Exam Details
Exam Code
:1Z0-888Exam Name
:MySQL 5.7 Database AdministratorCertification
:Oracle CertificationsVendor
:OracleTotal Questions
:155 Q&AsLast Updated
:Jul 08, 2025
Oracle Oracle Certifications 1Z0-888 Questions & Answers
-
Question 51:
You are remotely logged in to MySQL as the user "backup".
The account has temporarily been granted full privileges WITH GRANT to perform the actions required.
You want to change the password for the locally existing "backup" user.
Select the three commands which will perform the required action. (Choose three.)
A. SET PASSWORD FOR `backup'@'localhost' = `password';
B. SET PASSWORD = `password';
C. SET PASSWORD FOR `backup'@'localhost' = PASSWORD (`password')
D. ALTER USER USER() IDENTIFIED BY `password';
E. CREATE USER `backup'@'localhost' IDENTIFIED BY `password';
F. ALTER USER `backup' IDENTIFIED BY `password';
G. ALTER USER `backup'@'localhost' IDENTIFIED BY `password';
-
Question 52:
Which statement is correct about how InnoDB storage engine uses disk space?
A. It stores data in .MYD files and its index and undo information in the common tablespace.
B. It stores data in .MYD files, index information in .MYI files, and undo information the common tablespace.
C. It stores its data in tablespace file(s). Index and data dictionary details are stored in .FRM files.
D. It stores its data, index and undo information in .MYD and .MYI files.
E. It stores data, index and undo information in tablespace file(s).
-
Question 53:
Which statement is true about tablespaces?
A. All tablespace files must be in the directory specified by the –-datadir option.
B. General tablespaces can be configured to span multiple files.
C. All tables must be in either the system tablespace or a general tablespace.
D. The system tablespace can be configured to span multiple files.
-
Question 54:
Which MySQL utility copies the master instance to a slave instance on the same host?
A. mysqlfailover
B. mysqldbcopy
C. mysqlrplsync
D. mysqlserverclone
-
Question 55:
You have installed the validate_password plug-in and set the validate_password_policy variable. Which validation is affected by the validate_password_policy setting?
A. whether a new password is rejected if it contains a word found in a dictionary file.
B. whether a new password is rejected if it contains the current user's username.
C. the amount of delay after an incorrect password is entered
D. the length of time before a newly created password expires
-
Question 56:
Which two statements are true regarding MySQL security? (Choose two.)
A. The mysql user needs to have sudo privileges.
B. The mysqld process owner should own all files and directories to which the server writes.
C. The root or administrator users should own all files and directories to which the server writes.
D. The mysqld process should be run as root or administrator.
E. The mysqld process should not be run as root or administrator.
-
Question 57:
Which storage option for MySQL data directory typically offers the worst performance in a highly concurrent, OLTP-heavy, IO-bound workload?
A. battery-backed locally-attached RAID 5 array
B. iSCSI Lun
C. SAN (Fibre Channel) Lun
D. NFS (Networked File System) mount
-
Question 58:
You are asked to examine user accounts and find:
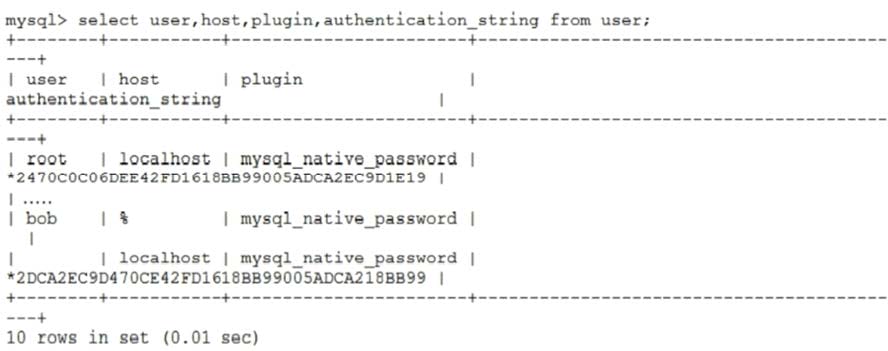
Which two statements will best secure this environment? (Choose two.)
A. DROP USER `'@'localhost';
B. ALTER USER `'@'localhost' PASSWORD = `secret_password';
C. ALTER USER bob@'%' IDENTIFIED BY `secret_password';
D. ALTER USER `root'@'localhost' ACCOUNT LOCK;
E. ALTER USER bob PASSWORD = `secret_password';
F. REVOKE ALL PRIVILEGES FROM `'@'localhost';
-
Question 59:
You are creating a strategy for backing up MySQL using a cold binary backup. The MySQL instance is a
replication master with global transaction identifiers (GTIDs) enabled and it uses Transparent Data
Encryption (TDE). Other than the configuration required to make the instance a replication master and
enabled GTIDs and TDE, the instance is using all default settings.
The requirements for the backup are:
It must be possible to rebuild the instance using the backup.
It must be verified.
It must allow for a catastrophic hardware failure.
Which four steps must be included in the backup strategy? (Choose four.)
A. Include the keyring data and/or configuration in the backup.
B. Restore the backup to a clean MySQL instance.
C. Copy the backup to a remote host.
D. Include the MySQL socket file in the backup.
E. Include the ibtmp1 file in the backup.
F. Include the relay logs in the backup.
G. Include the operating system disk encryption key in the backup.
H. Include the MySQL PID file in the backup.
I. Include the binary logs in the backup.
-
Question 60:
You have successfully provisioned the latest MySQL 5.7 database instance on a physical host, to be added to an existing farm for use in a modern, high volume, ACID-compliant, OLTP website, which serves hundreds of DML transactions per second.
The default values of which two key variables do you change to ensure seamless operation of the database? (Choose two.)
A. Key Buffer Size
B. InnoDB Redo Log Size
C. Binary Log Size
D. Buffer Pool Size
E. Sort Buffer size
F. Query Cache Size
Related Exams:
1Z0-020
Oracle8i: New Features for Administrators1Z0-023
Architecture and Administration1Z0-024
Performance Tuning1Z0-025
Backup and Recovery1Z0-026
Network Administration1Z0-034
Upgrade Oracle9i/10g OCA to Oracle Database OCP1Z0-036
Managing Oracle9i on Linux1Z0-041
Oracle Database 10g: DBA Assessment1Z0-052
Oracle Database 11g: Administration Workshop I1Z0-053
Oracle Database 11g: Administration II
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Oracle exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 1Z0-888 exam preparations and Oracle certification application, do not hesitate to visit our Vcedump.com to find your solutions here.