Exam Details
Exam Code
:200-901Exam Name
:Developing Applications and Automating Workflows using Cisco Platforms (DEVASC)Certification
:Cisco Certified DevNet AssociateVendor
:CiscoTotal Questions
:615 Q&AsLast Updated
:Apr 14, 2025
Cisco Cisco Certified DevNet Associate 200-901 Questions & Answers
-
Question 381:
Refer to the exhibit. An application must be deployed on a server that has other applications installed. The server resources are to be allocated based on the deployment requirements. The OS for each application must be independent. Which type of deployment is used?
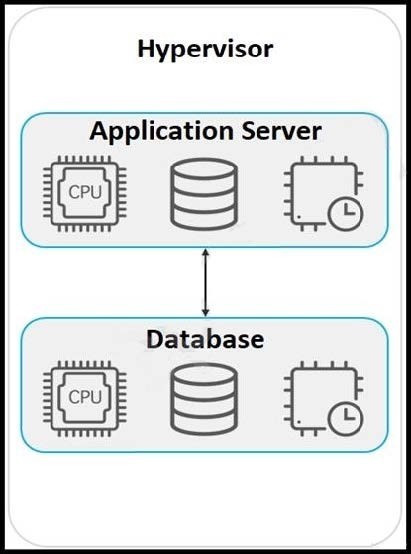
A. hybrid
B. virtual machines
C. containers
D. bare metal
-
Question 382:
What is a benefit of using a code review process in application development?
A. accelerates the deployment of new features in an existing application
B. provides version control during code development
C. enables the quick deployment of new code
D. eliminates common mistakes during development
-
Question 383:
Which OWASP threat takes advantage of a web application that the user has already authenticated to execute an attack?
A. phishing
B. DoS
C. brute force attack
D. CSRF
-
Question 384:
An engineer needs to retrieve a list of locally available Firepower Threat Defense upgrade packages by using the Firepower Management Center REST API. The engineer uses a GET request with the URL:
/api/fmc_platform/v1/updates/upgradepackages/f413afeb-e6f6-75f4-9169-6d9bd49s625e
What does "f413afeb-e6f6-75f4-9169-6d9bd49s625e" represent?
A. container UUID
B. package UUID
C. domain UUID
D. object UUID
-
Question 385:
Which HTTP error code series relates to redirection?
A. 400
B. 500
C. 200
D. 300
-
Question 386:
How are operations on REST APIs performed as compared to RPC APIs?
A. In a REST API, operations are performed on an object (node) that is identified by a URL, but RPC APIs are operation-oriented.
B. In a REST API, operations are performed on an external resource that is defined on the API, but the RCP APIs are resource-oriented.
C. In a REST API, operations are performed on a platform that is identified by the URL, but RPC APIs are platform-oriented.
D. In a REST API, operations are performed on an internal resource that is defined on the API, but RPC APIs are resource-oriented.
-
Question 387:
Which action do webhooks enable an application to perform?
A. Increase the request rate limit.
B. Populate the application with restricted data.
C. Receive real-time data.
D. Implement a push model.
-
Question 388:
Refer to the exhibit. A developer can access the TLS REST API on server A, but cannot access the API on server B. The developer can ping server B. When the developer performs a packet capture on the TLS REST API port on server B, the capture shows that the packet arrived and the server responded. What causes the issue?
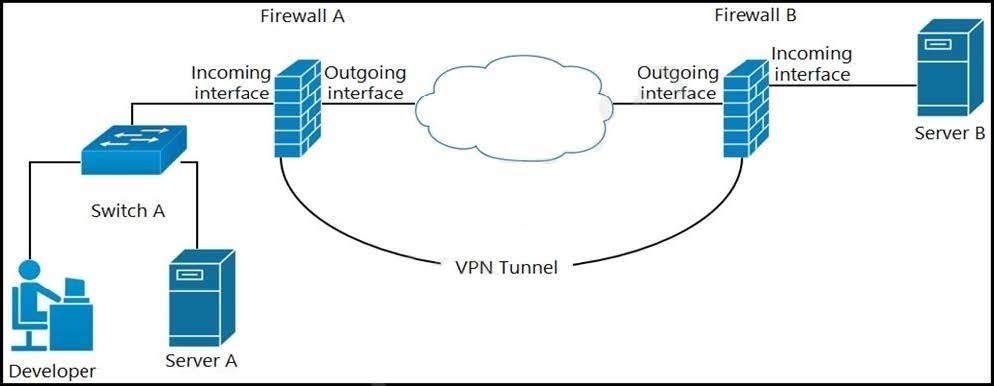
A. Port 80 is blocked on the outgoing interface of firewall B.
B. Port 443 is blocked on the outgoing interface of firewall A.
C. Port 443 is blocked on the incoming interface of firewall B.
D. Port 80 is blocked on the incoming interface of firewall A.
-
Question 389:
Refer to the exhibit. A network engineer wants use API update information about device interfaces. The network devices are deployed in a Cisco DevNet Sandbox and have running interfaces. Which value is suitable as the headers variable?
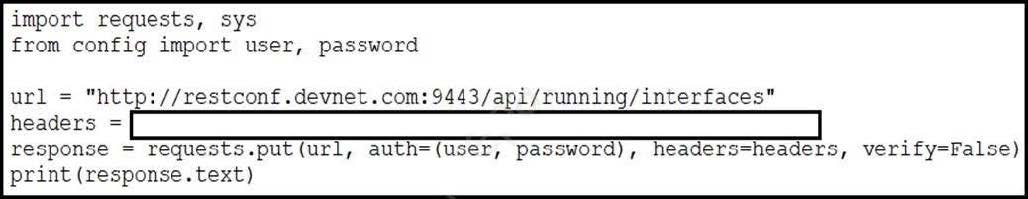
A. {'Content-Type': 'application/yang.data+yaml', 'Accept': 'application/yang.data+yaml'}
B. {'Content-Type': 'application/yang.data+json', 'Accept': 'application/yang.data+json'}
C. {'Content-Type': 'application/yang.data+utf8l', 'Accept': 'application/yang.data+utf8'}
D. {'Content-Type': 'application/restconf.data+txt', 'Accept': 'application/restconf.data+txt'}
-
Question 390:
A developer pushes an application to production. The application receives a webhook over HTTPS without a secret. The webhook information contains credentials to service in cleartext. When the information is received, it is stored in the database with an SHA-256 hash. Credentials to the database are accessed at runtime through the use of a vault service. While troubleshooting, the developer sets the logging to debug to view the message from the webhook. What is the security issue in this scenario?
A. Database credentials should be accessed by using environment variables defined at runtime.
B. During the transport of webhook messages, the credentials could be unencrypted and leaked.
C. During logging, debugging should be disabled for the webhook message.
D. Hashing the credentials in the database is not secure enough; the credentials should be encrypted.
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-901 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.