Exam Details
Exam Code
:200-901Exam Name
:Developing Applications and Automating Workflows using Cisco Platforms (DEVASC)Certification
:Cisco Certified DevNet AssociateVendor
:CiscoTotal Questions
:615 Q&AsLast Updated
:Apr 14, 2025
Cisco Cisco Certified DevNet Associate 200-901 Questions & Answers
-
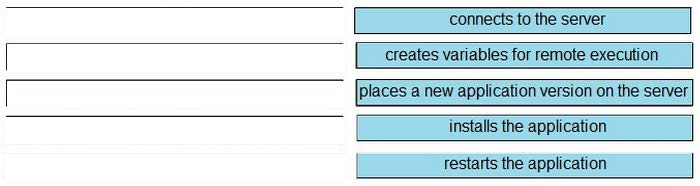
Question 171:
DRAG DROP
Refer to the exhibit.
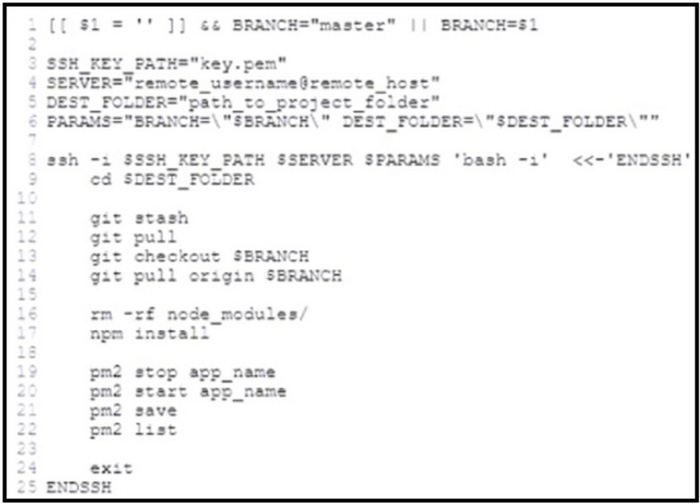
A developer is responsible for managing an application. The developer wants to deploy the new version of the application on the test environment whenever it is released. To automate this workflow, the developer writes a bash script. Drag and drop the deployment steps from the left into the order on the right to identify the workflow that is automated by the script.
Select and Place:
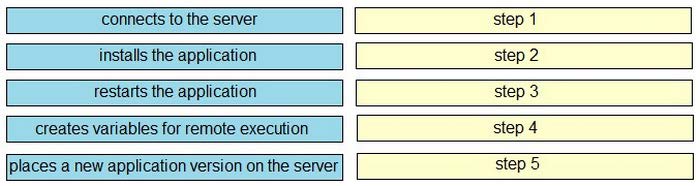
-
Question 172:
DRAG DROP
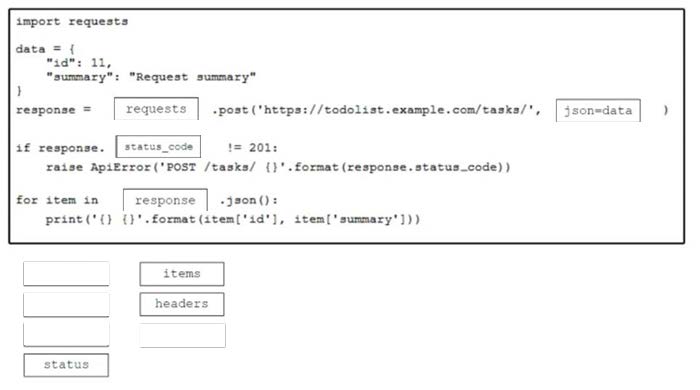
Drag and drop the code from the bottom onto the box where the code is missing to retrieve the RESTCONF running configuration for an interface named TwentyFiveGigabitEthernet 1/1/2. Not all options are used.
