Exam Details
Exam Code
:200-301Exam Name
:Implementing and Administering Cisco Solutions (CCNA) (Include Newest Simulation Labs)Certification
:CCNAVendor
:CiscoTotal Questions
:1605 Q&AsLast Updated
:Mar 27, 2025
Cisco CCNA 200-301 Questions & Answers
-
Question 11:
SIP-based Call Admission Control must be configured in the Cisco WLC GUI. SIP call-snooping ports are configured. Which two actions must be completed next? (Choose two.)
A. Set the QoS level to silver or greater for voice traffic.
B. Configure two different QoS roles for data and voice traffic.
C. Enable Media Session Snooping on the WLAN.
D. Set the QoS level to platinum for voice traffic.
E. Enable traffic shaping for the LAN interface of the WLC.
-
Question 12:
A network administrator plans an update to the WI-FI networks in multiple branch offices. Each location is configured with an SSID called “Office”. The administrator wants every user who connects to the SSID at any location to have the same access level. What must be set the same on each network to meet the requirement?
A. radio policy
B. profile name
C. NAS-ID configuration
D. security policies
-
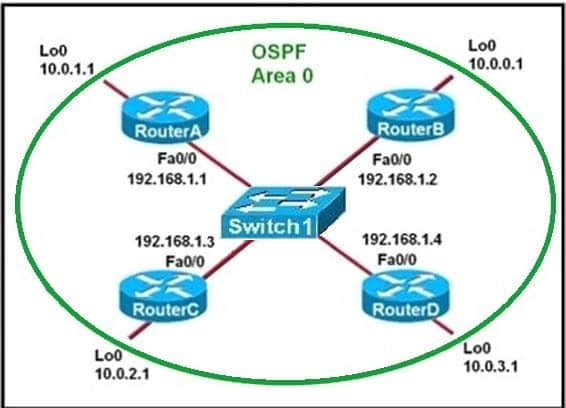
Question 13:
Refer to the exhibit.
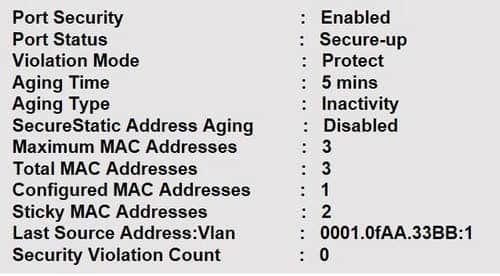
Host A switch interface is configured in VLAN 2. Host D sends a unicast packet destined for the IP address of host A.
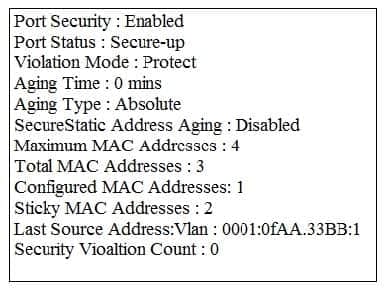
What does the switch do when it receives the frame from host D?
A. It floods the frame out of every ports except the source port.
B. It creates a broadcast storm.
C. It shuts down the source port and places it in err-disable mode.
D. It drops the frame from the MAC table of the switch.
-
Question 14:
Which two functions does a WLC perform in the lightweight access-point architecture that an AP performs independently in an autonomous architecture? (Choose two.)
A. managing RF channels, including transmission power
B. handling the association, authentication, and roaming of wireless clients
C. sending and processing beacon frames
D. encrypting and decrypting traffic that uses the WAP protocol family
E. preventing collisions between wireless clients on the same RF channel
-
Question 15:
Refer to the exhibit.
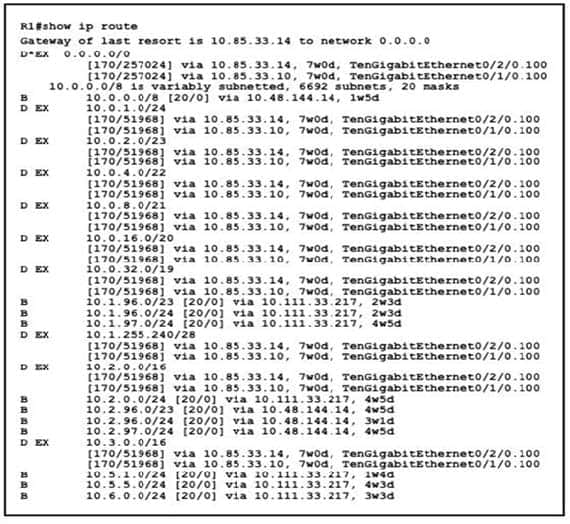
A network engineer is configuring a wireless LAN with Web Passthrough Layer 3 Web Policy. Which action must the engineer take to complete the configuration?
