Exam Details
Exam Code
:300-715Exam Name
:Implementing and Configuring Cisco Identity Services Engine (SISE)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:404 Q&AsLast Updated
:Apr 14, 2025
Cisco CCNP Security 300-715 Questions & Answers
-
Question 151:
An employee must access the internet through the corporate network from a new mobile device that does not support native supplicant provisioning provided by Cisco ISE. Which portal must the employee use to provision to the device?
A. My Devices
B. BYOD
C. Personal Device
D. Client Provisioning
-
Question 152:
An engineer builds a five-node distributed Cisco ISE deployment. The first two deployed nodes are responsible for the primary and secondary administration and monitoring personas.
Which persona configuration is necessary to have the remaining three Cisco ISE nodes serve as dedicated nodes in the Cisco ISE cube that is responsible only for handling the RADIUS and TACACS+ authentication requests, identity lookups, and policy evaluation?
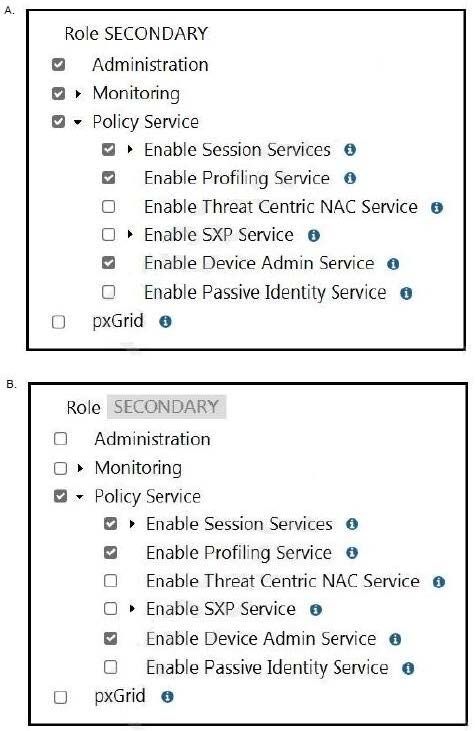
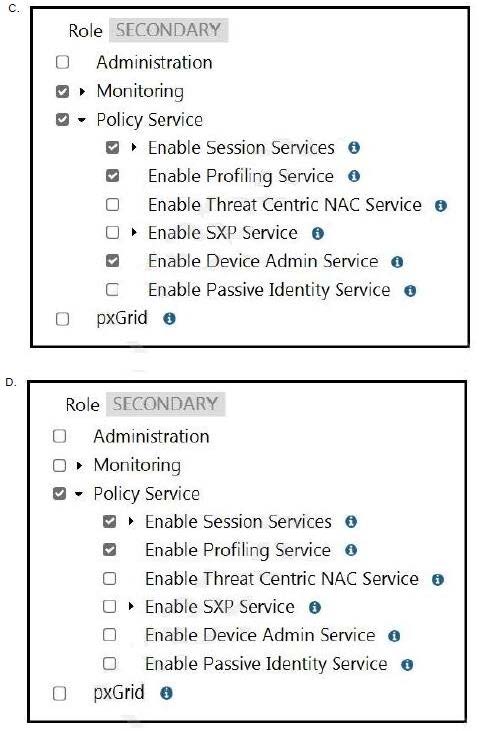
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 153:
What are two differences between the RADIUS and TACACS+ protocols? (Choose two.)
A. RADIUS offers multiprotocol support, whereas TACACS+ does not.
B. RADIUS is a Cisco proprietary protocol, whereas TACACS+ is an open standard protocol.
C. RADIUS enables encryption of all the packets, whereas with TACACS+, only the password is encrypted.
D. RADIUS combines authentication and authorization, whereas TACACS+ does not.
E. TACACS+ uses TCP port 49, whereas RADIUS uses UDP ports 1812 and 1813.
-
Question 154:
A network administrator is configuring client provisioning resource policies for client machines and must ensure that an agent pop-up is presented to the client when attempting to connect to the network. Which configuration item needs to be added to allow for this?
A. a temporal agent that gets installed onto the system
B. a remote posture agent proxying the network connection
C. the client provisioning URL in the authorization policy
D. an API connection back to the client
-
Question 155:
A network administrator is configuring a secondary Cisco ISE node from the backup configuration of the primary Cisco ISE node to create a high availability pair. The Cisco ISE CA certificates and keys must be manually backed up from the primary Cisco ISE and copied into the secondary Cisco ISE.
Which command must be issued for this to work?
A. copy certificate ise
B. certificate configure ise
C. import certificate ise
D. application configure ise
-
Question 156:
A network engineer has been tasked with enabling a switch to support standard web authentication for Cisco ISE. This must include the ability to provision for URL redirection on authentication.
Which two commands must be entered to meet this requirement? (Choose two.)
A. ip http secure-server
B. ip http authentication
C. ip http server
D. ip http redirection
E. ip http secure-authentication
-
Question 157:
A network administrator notices that after a company-wide shut down, many users cannot connect their laptops to the corporate SSID.
What must be done to permit access in a timely manner?
A. Connect this system as a guest user and then redirect the web auth protocol to log in to the network.
B. Allow authentication for expired certificates within the EAP-TLS section under the allowed protocols.
C. Add a certificate issue from the CA server, revoke the expired certificate, and add the new certificate in system.
D. Authenticate the user's system to the secondary Cisco ISE node and move this user to the primary with the renewed certificate.
-
Question 158:
An engineer tests Cisco ISE posture services on the network and must configure the compliance module to automatically download and install on endpoints. Which action accomplishes this task for VPN users?
A. Push the compliance module from Cisco FTD prior to attempting posture.
B. Use a compound posture condition to check for the compliance module and download, if needed.
C. Configure the compliance module to be downloaded from within the posture policy.
D. Create a Cisco AnyConnect configuration and Client Provisioning policy within Cisco ISE.
-
Question 159:
Which two external identity stores support EAP-TLS and PEAP-TLS? (Choose two.)
A. RSA SecurID
B. RADIUS Token
C. Active Directory
D. Internal Database
E. LDAP
-
Question 160:
An engineer deploys Cisco ISE and must configure Active Directory to then use information from Active Directory in an authorization policy.
Which two components must be configured, in addition to Active Directory groups, to achieve this goal? (Choose two.)
A. Identity Source Sequences
B. LDAP External Identity Sources
C. Active Directory External Identity Sources
D. Library Condition for Identity Group: User Identity Group
E. Library Condition for External Identity: External Groups
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-715 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.