Exam Details
Exam Code
:312-38Exam Name
:EC-Council Certified Network Defender (CND)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:653 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-38 Questions & Answers
-
Question 141:
Which characteristic of an antenna refers to how directional an antennas radiation pattern is?
A. Radiation pattern
B. Polarization
C. Directivity
D. Typical gain
-
Question 142:
Which field is not included in the TCP header?
A. Acknowledgment number
B. Sequence number
C. Source port
D. Source IP address
-
Question 143:
John wants to implement a packet filtering firewall in his organization's network. What TCP/IP layer does a packet filtering firewall work on?
A. Network Interface layer
B. Application layer
C. IP layer
D. TCP layer
-
Question 144:
What command is used to terminate certain processes in an Ubuntu system?
A. # netstat Kill [ Target Process]
B. #ps ax Kill
C. #grep Kill [Target Process]
D. #kill -9 [PID]
-
Question 145:
Which type of wireless network threats an attacker stakes out the area from a nearby location with a high gain amplifier drowning out the legitimate access point?
A. Rogue access point attack
B. Jamming signal attack
C. Ad Hoc Connection attack
D. Unauthorized association
-
Question 146:
Which of the following type of UPS is used to supply power above 10kVA and provides an ideal electric output presentation, and its constant wear on the power components reduces the dependability?
A. Line Interactive
B. Double conversion on-line
C. Stand by Ferro
D. Stand by On-line hybrid
-
Question 147:
John has planned to update all Linux workstations in his network. The organization is using various Linux distributions including Red hat, Fedora and Debian. Which of following commands will he use to update each respective Linux distribution?
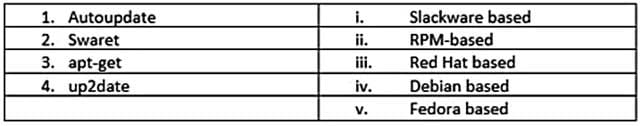
A. 1-ii, 2-i,3-iv,4-iii
B. 1-v,2-iii,3-i,4-iv
C. 1-iv,2-v,3-iv,4-iii
D. 1-iii,2-iv,3-ii,4-v
-
Question 148:
Andrew would like to configure IPsec in a manner that provides confidentiality for the content of packets. What component of IPsec provides this capability?
A. IKE
B. ESP
C. AH
D. ISAKMP
-
Question 149:
A newly joined network administrator wants to assess the organization against possible risk. He notices the organization doesn't have a __________ identified which helps measure how risky an activity is.
A. Risk Severity
B. Risk Matrix
C. Risk levels
D. Key Risk Indicator
-
Question 150:
Sean has built a site-to-site VPN architecture between the head office and the branch office of his company. When users in the branch office and head office try to communicate with each other, the traffic is encapsulated. As the traffic passes though the gateway, it is encapsulated again. The header and payload both are encapsulated. This second encapsulation occurs only in the __________ implementation of a VPN.
A. Point-to-Point Mode
B. Transport Mode
C. Tunnel Mode
D. Full Mesh Mode
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-38 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.