Select and Place:
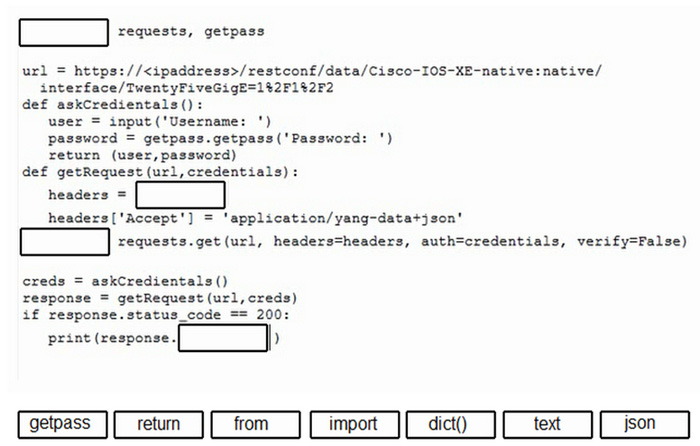
-
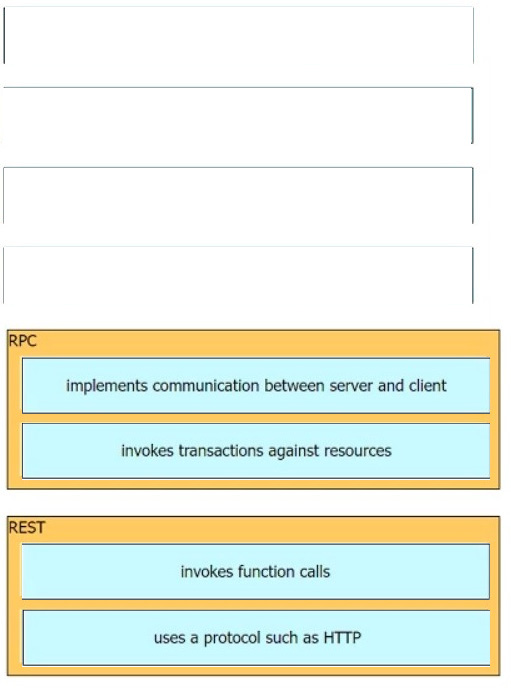
Question 173:
DRAG DROP
Drag and drop the API characteristics from the left onto the corresponding categories on the right.
Select and Place:
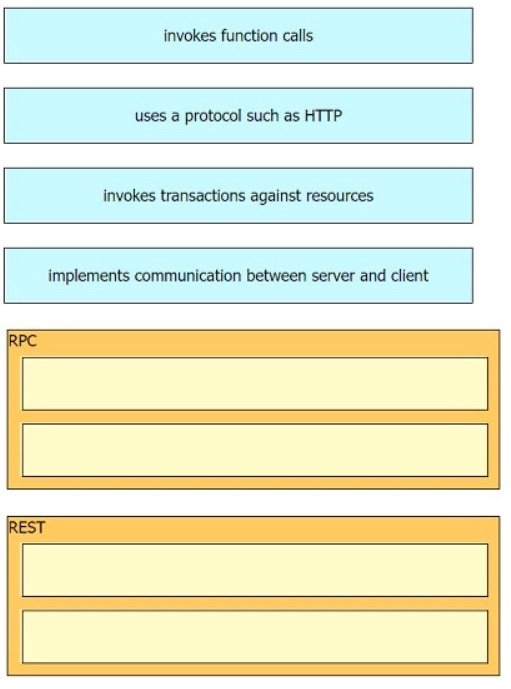
-
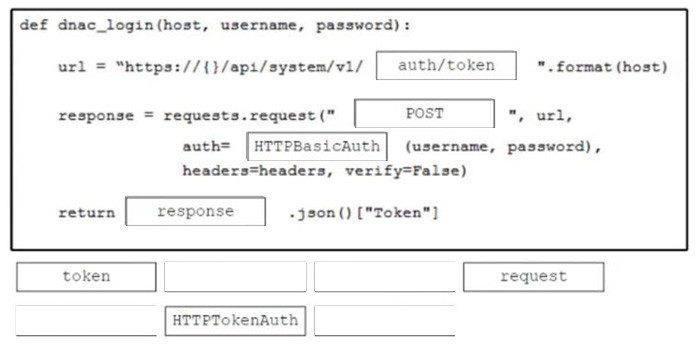
Question 174:
DRAG DROP
Drag and drop the code from the bottom onto the box where the code is missing to obtain an authorization token by using the Cisco DNA Center API. Not all options are used.
