Exam Details
Exam Code
:202-450Exam Name
:LPIC-2 - Exam 202 - version 4.5Certification
:LPI CertificationsVendor
:LpiTotal Questions
:373 Q&AsLast Updated
:Apr 08, 2025
Lpi LPI Certifications 202-450 Questions & Answers
-
Question 181:
If the command arp -f is run, which file will be read by default?
A. /etc/hosts
B. /etc/ethers
C. /etc/arp.conf
D. /etc/networks
E. /var/cache/arp
-
Question 182:
According to the configuration below, what is the e-mail address of the administrator for this domain?
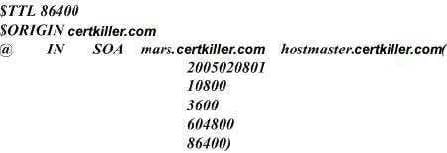
-
Question 183:
Which of the following is true, when a server uses PAM authentication and both /etc/pam.conf and /etc/pam.d/ exist?
A. It causes error messages.
B. /etc /pam.conf will be ignored.
C. /etc / pam.d/ will be ignored.
D. Both are used, but /etc/pam.d/ has a higher priority.
E. Both are used, but /etc/pam.conf has a higher priority.
-
Question 184:
Which site-specific configuration file for the shadow login suite must be modified to log login failures? Please enter the complete path to that file.
A. /etc/login.defs
-
Question 185:
You are not sure whether the kernel has detected a piece of hardware in your machine. What command, without options or parameters, should be run to present the contents of the kernel ringbuffer?
A. dmesg
-
Question 186:
A server is being used as a smurf amplifier, whereby it is responding to ICMP Echo- Request packets sent to its broadcast address. To disable this, which command needs to be run?
A. ifconfig eth0 nobroadcast
B. echo "0" > /proc/sys/net/ipv4/icmp_echo_accept_broadcasts
C. iptables -A INPUT -p icmp -j REJECT
D. echo "1" > /proc/sys/net/ipv4/icmp_echo_ignore_broadcasts
E. echo "1" > /proc/sys/net/ipv4/icmp_echo_nosmurf
-
Question 187:
The following is an excerpt from the output of tcpdump -nli eth1 'udp':
13:03:17.277327 IP 192.168.123.5.1065 > 192.168.5.112.53: 43653+ A? lpi.org. (25) 13:03:17.598624 IP 192.168.5.112.53 > 192.168.123.5.1065: 43653 1/0/0 A 24.215.7.109 (41) Which network service or protocol was used?
A. FTP
B. HTTP
C. SSH
D. DNS
E. DHCP
-
Question 188:
What is the correct format for an ftpusers file entry?
A. Use only one username on each line.
B. Add a colon after each username.
C. Add a semicolon after each username.
D. Add ALLOW after each username.
E. Add DENY after each username.
-
Question 189:
Which keys are stored in the authorized_keys file?
A. public
-
Question 190:
An SSH port-forwarded connection to the web server www.example.com was invoked using the command ssh -TL 80 :www.example.com:80 [email protected]. Which TWO of the following are correct?
A. The client can connect to the web server by typing http://www.example.com/ into the browser's address bar and the connection will be encrypted
B. The client can connect to www.example.com by typing http://localhost/ into the browser's address bar and the connection will be encrypted
C. The client can't connect to the web server by typing http://www.example.com/ into the browser's address bar. This is only possible using http://localhost/
D. It is only possible to port-forward connections to insecure services that provide an interactive shell (like telnet)
E. The client can connect to the web server by typing http://www.example.com/ into the browser's address bar and the connection will not be encrypted
Related Exams:
010-160
Linux Essentials, version 1.6101-400
LPI Level 1 Exam 101, Junior Level Linux Certification, Part 1 of 2101-500
LPIC-1 - Exam 101 - version 5.0102-400
LPI Level 1 Exam 102, Junior Level Linux Certification, Part 2 of 2102-500
LPIC-1 - Exam 102 - version 5.0201-450
LPIC-2 - Exam 201 - version 4.5202-450
LPIC-2 - Exam 202 - version 4.5305-300
LPIC-3 Virtualization and Containerization - Exam 305 - version 3.0701-100
DevOps Tools Engineer - Exam 701 - version 1.0
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Lpi exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 202-450 exam preparations and Lpi certification application, do not hesitate to visit our Vcedump.com to find your solutions here.