commands: The admin then leaves the system running with the specified changes. What are two remaining security concerns? (Choose two.)
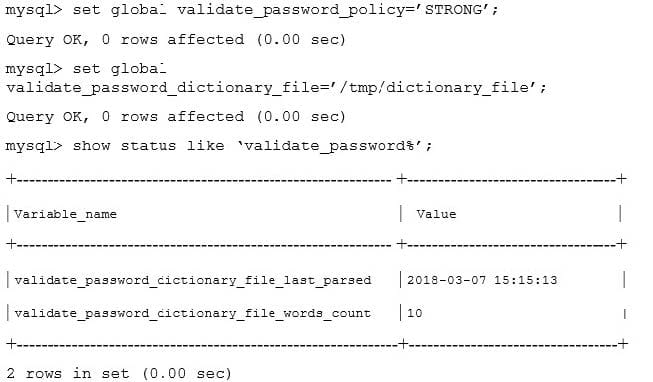
A. validate_password_policy cannot be set without restarting the MySQL instance.
B. The name of the dictionary file is too obvious.
C. The dictionary file word list is too short.
D. validate_password_dictionary_file cannot be set without restarting the MySQL instance.
E. The validate_password plug-in has not been loaded.
F. The dictionary file is an insecure location.
-
Question 122:
Which three tasks are handled by the optimizer? (Choose three.)
A. Decide which indexes to use.
B. Rewrite the WHERE clause.
C. Parse the query.
D. Change the order in which the tables are joined.
E. Validate the query.
F. Execute the query.
G. Verify that the user is allowed to execute the query.
-
Question 123:
A MySQL Server has been running an existing application successfully for six months. The my.cnf is adjusted to contain this additional configuration:
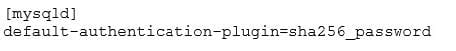
The MySQL Server is restarted without error.
What effect will the new configuration have on existing account?
A. They are not affected by this configuration change.
B. They all connect via the secure sha256_password algorithm without any configuration change.
C. They will have their passwords updated on start-up to sha256_password format.
D. They will have to change their password the next time they login to the server.
-
Question 124:
You are no longer able to log in to an existing MySQL Server because the root password credentials not working. You need to reset the root password to complete various administrative tasks. What are the two major methods that will achieve this? (Choose two.)
A. Start the MySQL Server in --safe-mode, which only loads the privilege system for changes as data is inaccessible.
B. Start the MySQL Server with reset-root-password in my.cnf, which will prompt you to enter a new root user password.
C. Start the MySQL Server with --init-file pointing to SQL that executes an ALTER USER statement to change the root user password.
D. Start the MySQL Server with --skip-grant-tables and execute SQL, which will update the root password.
E. Start the MySQL Server with 璱nitialize-insecure to force a password reset procedure on the command line.
-
Question 125:
These details are shown when logged in to an account: Which set of statements would match the accounts shown?
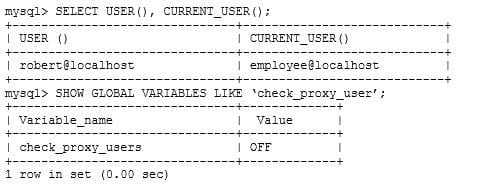
A. mysql> CREATE USER `employee'@'localhost' IDENTIFIED BY `more_secrets'; mysql> CREATE USER ''@'' IDENTIFIED BY `valid_password' WITH PROXY `employee'@'localhost';
B. mysql> CREATE USER `employee'@'localhost' IDENTIFIED BY `more_secrets'; mysql> GRANT PROXY ON `employee'@'localhost' TO `robert'@'localhost';
C. mysql> CREATE USER `robert'@'localhost' IDENTIFIED BY `secret_password'; mysql>CREATE USER `employee'@'localhost' IDENTIFIED BY `more_secrets';
D. mysql> CREATE_USER ''@'' IDENTIFIED WITH authentication_pam ACCOUNT LOCK; mysql> CREATE USER `employee'@'localhost' IDENTIFIED BY `more_secrets'; mysql> GRANT PROXY ON `employee'@'localhost' TO ''@'';
-
Question 126:
Host slave1 has ip address 192.0.2.10. Host slave2 has ip address 203.0.113.50
Examine these commands:
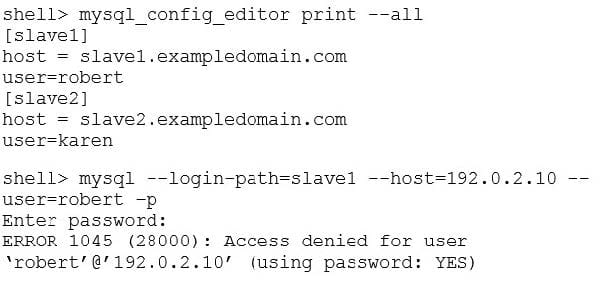
Why did this error occur?