A. Set the Layer 2 Security to 802.1X.
B. Enable TKIP and CCMP256 WPA2 Encryption.
C. Enable the WPA Policy.
D. Set the Layer 2 Security to None.
-
Question 16:
Refer to the exhibit.
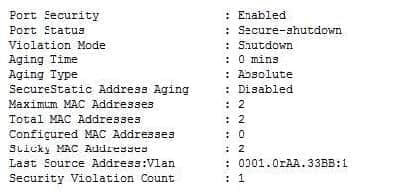
Which configuration enables an EtherChannel to form dynamically between SW1 and SW2 by using an industry-standard protocol, and to support full IP connectivity between all PCs?
A. SW1# interface Gi0/1 switchport switchport mode access channel-group 1 mode active ! interface Gi0/2 switchport switchport mode access channel-group 1 mode active
SW2#
interface Gi0/1
switchport
switchport mode access
channel-group 1 mode desirable
!
interface Gi0/2
switchport
switchport mode access
channel-group 1 mode desirable
B. SW1# interface Gi0/1 switchport switchport mode trunk channel-group 1 mode on ! interface Gi0/2 switchport switchport mode trunk channel-group 1 mode auto
SW2#
interface Gi0/1
switchport
switchport mode trunk
channel-group 1 mode auto
!
interface Gi0/2
switchport
switchport mode trunk
channel-group 1 mode on
interface port-channel 1
switchport
switchport mode trunk
C. SW1# interface Gi0/1 switchport switchport mode trunk channel-group 1 mode active ! interface Gi0/2 switchport switchport mode trunk channel-group 1 mode active
SW2#
interface Gi0/1
switchport
switchport mode trunk
channel-group 1 mode passive
!
interface Gi0/2
switchport
switchport mode trunk
channel-group 1 mode passive
D. SW1# interface Gi0/1 switchport switchport mode trunk channel-group 1 mode auto ! interface Gi0/2 switchport switchport mode trunk channel-group 1 mode auto
SW2#
interface Gi0/1
switchport
switchport mode trunk
channel-group 1 mode desirable
!
interface Gi0/2
switchport
switchport mode trunk
channel-group 1 mode desirable
-
Question 17:
A router received three destination prefixes: 10.0.0.0/8, 10.0.0.0/16, and 10.0.0.0/24. When the show ip route command is executed, which output does it return?
A. Gateway of last resort is 172.16.1.1 to network 0.0.0.0
o E2 10.0.0.0/8 [110/5] via 192.168.1.1, 0:01:00, Ethernet0
o E2 10.0.0.0/16[110/5] via 192.168.2.1, 0:01:00, Ethernet1
o E2 10.0.0.0/24[110/5] via 192.168.3.1, 0:01:00, Ethernet2
B. Gateway of last resort is 172.16.1.1 to network 0.0.0.0
o E2 10.0.0.0/8 [110/5] via 192.168.1.1, 0:01:00, Ethernet0
C. Gateway of last resort is 172.16.1.1 to network 0.0.0.0
o E2 10.0.0.0/24[110/5] via 192.168.3.1, 0:01:00, Ethernet2
D. Gateway of last resort is 172.16.1.1 to network 0.0.0.0
o E2 10.0.0.0/16[110/5] via 192.168.2.1, 0:01:00, Ethernet1
o E2 10.0.0.0/24[110/5] via 192.168.3.1, 0:01:00, Ethernet2
-
Question 18:
Refer to the exhibit.
User traffic originating within site B is failing to reach an application hosted on IP address 192.168.0.10, which is located within site A. What is determined by the routing table?
A. The traffic is blocked by an implicit deny in an ACL on router2.
B. The lack of a default route prevents delivery of the traffic.
C. The traffic to 192.168.0.10 requires a static route to be configured in router1.
D. The default gateway for site B is configured incorrectly.
-
Question 19:
When deploying a new network that includes both Cisco and third-party network devices, which redundancy protocol avoids the interruption of network traffic if the default gateway router fails?
A. VRRP
B. FHRP
C. GLBP
D. HSRP
-
Question 20:
What are two benefits of private IPv4 addressing? (Choose two.)
A. propagates routing information to WAN links
B. provides unlimited address ranges
C. reuses addresses at multiple sites
D. conserves globally unique address space
E. provides external internet network connectivity
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-301 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.