Exam Details
Exam Code
:202-450Exam Name
:LPIC-2 - Exam 202 - version 4.5Certification
:LPI CertificationsVendor
:LpiTotal Questions
:373 Q&AsLast Updated
:Mar 22, 2025
Lpi LPI Certifications 202-450 Questions & Answers
-
Question 331:
Which ACL type in Squid's configuration file is used for authentication purposes?
A. proxyAuth
B. proxy_auth
C. proxy_passwd
D. auth
E. auth_required
-
Question 332:
What is the name of the network security scanner project which, at the core, is a server with a set of network vulnerability tests (NVTs)?
A. nmap
B. OpenVAS
C. Snort
D. wireshark
-
Question 333:
The listing below is an excerpt from a Squid configuration filE.
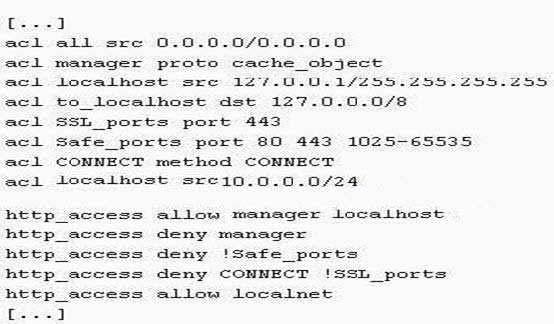
A. Users connecting from localhost will be able to access web sites through this proxy.
B. It's necessary to include a http_access rule denying access to all, at the end of the rules.
C. It's possible to use this proxy to access SSL enabled web sites listening on any port.
D. This proxy can't be used to access FTP servers listening on the default port.
E. This proxy is misconfigured and no user will be able to access web sites through it.
-
Question 334:
Which of the following organisations track and report on security related flaws in computer technology? (Please select TWO answers)
A. Bugtraq
B. CERT
C. CSIS
D. Freshmeat
E. Kernel.org
-
Question 335:
Considering the following kernel IP routing table now, which of the following commands must be remove the route to the network 10.10.1.0/24?
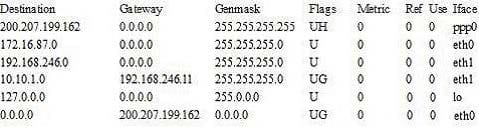
Kernel IP routing table
A. routedel 10.10.1.0
B. routedel 10.10.1.0/24
C. routedel -net 10.10.1.0/24
D. routedel 10.10.1.0/24 gw 192.168.246.11
E. routedel -net 10.10.1.0
-
Question 336:
To securely use dynamic DNS updates, the use of TSIG is recommended. Which TWO statements about TSIG are true?
A. TSIG is used for zone data encryption
B. TSIG is a signal to start a zone update
C. TSIG is used in zone files
D. TSIG is used only in server configuration
E. Servers using TSIG must be in sync (time zone!)
-
Question 337:
When Apache is configured to use name-based virtual hosts:
A. it's also necessary to configure a different IP address for each virtual host.
B. the Listen directive is ignored by the server.
C. it starts multiple daemons (one for each virtual host).
D. it's also necessary to create a VirtualHost block for the main host.
E. only the directives ServerName and DocumentRoot may be used inside a block.
-
Question 338:
In what mode is your FTP session when the client side makes the connections to both the data and command ports of the FTP server?
A. passive
B. active
C. impassive
D. safe
E. inactive
-
Question 339:
What is the name of the dovecot configuration variable that specifies the location of user mail?
A. mbox
B. mail_location
C. user_dir
D. maildir
E. user_mail_dir
-
Question 340:
How must Samba be configured, so that it can check passwords against the ones in /etc/passwd and / etc/shadow?
A. Set the parameters "encrypt passwords = yes" and "password file = /etc/passwd".
B. Set the parameters "encrypt passwords = yes", "password file = /etc/passwd" and "password algorithm =crypt"
C. Delete the smbpasswd file and create a symbolic link to the passwd and shadow file
D. It is not possible for Samba to use/etc/passwd and /etc/shadow
E. Run smbpasswd to convert /etc/passwd and /etc/shadow to a Samba pass word file
Related Exams:
010-160
Linux Essentials, version 1.6101-400
LPI Level 1 Exam 101, Junior Level Linux Certification, Part 1 of 2101-500
LPIC-1 - Exam 101 - version 5.0102-400
LPI Level 1 Exam 102, Junior Level Linux Certification, Part 2 of 2102-500
LPIC-1 - Exam 102 - version 5.0201-450
LPIC-2 - Exam 201 - version 4.5202-450
LPIC-2 - Exam 202 - version 4.5305-300
LPIC-3 Virtualization and Containerization - Exam 305 - version 3.0701-100
DevOps Tools Engineer - Exam 701 - version 1.0
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Lpi exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 202-450 exam preparations and Lpi certification application, do not hesitate to visit our Vcedump.com to find your solutions here.