Exam Details
Exam Code
:250-428Exam Name
:Administration of Symantec Endpoint Protection 14Certification
:Symantec CertificationsVendor
:SymantecTotal Questions
:165 Q&AsLast Updated
:Apr 12, 2025
Symantec Symantec Certifications 250-428 Questions & Answers
-
Question 61:
What are two criteria that Symantec Insight uses to evaluate binary executables? (Select two.)
A. sensitivity
B. prevalence
C. confidentiality
D. content
E. age
-
Question 62:
An administrator uses the search criteria displayed in the image below. Which results ore returned from the query?
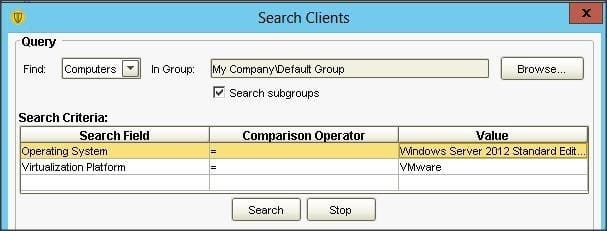
A. Only VMware Servers in the Default Group
B. All Windows 2012 Servers in the Default Group
C. Only Windows 2012 Servers that are Virtualized in the Default Group
D. All Windows 2012 Servers and all Virtualized Servers in the Default Group
-
Question 63:
Which two are policy types within the Symantec Endpoint Protection Manager? (Select two.)
A. Exceptions
B. Host Protection
C. Shared Insight
D. Intrusion Prevention
E. Process Control
-
Question 64:
Which two options are supported Symantec Endpoint Manager authentication types? (Select two.)
A. Microsoft Active Directory
B. MS-CHAP
C. RSA SecurID
D. Biometrics
E. Network Access Control
-
Question 65:
Users report abnormal behavior on systems where Symantec Endpoint Protection is installed.
Which tool can an administrator run on the problematic systems to identify the likely cause of the abnormal behavior?
A. smc.exe -stop
B. SymHelp.exe
C. PowerShell.exe
D. CleanWipe.exe
-
Question 66:
An administrator changes the Virus and Spyware Protection policy for a specific group that disables Auto-Protect. The administrator assigns the policy and the client systems applies the corresponding policy serial number. Upon visual inspection of a physical client system, the policy serial number is correct. However, Auto-Protect is still enabled on the client system.
Which action should the administrator take to ensure that the desired setting is in place on the client?
A. Restart the client system
B. Run a command on the computer to Update Content
C. Enable the padlock next to the setting in the policy
D. Withdraw the Virus and Spyware Protection policy
-
Question 67:
A company allows users to create firewall rules. During the course of business, users are accidentally adding rules that block a custom internal application. Which steps should the Symantec Endpoint Protection administrator take to prevent users from blocking the custom application?
A. Create an Allow All Firewall rule for the fingerprint of the file and place it at the bottom of the firewall rules above the blue line
B. Create an Allow firewall rule for the application and place it at the bottom of the firewall rules below the blue line
C. Create an Allow for the network adapter type used by the application and place it at the top of the firewall rules below the blue line.
D. Create an Allow Firewall rule for the application and place it at the top of the firewall rules above the blue line.
-
Question 68:
An administrator reports that the Home, Monitors, and Report pages are absent in the Symantec Endpoint Protection Management console when the administrator logs on. Which action should the administrator perform to correct the problem?
A. configure proxy settings for each server in the site
B. configure External Logging to Enable Transmission of Logs to a Syslog Server
C. grant the Administrator Full Access to Root group of the organization
D. grant View Reports permission to the administrator
-
Question 69:
Which tool should an administrator use to discover and deploy the Symantec Endpoint Protection client to new computers?
A. Unmanaged Detector
B. Client Deployment Wizard
C. Communication Update Package Deployment
D. Symantec Endpoint Discovery Tool
-
Question 70:
In which two areas can host groups be used? (Select two.)
A. Locations
B. Download Insight
C. IPS
D. Application and Device Control
E. Firewall
Related Exams:
250-428
Administration of Symantec Endpoint Protection 14250-438
Administration of Symantec Data Loss Prevention 15250-440
Administration of Symantec PacketShaper 11.9.1250-441
Administration of Symantec Advanced Threat Protection 3.0250-445
Administration of Symantec Email Security.cloud (v1)250-447
Administration of Symantec Client Management Suite 8.5250-513
Administration of Symantec Data Loss Prevention 12250-556
Administration of Symantec ProxySG 6.7250-561
Endpoint Security Complete - Administration R1250-580
Endpoint Security Complete - R2 Technical Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 250-428 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.