Exam Details
Exam Code
:300-620Exam Name
:Implementing Cisco Application Centric Infrastructure (DCACI)Certification
:CCNP Data CenterVendor
:CiscoTotal Questions
:309 Q&AsLast Updated
:Mar 20, 2025
Cisco CCNP Data Center 300-620 Questions & Answers
-
Question 1:
Refer to the exhibit.
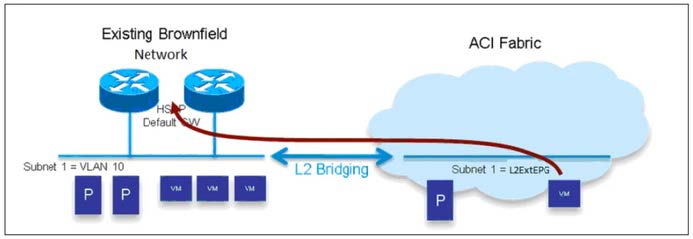
An engineer must migrate workloads from the brownfield network to the Cisco ACI fabric. The VLAN 10 default gateway remains in the router located in the brownfield network. The bridge domain has already been associated with L2Out. Which two actions must be taken to migrate the workloads? (Choose two.)
A. Enable ARP Flooding.
B. Configure Multi-Destination Flooding Flood in Encapsulation.
C. Select limit IP learning to Subnet.
D. Set L2 Unknown Unicast Flood.
E. Map the MAC address of the default gateway to the bridge domain.
-
Question 2:
An engineer is configuring a new user account in Cisco ACI. The new user will be assigned the role of fabric administrator. The fabric has only one tenant, so the engineer associated the new user account with a security domain for the tenant, as well as the security domain for the management tenant.
Which configuration permits the new user with admin access to the fabric?
A. Associate the new user with the security domain all.
B. Grant the new user R/W access to the user and management tenant.
C. Add the DN uni/fabric under explicit rules.
D. Bind the security domain infra to the new user account.
-
Question 3:
An engineer must integrate a Cisco ACI fabric with VMware and discover an ESXi host using LLDP. Two EPGs have been created and associated with the VMM domain. The engineer must configure the ACI such that contracts are pushed to the ACI leaf switches when the VM is mapped to EPG and the contracts are removed when LLDP is disabled.
Which configuration must be selected to meet these requirements?
A. Deployment immediacy: On-Demand
B. Resolution immediacy: On-Demand
C. Deployment immediacy: Immediate
D. Resolution immediacy: Immediate
-
Question 4:
An engineer must implement user activity tracking in the Cisco ACI with a solution that meets these requirements:
1.
All user activity that is related to the Cisco ACI infrastructure hardware must be tracked.
2.
All audit logs with severity level 5 and below must be collected and exported.
3.
Logs must be exported to a Security Information and Event Management (SIEM) appliance.
Which set of steps must be taken?
A. Create a Syslog Monitoring Destination Group with a remote destination of the SIEM device. Create a Tenant-level Syslog Source under the Monitoring section of the Tenant Tab. Select Audit Logs and a severity level of Warning,
B. Create a Syslog Monitoring Destination Group with a Local File destination. Create an Access-level Syslog Source under the Monitoring section of the Fabric Tab. Select Fault Logs and a severity level of Notification.
C. Create a Syslog Monitoring Destination Group with a remote destination of the SIEM device. Create a Fabric-level Syslog Source under the Monitoring section of the Fabric Tab. Select Audit Logs and a severity level of Notification.
D. Create a Syslog Monitoring Destination Group with Console Destination. Create a System-level Syslog Source under the Monitoring section of the System Tab. Select Session Logs and a severity level of Warning.
-
Question 5:
A network engineer is implementing a Layer 3 Out in the Cisco ACI fabric. The data center core switches must connect to a pair of leaf switches and exchange routes via a routing protocol. In addition, the implementation must meet these criteria:
1.
The external switch interface must use 802.1Q tagging.
2.
Access to the Internet for the ACI fabric must be the L3Out.
3.
The L3Out must use a routing protocol that has rapid convergence time and low CPU usage.
Which configuration set meets these requirements?
