Exam Details
Exam Code
:300-715Exam Name
:Implementing and Configuring Cisco Identity Services Engine (SISE)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:404 Q&AsLast Updated
:Mar 28, 2025
Cisco CCNP Security 300-715 Questions & Answers
-
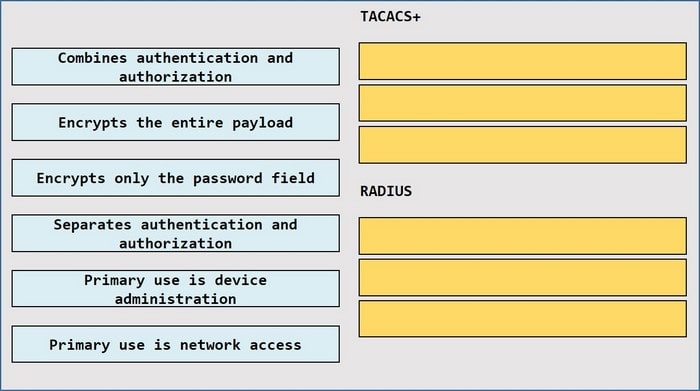
Question 21:
DRAG DROP
Drag and drop the description from the left onto the protocol on the right that is used to carry out system authentication, authentication, and accounting.
Select and Place:
-
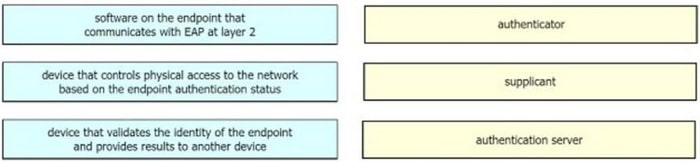
Question 22:
DRAG DROP
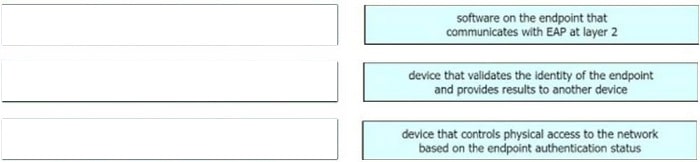
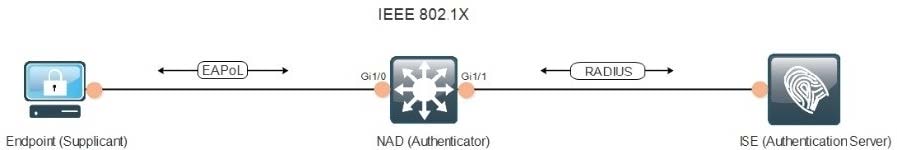
Drag the descriptions on the left onto the components of 802.1X on the right.
Select and Place:
-
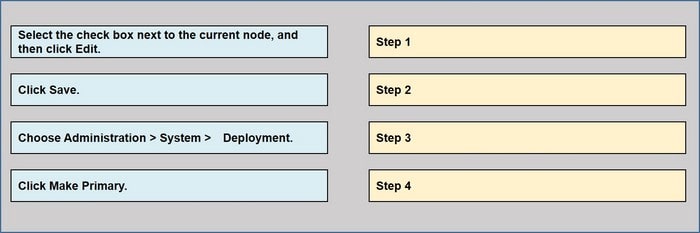
Question 23:
DRAG DROP
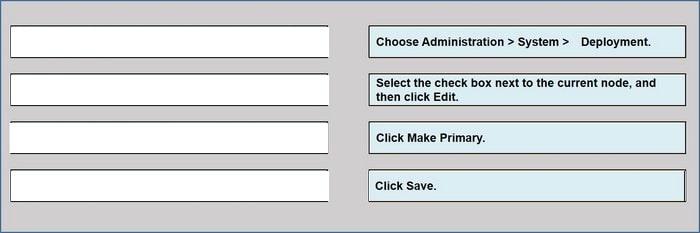
Drag the steps to configure a Cisco ISE node as a primary administration node from the left into the correct order on the night.
Select and Place:
-
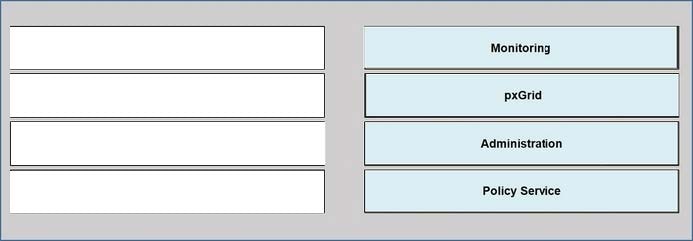
Question 24:
DRAG DROP
Drag the Cisco ISE node types from the left onto the appropriate purposes on the right.
