Exam Details
Exam Code
:1Z0-997-20Exam Name
:Oracle Cloud Infrastructure 2020 Architect ProfessionalCertification
:Oracle CertificationsVendor
:OracleTotal Questions
:165 Q&AsLast Updated
:
Oracle Oracle Certifications 1Z0-997-20 Questions & Answers
-
Question 91:
You developed a microservices-based application that runs on Oracle Cloud Infrastructure (OCI) Container Engine for Kubernetes (OKE). It has multiple endpoints that needs to be exposed to the public internet.
What is the most cost-effective way to expose multiple application endpoints without adding complexity to the application?
A. Use NodePort service type in Kubernetes for each of your service endpoint and use node's public IP address to access the applications.
B. Use separate load balancer instance for each service, but use the 100 Mbps load balancer option.
C. Deploy an Ingress Controller and use it to expose each endpoint with its own routing endpoint.
D. Use ClusterIP service type in Kubernetes for each of your service endpoint and use a load balancer to expose the endpoints.
-
Question 92:
Which of the below options is true regarding Oracle Cloud Infrastructure's load balancing service?
A. You can dynamically change the load balancer shape to handle more incoming traffic.
B. The public load balancer applies a floating public IP address to the primary load balancer.
C. When you create a private load balancer, the service requires 2 or more subnets to host both the primary and standby load balancers.
D. A public load balancer is Availability Domain specific in scope.
-
Question 93:
An E-commerce company which sells computers, tablets, and other electronics items has recently decided to move all of their on-premises infrastructure to Oracle Cloud Infrastructure (OCI). One of their on-premises application is running on an NGINX server and the Oracle Database is running in a 2 node Oracle Real Application Clusters (RAC) configuration.
They cannot afford to have any application down time when they do the migration.
What is an effective mechanism to migrate the customer application to OCI and set up regular automated backups?
A. Launch a compute instance and run an NGINX server to host the application. Deploy a 2 node VM DB Systems with Oracle RAC enabled. Import the on-premises database to OCI VM DB Systems using Oracle Data Pump and then enable automatic backups.
B. Launch a compute instance for both the NGINX application server and the database server. Attach block volumes on the database server compute instance and enable backup policy to backup the block volumes.
C. Launch a compute instance and run an NGINX server to host the application. Deploy Exadata Quarter Rack, enable automatic backups and import the database using Oracle Data Pump.
D. Launch a compute instance and run an NGINX server to host the application. Deploy a 2 node VM DB Systems with Oracle RAC enabled. Setup Oracle GoldenGate to synchronize data from their on-premises database to OCIVM Database. Export and Import the on- premises database to OCIVM DB Systems using Oracle Data Pump, apply the GoldenGate trail files to sync up the OCI database with the on-premises database. Enable automatic backups for the OCIVM database and then cutoverthe application from on-premises to OCI.
-
Question 94:
Your company developed a function that needs to access the Oracle Database to inject some data to it at runtime. You are tasked to move this function to the
Oracle Cloud Infrastructure (OCI) and use Oracle Functions and access Oracle Autonomous Database. You created a Dockerfile below to run this function, however, you are getting this error "cx_Oracle.DatabaseError: ORA""12560: TNS:protocol adapter error".
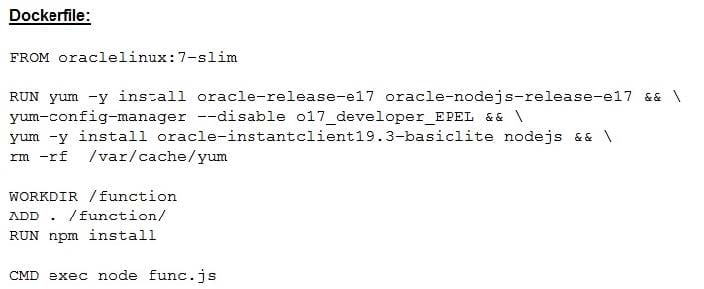
What should you do to make sure that Oracle Functions can run this Dockerfile properly? (Choose the best answer.)
A. Add these two lines to your Dockerfile: groupadd """"gid 1000 fn andand \ adduser """"uid 1000 """"gid fn fn
B. Use """"privileged flag while running the Docker container to add runtime privilege
C. Use """"cap""add=ALL flag while running the Docker container to add runtime capability
D. You ned to run this Container as root, so add this line: USER root
-
Question 95:
A manufacturing company is planning to migrate their on-premises database to OCI and has hired you for the migration. Customer has provided following information regarding their existing onpremises database:
Database version, host operating system and version, database character set, storage for data staging, acceptable length of system outage.
