Exam Details
Exam Code
:312-38Exam Name
:EC-Council Certified Network Defender (CND)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:653 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-38 Questions & Answers
-
Question 471:
Which of the following offer "always-on" Internet service for connecting to your ISP? Each correct answer represents a complete solution. Choose all that apply.
A. analog modem
B. digital modem
C. DSL
D. cable modem
-
Question 472:
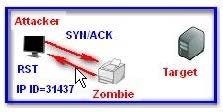
Which of the following steps are required in an idle scan of a closed port? Each correct answer represents a part of the solution. Choose all that apply.
A. The attacker sends a SYN/ACK to the zombie.
B. The zombie's IP ID increases by only 1.
C. In response to the SYN, the target sends a RST.
D. The zombie ignores the unsolicited RST, and the IP ID remains unchanged.
E. The zombie's IP ID increases by 2.
-
Question 473:
Which of the following is a mechanism that helps to ensure that only the intended and authorized recipients are able to read the data?
A. access to information
B. none
C. integrity
D. authentication
E. confidence
-
Question 474:
Which of the following attacks, the attacker cannot use the software, which is trying a number of key combinations in order to obtain your password?
A. Buffer overflow
B. Zero-day attack
C. Smurf attack
D. None
E. Shock brutal force
-
Question 475:
You just set up a wireless network to customers in the cafe. Which of the following are good security measures implemented? Each correct answer represents a complete solution. Choose all that apply.
A. WEP encryption
B. WPA encryption
C. Not broadcasting the SSID
D. The MAC-filtering router
-
Question 476:
What is needed for idle scan a closed port the next steps? Each correct answer represents a part of the solution. Choose all that apply.
A. Zombie ignores unsolicited RST, and IP ID remains unchanged.
B. The attacker sends a SYN/ACK zombie.
C. In response to the SYN, the target to send RST.
D. Zombie IP ID will increase by only 1.
E. Zombie IP ID 2 rises.
-
Question 477:
What is the technique used in the cost estimates for the project during the design phase of the following? Each correct answer represents a complete solution. Choose all that apply.
A. expert assessment
B. The Delphi technique
C. Function point analysis
D. Program Evaluation Technique (PERT)
-
Question 478:
Which of the following is a management process that provides a framework to stimulate a rapid recovery, and the ability to react effectively to protect the interests of its brand, reputation and stakeholders?
A. None
B. log analysis
C. Business Continuity Management
D. patch management
E. response systems
-
Question 479:
Which of the following is the standard protocol that provides VPN security at the highest level?
A. P.M
B. IPSec
C. PPP
D. None
E. L2TP
-
Question 480:
Which of the following is a distance vector routing protocols? Each correct answer represents a complete solution. Choose all that apply.
A. OSPF
B. IGRP
C. IS-IS
D. REST IN PEACE
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-38 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.