Exam Details
Exam Code
:300-710Exam Name
:Securing Networks with Cisco Firepower (SNCF)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:398 Q&AsLast Updated
:Mar 21, 2025
Cisco CCNP Security 300-710 Questions & Answers
-
Question 11:
Refer to the exhibit.
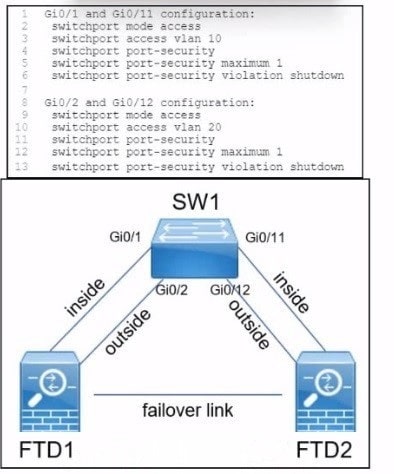
A company is deploying a pair of Cisco Secure Firewall Threat defence devices named FTD1 and FTD2. FTD1 and FTD2 have been configured as an active/standby pair with a failover link but without a stateful link.
What must be implemented next to ensure that users on the internal network still communicate with outside devices if FTD1 fails?
A. Disable port security on the switch interfaces connected to FTD1 and FTD2.
B. Set maximum secured addresses to two on the switch interfaces on FTD1 and FTD2.
C. Connect and configure a stateful link and thon deploy the changes.
D. Configure the spanning-tree PortFasI feature on SW1 and FTD2
-
Question 12:
A network administrator is trying to configure Active Directory authentication for VPN authentication to a Cisco Secure Firewall Threat Defence instance that is registered with Cisco Secure Firewall Management Center. Which system settings must be configured first in Secure Firewall Management Center to accomplish the goal?
A. Device, Remote Access VPN
B. System, Realms
C. Policies, Authentication
D. Authentication, Device
-
Question 13:
Refer to the exhibit.
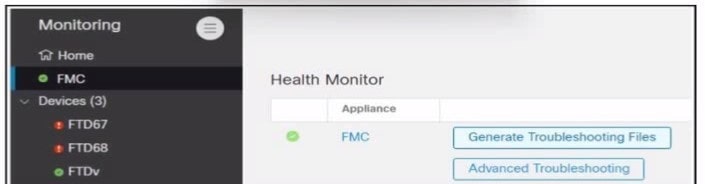
An engineer generates troubleshooting files in Cisco Secure Firewall Management Center (FMC).
A successfully completed task Is removed before the files are downloaded.
Which two actions must be taken to determine the filename and obtain the generated troubleshooting files without regenerating them? (Choose two.)
A. Use an FTP client Hi expert mode on Secure FMC lo upload the files to the FTP server.
B. Go to the same screen as shown in the exhibit, click Advanced Troubleshooting, enter the rile name, and then start the download
C. Connect to CU on the FTD67 and FTD66 devices and copy the tiles from flash to the PIP server.
D. Go to expert mode on Secure FMC. list the contents of/Var/common, and determine the correct filename from the output
E. Click System Monitoring, men Audit to determine the correct filename from the line containing the Generate Troubleshooting Files string.
-
Question 14:
An administrator configures the interfaces of a Cisco Secure Firewall Threat Defence device in an inline IPS deployment.
The administrator completes these actions:
1.
identifies the device and the interfaces
2.
sets the interface mode to inline
3.
enables the interlaces
Which configuration step must the administrator take next to complete the implementation?
A. Enable spanning-tree PortFast on the interfaces.
B. Configure an inline set
C. Set the interface to Transparent mode.
D. Set the interface to routed mode.
-
Question 15:
An administrator is configuring a new report template off. of a saved search within Cisco Secure Firewall Management Centre. The goal is to use the malware analysis report template, but use a different type saved search as the basis. The report is not working.
What must be considered when configuring this report template?
A. Saved searches can be used for the same report template only
B. Saved searches are available freely for all report templates within the same domain.
C. Saved searches from a different report template must be used.
D. Saved searches must be renamed before using for different report template.
-
Question 16:
An engineer must change the mode of a Cisco Secure Firewall Threat Defense (FTD) firewall in the Cisco Secure Firewall Management Center (FMC) inventory.
The engineer must take these actions:
1.
Register Secure FTD with Secure FMC.
2.
Change the firewall mode.
3.
Deregister the Secure FTD device from Secure FMC.
How must the engineer take FTD take the actions?
A. Reload the Secure FTD device.
B. Configure the management IP address.
C. Access the Secure FTD CLI from the console port.
D. Erase the Secure FTD configuration
-
Question 17:
Which component is needed to perform rapid threat containment with Cisco FMC?
A. ISE
B. RESTful API
C. SIEM
D. DDI
-
Question 18:
A network administrator is trying to configure an access rule to allow access to a specific banking site over HTTPS.
Which method must the administrator use to meet the requirement?
A. Enable SSL decryption and specify the URL.
B. Define the URL to be blocked and set the application to HTTP.
C. Define the URL to be blocked and disable SSL inspection.
D. Block the category of banking and define the application of WWW.
-
Question 19:
An engineer is tasked with configuring a custom intrusion rule on Cisco Secure Firewall Management Center to detect and block the malicious traffic pattern with specific payload containing string "|04 68 72 80 87 ff ed cq fg he qm pn|". Which action must the Engineer configure on the IPS policy?
A. reset
B. drop
C. alert
D. disable
E. quarantine
-
Question 20:
An engineer must integrate a third-party security intelligence feed with Cisco Secure Firewall Management Center. Secure Firewall Management Center is running Version 6.2.3 and has 8 GB of memory. Which two actions must be taken to implement Threat Intelligence Director? (Choose two.)
A. Add a TAXI I server.
B. Add the URL of the TAXII server.
C. Upgrade to version 6.6.
D. Enable REST API access.
E. Add 7 GB of memory.
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-710 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.