Exam Details
Exam Code
:312-38Exam Name
:EC-Council Certified Network Defender (CND)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:653 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-38 Questions & Answers
-
Question 41:
Implementing access control mechanisms, such as a firewall, to protect the network is an example of which of the following network defense approach?
A. Proactive approach
B. Retrospective approach
C. Preventive approach
D. Reactive approach
-
Question 42:
Which type of antenna is based on the principle of a satellite dish and can pick up Wi-Fi signals from a distance of ten miles of more?
A. Yagi antenna
B. Directional antenna
C. Omnidirectional antenna
D. Parabolic Grid antenna
-
Question 43:
Which scan attempt can penetrate through a router and a firewall that filter incoming packets with particular flags set and is not supported by Windows?
A. ARP scan attempt
B. TCP full connect scan attempt
C. TCP null scan attempt
D. PINC sweep attempt
-
Question 44:
Which type of training can create awareness among employees regarding compliance issues?
A. Social engineering awareness training
B. Security policy training
C. Physical security awareness training
D. Training on data classification
-
Question 45:
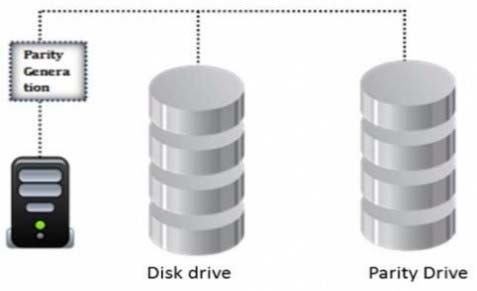
Identify the minimum number of drives required to setup RAID level 5.
A. Multiple
B. 3
C. 4
D. 2
-
Question 46:
Which of the following filters can be used to detect UDP scan attempts using Wireshark?
A. icmp.type==3 and icmp.code==3
B. icmp.type==13
C. icmp.type==8 or icmp.type==0
D. icmp.type==15
-
Question 47:
Rosa is working as a network defender at Linda Systems. Recently, the company migrated from Windows to MacOS. Rosa wants to view the security related logs of her system, where con she find these logs?
A. /private/var/log
B. /var/log/cups/access-log
C. /Library/Logs/Sync
D. /Library/Logs
-
Question 48:
Which of the following characteristics represents a normal TCP packet?
A. SYN and FIN bits are set
B. Source or destination port b zero
C. FIN ACK and ACK are used in terminating the connection
D. The destination address is a broadcast address
-
Question 49:
Who offers formal experienced testimony in court?
A. Incident analyzer
B. Evidence documenter
C. Expert witness
D. Attorney
-
Question 50:
Which among the following is used to limit the number of cmdlets or administrative privileges of administrator, user, or service accounts?
A. Just Enough Administration (EA)
B. User Account Control (UAC)
C. Windows Security Identifier (SID)
D. Credential Guard
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-38 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.