A. Configure the OSPF Protocol policy with an area of 0. Set up the Routed External Network object and Node Profile and select OSPF. Create the Switch profile and select VPC with the appropriate interfaces. Create the default network and associate it with the Routed Outside object.
B. Configure the BGP Protocol policy with the appropriate Autonomous System number.
Configure an Interface policy and an External Bridged Domain.
Create an External Bridged Network and use the configured VLAN pool.
Build the Leaf profile and select the Routed sub-interface with the appropriate VLAN.
C. Implement the IS-IS Protocol policy with the selected Autonomous System number. Create the Routed Outside object and Node Profile and select IS-IS. Configure the Interface profile and select the Routed Interface with the appropriate interfaces. Create the External Network object.
D. Implement the EIGRP Protocol policy with the selected Autonomous System number. Create Routed Outside object and Node Profile and select EIGRP as the routing protocol. Build the Interface profile and select SVI and the appropriate VPC. Configure the External Network object with a network of 0.0.0.0/0.
-
Question 6:
An engineer must monitor a Cisco ACI fabric with SNMP. The “permit any contract” attribute is not configured in the fabric.
Which action must be taken to receive SNMP traps from Cisco APIC?
A. Consume the inband contract from the out-of-band EPG.
B. Configure the OOB contract under the common tenant.
C. Add the UDP filter port 162 to the existing OOB contract.
D. Provide a standard contract under the user tenant.
-
Question 7:
An engineer wants to configure Cisco ACI switches to use authenticated ZMQ when communicating with the proxy spine.
Which configuration allows MD5 ZMQ messages only?
A. COOP Group policy in strict mode
B. IS-IS password using MD5
C. BGP password using MD5
D. COOP Group policy in compatible mode
-
Question 8:
An engineer created a monitoring policy called Test in a Cisco ACI fabric and had to change the severity level of the monitored object Call home source.
Which set of actions prevent the event from appearing in event reports?
A. Select Faults Severity Assignment Policies. Set severity level to cleared.
B. Select Event Severity Assignment Policies. Set severity level to squelched.
C. Select Faults Severity Assignment Policies. Set severity level to squelched.
D. Select Event Severity Assignment Policies. Set severity level to cleared.
-
Question 9:
Refer to the exhibit.

Cisco ACI fabric is connected to a Cisco Catalyst 3850 Series Switch using EBGP. Server 2 is unable to communicate with Server 1. Leaf-2 fails to learn the external subnet 10.2.2.0/24 and other external subnets from other L3Outs. Which configuration ensures that the networks from Leaf-2 are learned by the external network?
A. Configure 10.2.2.0/24 under the external EPG of the L3Out.
B. Implement a contract between the Server 2 EPG and the L3Out.
C. Implement the bridge domain to advertise the bridge domain subnet.
D. Configure Spine-1 as the MP-BGP route reflector.
-
Question 10:
What is the result of the pcEnPref flag configured on the epg-App_EPG?
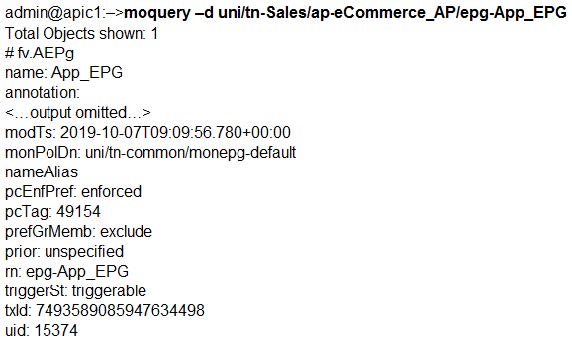
A. Any configuration changes to the private network are validated.
B. Access control rules for the L3Out network are applied.
C. Access control rules for the private network are applied.
D. Any changes to the underlying EPG objects are forbidden.
Related Exams:
300-610
Designing Cisco Data Center Infrastructure (DCID)300-615
Troubleshooting Cisco Data Center Infrastructure (DCIT)300-620
Implementing Cisco Application Centric Infrastructure (DCACI)300-630
Implementing Cisco Application Centric Infrastructure - Advanced (DCACIA)300-635
Automating and Programming Cisco Data Center Solutions (DCAUTO)350-601
Implementing and Operating Cisco Data Center Core Technologies (DCCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-620 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.