Exam Details
Exam Code
:300-915Exam Name
:Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)Certification
:Cisco CertificationsVendor
:CiscoTotal Questions
:59 Q&AsLast Updated
:Mar 07, 2025
Cisco Cisco Certifications 300-915 Questions & Answers
-
Question 31:
Which two actions must be completed before starting the process of sending IoT data to the cloud via edge routers? (Choose two.)
A. Measure the voltage, power rating, and quiescent current for the sensors that send data to the cloud.
B. Gather the hardware (MAC) addresses of local and cloud routers to ensure low latency communication.
C. Collect information about the CPU architecture in the cloud and edge to ensure that they match.
D. Gather the interval, the volume, and the latency that the data must be provisioned with.
E. Collect information about growth, required elasticity, and high availability of the provisioning process.
-
Question 32:
As part of an IoT project, an organization is developing an application that will share multiple clients using a REST API.
Based on the software development process, what are two valid technical activities that can be suggested to secure the REST API that is developed during the development of the software? (Choose two.)
A. Respond to request failures in detail to allow users for easier troubleshooting.
B. Implement HTTP whitelisting to only methods that are allowed.
C. Implement and review audit logs for security-related events.
D. Reject HTTP methods that are invalid with an error code 404.
E. Implement physical firewalling and access control to the resources.
-
Question 33:
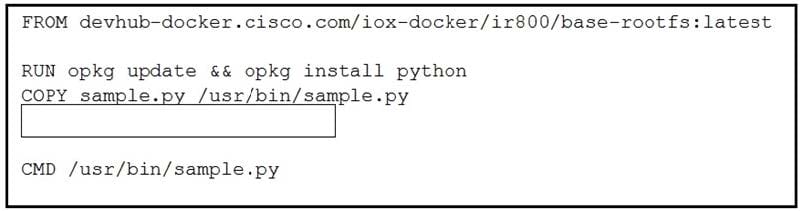
Refer to the exhibit. Which line of code completes the Dockerfile?
A. RUN chmod 777 /usr/bin/sample.py
B. RUN chown root:root /usr/bin/sample.py
C. WORKDIR /usr/bin
D. USER root
-
Question 34:
A network is being configured for an Ethernet-connected sensor. The sensor fails to send data to the configured destination. The IP address of the sensor can be pinged from a laptop on the same subnet. When a different subnet is used, the sensor cannot be reached, but other clients on the same subnet are still accessible.
What are two reasons for the connectivity problem? (Choose two.)
A. wrong DNS server on the sensor
B. wrong subnet mask on your laptop
C. wrong default gateway on the sensor
D. wrong default gateway on your laptop
E. wrong subnet mask on the sensor
-
Question 35:
Which two statements about how to provision and manage data originators in a cloud environment are true? (Choose two.)
A. The provisioning of digital identities is the responsibility of the data originators.
B. Cloud providers offer services for automated device provisioning, which allows the lifecycle of the cloud-representation for data originators to be managed.
C. Cloud providers offer application programming interfaces, which allow a programmatic provisioning of data originators.
D. There is no need to provision and manage access for data originators in the cloud.
E. The access to public clouds must be configured and managed manually.
-
Question 36:
An IoT application has been built into the application CI/CD pipeline. The application needs credentials to access other applications, APIs, and cloud resources.
When should the credentials be inserted into the application using the CI/CD process?
A. hard coded into your application code base
B. during application runtime
C. after application testing
D. during application build time
-
Question 37:
The environment for an Industrial IoT project in a large open pit mine is being scoped. The location has a large amount of dust and the device will be exposed to less than 1 meter of water temporarily.
When the edge device is being chosen, which Ingress protection rating must be used?
A. IP37
B. IP61
C. IP67
D. IP76
-
Question 38:
Which two statements define the mechanism for console access of the Guest Operating System from the Cisco IR829 router? (Choose two.)
A. The Guest OS can be accessed by default on Telnet port 2070 from the Cisco IR829 console.
B. The Guest OS console is available directly by the AUX port 3362 from the Cisco IR829 router.
C. The Guest OS can be accessed directly using the console port on the Cisco IR829 router.
D. The Guest OS can be accessed by initiating SSH from the Cisco IR829 console.
E. The Guest OS console is available only when a static IP is configured on the host.
-
Question 39:
What is a major difference of MQTT in terms of design compared to AMQP?
A. MQTT requires more bandwidth.
B. MQTT has very low overhead.
C. MQTT has more advanced routing features for messages.
D. MQTT provides routing based on headers.
-
Question 40:
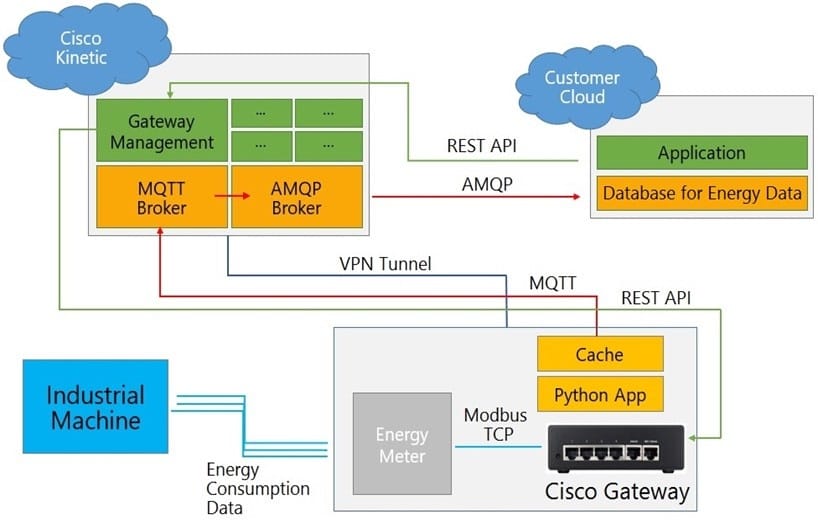
Refer to the exhibit. Which two statements about data flow are true? (Choose two.)
A. Another AMQP broker should be implemented on the customer cloud.
B. Instead of AMQP, MQTT should be used for compatibility issues in a cloud-to-cloud connection.
C. A VPN tunnel is not necessary because the MQTT payload is encrypted by default.
D. The gateway must stay constantly connected to the Kinetic cloud to avoid blank data sets, even when using caching functions.
E. The Python application could use the paho-mqtt library.
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-915 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.