Exam Details
Exam Code
:250-438Exam Name
:Administration of Symantec Data Loss Prevention 15Certification
:Symantec CertificationsVendor
:SymantecTotal Questions
:70 Q&AsLast Updated
:Mar 06, 2025
Symantec Symantec Certifications 250-438 Questions & Answers
-
Question 61:
What are two reasons an administrator should utilize a manual configuration to determine the endpoint location? (Choose two.)
A. To specify Wi-Fi SSID names
B. To specify an IP address or range
C. To specify the endpoint server
D. To specify domain names
E. To specify network card status (ON/OFF)
-
Question 62:
How should a DLP administrator exclude a custom endpoint application named "custom_app.exe" from being monitoring by Application File Access Control?
A. Add "custom_app.exe" to the "Application Whitelist" on all Endpoint servers.
B. Add "custom_app.exe" Application Monitoring Configuration and de-select all its channel options.
C. Add "custom_app_.exe" as a filename exception to the Endpoint Prevent policy.
D. Add "custom_app.exe" to the "Program Exclusion List" in the agent configuration settings.
-
Question 63:
A software company wants to protect its source code, including new source code created between scheduled indexing runs. Which detection method should the company use to meet this requirement?
A. Exact Data Matching (EDM)
B. Described Content Matching (DCM)
C. Vector Machine Learning (VML)
D. Indexed Document Matching (IDM)
-
Question 64:
A DLP administrator has enabled and successfully tested custom attribute lookups for incident data based on the Active Directory LDAP plugin. The Chief Information Security Officer (CISO) has attempted to generate a User Risk Summary report, but the report is empty. The DLP administrator confirms the Cisco's role has the "User Reporting" privilege enabled, but User Risk reporting is still not working.
What is the probable reason that the User Risk Summary report is blank?
A. Only DLP administrators are permitted to access and view data for high risk users.
B. The Enforce server has insufficient permissions for importing user attributes.
C. User attribute data must be configured separately from incident data attributes.
D. User attributes have been incorrectly mapped to Active Directory accounts.
-
Question 65:
Which two Infrastructure-as-a-Service providers are supported for hosting Cloud Prevent for Office 365? (Choose two.)
A. Any customer-hosted private cloud
B. Amazon Web Services
C. ATandT
D. Verizon
E. Rackspace
-
Question 66:
Under the "System Overview" in the Enforce management console, the status of a Network Monitor detection server is shown as "Running Selected." The Network Monitor server's event logs indicate that the packet capture and filereader processes are crashing.
What is a possible cause for the Network Monitor server being in this state?
A. There is insufficient disk space on the Network Monitor server.
B. The Network Monitor server's certificate is corrupt or missing.
C. The Network Monitor server's license file has expired.
D. The Enforce and Network Monitor servers are running different versions of DLP.
-
Question 67:
How should a DLP administrator change a policy so that it retains the original file when an endpoint incident has detected a "copy to USB device" operation?
A. Add a "Limit Incident Data Retention" response rule with "Retain Original Message" option selected.
B. Modify the agent config.db to include the file
C. Modify the "Endpoint_Retain_Files.int" setting in the Endpoint server configuration
D. Modify the agent configuration and select the option "Retain Original Files"
-
Question 68:
What is the correct configuration for "BoxMonitor.Channels" that will allow the server to start as a Network Monitor server?
A. Packet Capture, Span Port
B. Packet Capture, Network Tap
C. Packet Capture, Copy Rule
D. Packet capture, Network Monitor
-
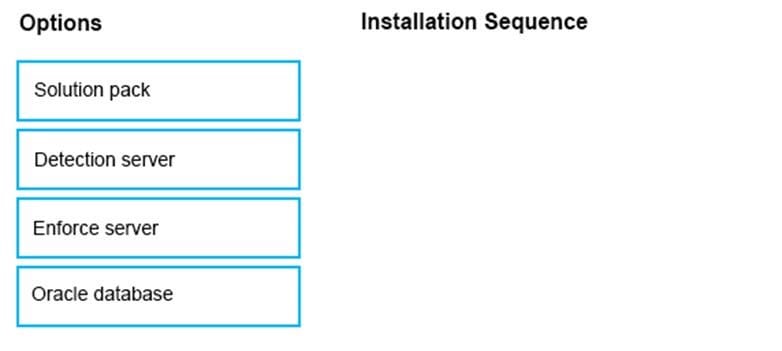
Question 69:
DRAG DROP
What is the correct installation sequence for the components shown here, according to the Symantec Installation Guide?
Place the options in the correct installation sequence.
Select and Place:
-
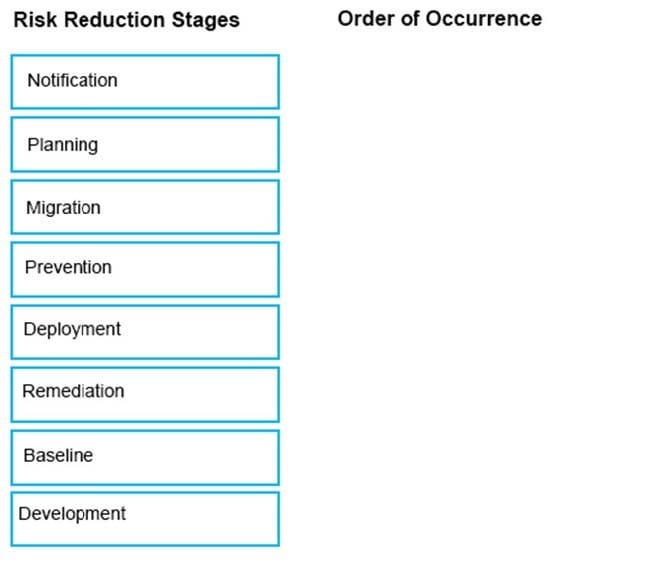
Question 70:
DRAG DROP
The Symantec Data Loss risk reduction approach has six stages.
Drag and drop the six correct risk reduction stages in the proper order of Occurrence column.
Select and Place:
Related Exams:
250-428
Administration of Symantec Endpoint Protection 14250-438
Administration of Symantec Data Loss Prevention 15250-440
Administration of Symantec PacketShaper 11.9.1250-441
Administration of Symantec Advanced Threat Protection 3.0250-445
Administration of Symantec Email Security.cloud (v1)250-447
Administration of Symantec Client Management Suite 8.5250-513
Administration of Symantec Data Loss Prevention 12250-556
Administration of Symantec ProxySG 6.7250-561
Endpoint Security Complete - Administration R1250-580
Endpoint Security Complete - R2 Technical Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 250-438 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.