What additional information do you need from customer in order to recommend a suitable migration method? Choose two
A. Elapsed time since database was last patched
B. On-premises host operating system and version
C. Number of active connections
D. Data types used in the on-premises database
E. Top 5 longest running queries
-
Question 96:
You are the security architect for a medium sized e-commerce company that runs all of their applications in Oracle Cloud Infrastructure (OCI). Currently, there are 14 unique applications, each deployed and secured in their own compartment. The Operations team has procured a new monitoring tool that will be deployed throughout the OCI ecosystem. Their requirement is to deploy one management node into each compartment.
Currently, the Operations team Identity and Access Management (IAM) group has the following policy: allow group OpsTeam to READ all-resources in tenancy
Once the new monitoring nodes are deployed, the Operations team may need to stop, start, or reboot them occasionally.
What is the most efficient solution to allow the Operations team to fully manage the monitoring nodes, without allowing them to alter other resources across the tenancy?
A. In each of the 14 compartments, create a new policy with the following statement: allow group OpsTeam to manage instance-family in compartment XXX where XXX is the name of the compartment where you are creating the policy.
B. Create a new policy in the root compartment with the following policy statement: allow group OpsTeam to manage instance-family in tenancy where ANY (request.operation ?`UpdateInstance', request.operation ?`InstanceAction')
C. Tag all the monitoring nodes with the defined tag AllPolicy:AllowAccess:OpsTeam and write the following IAM policy: allow group OpsTeam to manage instance-family in tenancy where target.resource.tag.AllPolicy.AllowAccess ? `OpsTeam'
D. Tag all the monitoring nodes with the free-form tag AllowAccess:OpsTeam and write the following IAM policy: allow group OpsTeam to manage instance-family in tenancy where target.resource.tag.AllowAccess = `OpsTeam'
-
Question 97:
Your security team has informed you that there are a number of malicious requests for your web application coming from a set of IP addresses originating from a country in Europe.
Which of the following methods can be used to mitigate these type of unauthorized requests?
A. Web Application Firewall policy using access control rules
B. Deny rules in Virtual Cloud Network Security Group for the specific set of IP addresses.
C. Delete Internet Gateway from Virtual Cloud Network.
D. Deny rules in Virtual Cloud Network Security Lists for the specific set of IP addresses.
-
Question 98:
A digital marketing company is planning to host a website on Oracle Cloud Infrastructure (OCI) and leverage OCI Container Engine for Kubernetes (OKE). The web server will make API calls to access OCI Object Storage to store all images uploaded by users.
For security purposes, your manager instructed you to ensure that the credentials used by the web server to allow access not stored locally on the compute instance.
What solution results in an Implementation with the least effort for this scenario?
A. Configure the credentials using Instance Principal to allow the web server to make API calls to OCl Object Storage
B. Configure the credentials using OCI Registry (OC1R) which will automatically connect with OKE allowing the web server to make API calls to OCI Object Storage.
C. Configure the credentials to use Transparent Data Encryption (TDE) which will automatically allow the web server to make API calls to OCl Object Storage.
D. Configure the credentials using OCI Key Management to allow an instance to make API calls and grant access to OCl Object Storage.
-
Question 99:
You have created compartment called Dev for developers. There are two IAM groups for developers: group-devl and group-dev2. You need to write an Identity and Access Management (IAM) policy to give users in these groups access to manage all resources in the compartment Dev.
Which of the following IAM policy will accomplish this?
A. Allow any-user to manage all resources in compartment Dev where request.group= /group-dev*/
B. Allow group group-devl group-dev2 to manage all resources in compartment Dev
C. Allow group /group-dev*/ to manage all resources in compartment Dev
D. Allow any-user to manage all resources in tenancy where target.comparment= Dev
-
Question 100:
You are part of a project team working in the development environment created in OCI. You have realized that the CIDR block specified for one of the subnet in a VCN is not correct and want to delete the subnet. While deleting you are getting an error indicating that there are still resources that you must delete first. The error includes the OCID of the VNIC that is in the subnet.
Which of the following action you will take to troubleshoot this issue?
A. Use OCI CLI to call "GetVnic" operation to find out the parent resource of the VNIC
B. Copy and Paste OCID of the VNIC in the search box of the OCI Console to find out the parent resource of the VNIC
C. Use OCI CLI to delete the VNIC first and then delete the subnet
D. Use OCI CLI to delete the subnet using --force option
Related Exams:
1Z0-020
Oracle8i: New Features for Administrators1Z0-023
Architecture and Administration1Z0-024
Performance Tuning1Z0-025
Backup and Recovery1Z0-026
Network Administration1Z0-034
Upgrade Oracle9i/10g OCA to Oracle Database OCP1Z0-036
Managing Oracle9i on Linux1Z0-041
Oracle Database 10g: DBA Assessment1Z0-052
Oracle Database 11g: Administration Workshop I1Z0-053
Oracle Database 11g: Administration II
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Oracle exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 1Z0-997-20 exam preparations and Oracle certification application, do not hesitate to visit our Vcedump.com to find your solutions here.