Select and Place:
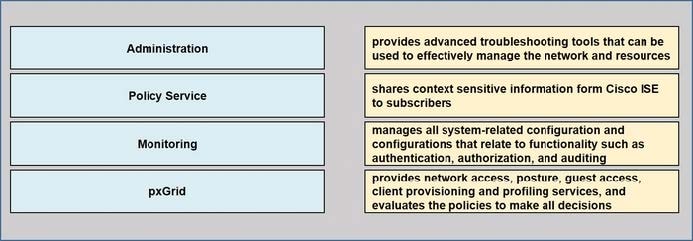
-
Question 25:
Refer to the exhibit.
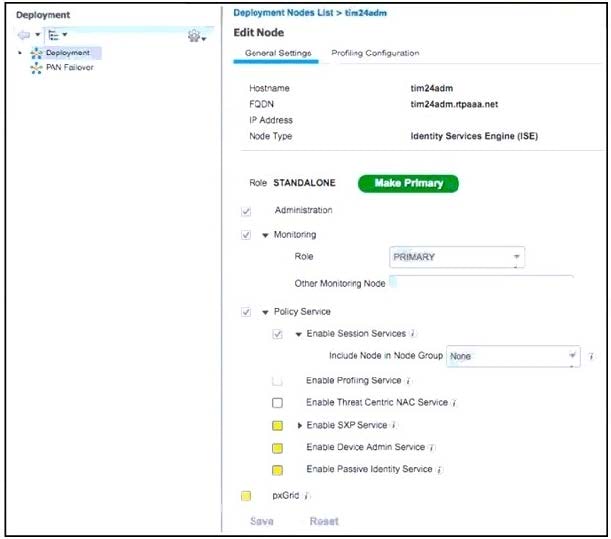
Which checkbox must be enabled to allow Cisco ISE to publish group membership information for active users that can be shared with Cisco Firepower devices?
A. Enable Passive Identity Service
B. Enable SXP Service
C. Enable Device Admin Service
D. pxGrid
-
Question 26:
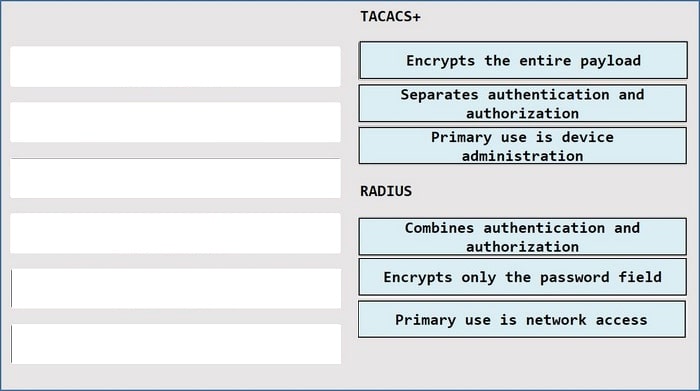
What is a difference between TACACS+ compared to RADIUS? (Choose two.)
A. TACACS+ encrypts only the password, and RADIUS encrypts the entire packet payload.
B. TACACS+ uses a connection-oriented transport, and RADIUS uses a connectionless transport.
C. TACACS+ supports 802.1X network access control, and RADIUS supports only MAB.
D. TACACS+ offers multiple protocol support, and RADIUS supports only IP traffic.
-
Question 27:
An engineer must use certificate authentication for endpoints that connect to a wired network with a Cisco ISE deployment. The engineer must define the certificate field used as the principal username. What is needed to complete the configuration?
A. authorization profile
B. authentication policy
C. authorization rule
D. authentication profile
-
Question 28:
A client with MAC address 04:77:10:14:67:AB connects to the network. The client does not support 802.1X. Which setting must be enabled in the Allowed Authentication Protocols list in your Authentication Policy for Cisco ISE Server to support MAB authentication for this MAC address?
A. Process Host Lookup
B. EAP-FAST
C. EAP-TTLS
D. MS-CHAPv2
-
Question 29:
A network engineer is configuring a Cisco WLC in order to find out more information about the devices that are connecting. This information must be sent to Cisco ISE to be used in authorization policies. Which profiling mechanism must be configured in the Cisco WLC to accomplish this task?
A. SNMP
B. CDP
C. DNS
D. DHCP
-
Question 30:
The security team identified a rogue endpoint with MAC address 00:46:91:02:28:4A attached to the network. Which action must security engineer take within Cisco ISE to effectively restrict network access for this endpoint?
A. Configure access control list on network switches to block traffic.
B. Create authentication policy to force reauthentication.
C. Add MAC address to the endpoint quarantine list.
D. Implement authentication policy to deny access.
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-715 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.