A. The host on the command line is not defined in the login path.
B. The mysqld instance has not been restarted after creating the login path.
C. There is no password defined in the login path.
D. The DNS is not configured correctly for slave1 host.
E. The .mylogin.cnf file is not readable.
-
Question 127:
Which three options are most likely to be changed for production form their default values? (Choose three.)
A. innodb_buffer_pool_size
B. max_connections
C. join_buffer_size
D. character_set_system
E. innodb_log_file_size
F. max_user_connections
G. port
-
Question 128:
What is the order of tables shown in an EXPLAIN output?
A. It lists tables from the smallest to the largest.
B. It lists tables in the order in which their data will be read.
C. It lists tables from the most optimized to the least optimized.
D. It lists tables in the order in which they are specified in the statement that is being explained.
-
Question 129:
A master-slave replication setup has the slave showing this error:
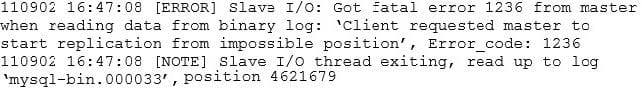
On the master server, the binary logs show:
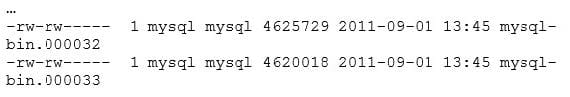
What could explain this error? (Choose two.)
A. binlog_cache_size=1024 is too small and transactions are lost.
B. binlog_format=STATEMENT and a non-deterministic query was executed.
C. enforce_gtid_consistency=ON and consistency is broken between the master and the slave.
D. The sync_relay_log=1000 setting on the slave is too small.
E. sync_binlog=0 and the master server crashed.
-
Question 130:
A MySQL replication slave is set up as follows:
Uses all InnoDB tables Receives ROW-based binary logs Has the read-only option
The replication slave has been found in an error state. You check the MySQL error log file and find these entries:
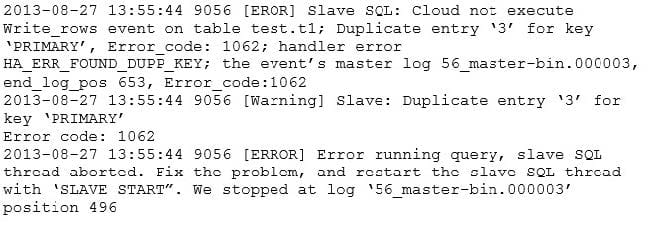
What are two possible causes for this error to occur? (Choose two.)
A. The applications have the SUPER privilege, which allows them to update rows.
B. The root user on the slave has executed FLUSH LOGS, causing the relay-log to doublewrite.
C. For tables with UNIQUE keys, statement-based replication must be used to maintain integrity.
D. The slave was created with mysqldump –u root –p --skip-lock-tables –all-databases > /data/data.sql
E. The slave user does not have INSERT, UPDATE, or DELETE permission and cannot execute the Write_rows function.
Related Exams:
1Z0-020
Oracle8i: New Features for Administrators1Z0-023
Architecture and Administration1Z0-024
Performance Tuning1Z0-025
Backup and Recovery1Z0-026
Network Administration1Z0-034
Upgrade Oracle9i/10g OCA to Oracle Database OCP1Z0-036
Managing Oracle9i on Linux1Z0-041
Oracle Database 10g: DBA Assessment1Z0-052
Oracle Database 11g: Administration Workshop I1Z0-053
Oracle Database 11g: Administration II
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Oracle exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 1Z0-888 exam preparations and Oracle certification application, do not hesitate to visit our Vcedump.com to find your solutions here.