Select and Place:
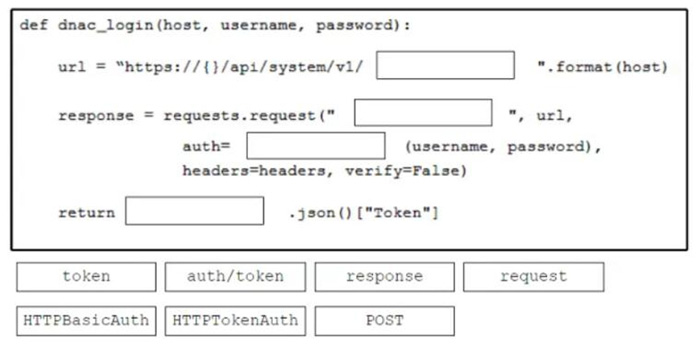
-
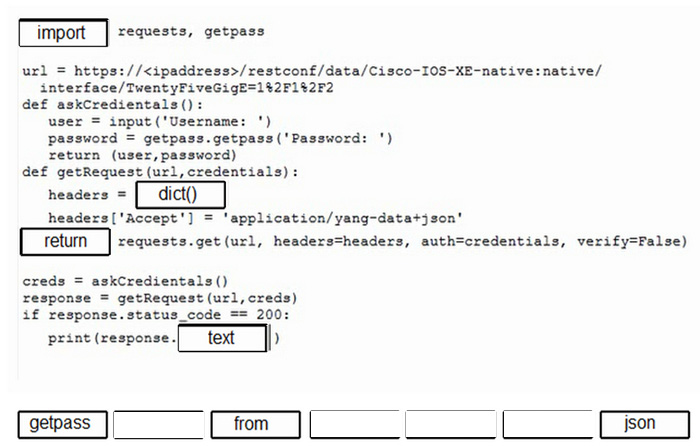
Question 175:
DRAG DROP
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
Select and Place:
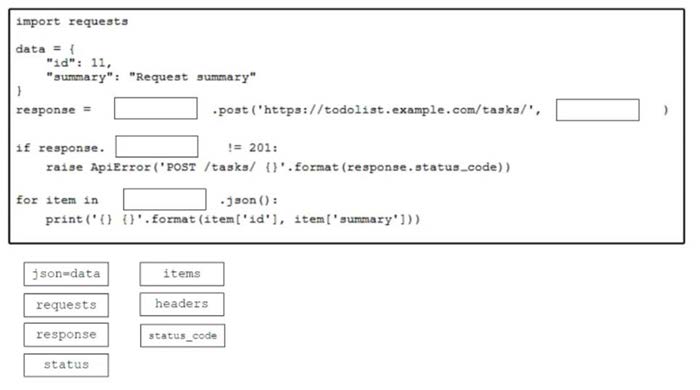
-
Question 176:
DRAG DROP
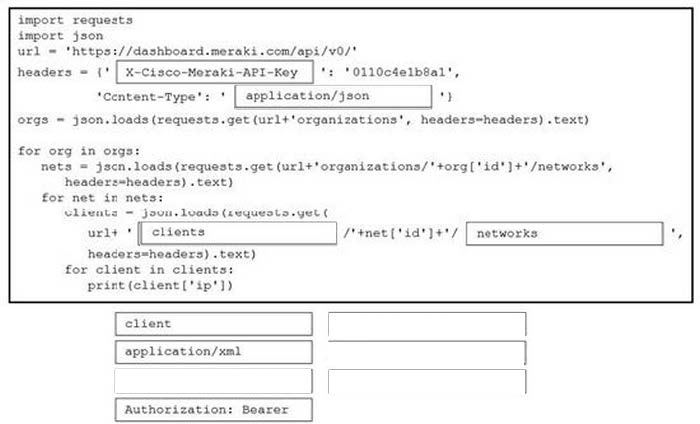
Drag and drop the code from the bottom onto the box where the code is missing in the Python script to complete a function to return all the clients on a network by using the Cisco Meraki Dashboard API. Not all options are used.
Select and Place:
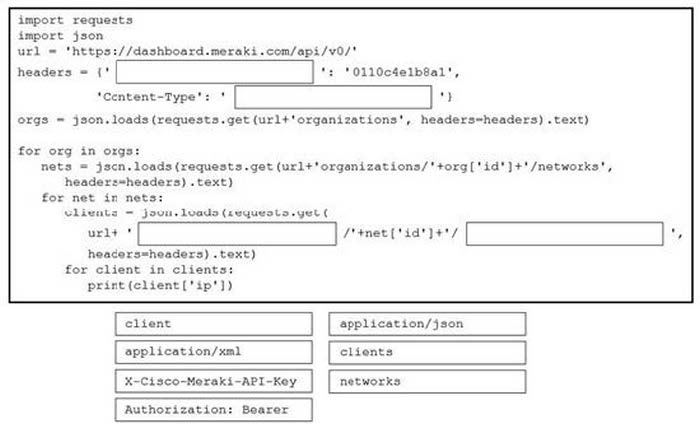
-
Question 177:
What is a characteristic of Waterfall compared to Agile software development method?
A. Waterfall focuses on continuous improvement, and Agile focuses on the design phase.
B. Waterfall separates the project development lifecycle into sprints, and Agile does not use cycles.
C. Waterfall specifies requirements before development begins, and Agile responds flexibly to changes in requirements.
D. Waterfall uses reviews with step by step approach, and Agile uses a serially phased approach.
-
Question 178:
Refer to the exhibit.

A developer is part of a team that is working on an open-source project in which source code is hosted in a public GitHub repository. While the application was built, security concerns were addressed by encrypting the credentials on the server. After a few months, the developer realized that a hacker managed to gain access to the account. The exhibit contains part of the source code for the login process. Why was the attacker able to access the developer's account?
A. The encoded credentials were available in the source code.
B. The application was not encrypting the communication with the server.
C. The credentials were encrypted in the source code.
D. An SSL certificate was used instead of the TLS protocol to authenticate.
-
Question 179:
Which technology is responsible for matching a name to an IP address of an application running on a host?
A. firewall
B. proxy
C. load balancer
D. DNS
-
Question 180:
Which network constraint causes the performance of the application to decrease as the number of users accessing the application increases?
A. latency
B. loss
C. bandwidth
D. jitter
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-901 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.