Exam Details
Exam Code
:312-38Exam Name
:EC-Council Certified Network Defender (CND)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:653 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-38 Questions & Answers
-
Question 501:
Which of the following tools is an open source network intrusion prevention and detection system that works network sniffer and record the operation of the network, which is coordinated pre-signatures?
A. dsniff
B. kismet
C. None
D. KisMAC
E. bridle
-
Question 502:
Which of the following statements best describes the consequences of a disaster recovery test?
A. None
B. The test results should be kept secret.
C. If no deficiencies were found during the test, so the plan is probably perfect.
D. If no deficiencies were found during the test, the test was probably erroneous.
E. The plan should not change any of the test results would be.
-
Question 503:
Which of the following flag to set whether the scan sends TCP Christmas tree frame with the remote machine? Each correct answer represents a part of the solution. Choose all that apply.
A. FIN
B. URG
C. RST
D. PUSH
-
Question 504:
What is used for drawing symbols in public places following techniques of advertising an open Wi-Fi network?
A. wardriving
B. None
C. spam
D. war call
E. warchalking
-
Question 505:
Which of the following firewalls are used to monitor the status of active connections, and configure the network packets to pass through the firewall? Each correct answer represents a complete solution. Choose all that apply.
A. Farm owner
B. Proxy server
C. Dynamic packet filtering
D. The circuit gateway
-
Question 506:
You work for a professional computer hacking forensic investigator DataEnet Inc. To explore the e-mail information about an employee of the company. The suspect an employee to use the online e-mail systems such as Hotmail or Yahoo. Which of the following folders on the local computer you are going to check to accomplish the task? Each correct answer represents a complete solution. Choose all that apply.
A. cookies folder
B. Temporary Internet Folder
C. download folder
D. History Folder
-
Question 507:
Which of the following standards is a change in the original IEEE 802.11 and defines the security mechanisms for wireless networks?
A. 802.11b
B. 802.11a
C. None
D. 802.11e
E. 802.11i
-
Question 508:
Which of the following representatives of the incident response team takes the forensic backups of systems that are essential event?
A. the legal representative
B. technical representative
C. lead investigator
D. None
E. Information Security representative
-
Question 509:
Which of the following strategies is used to minimize the effects of a disruptive event on a company, and is created to prevent interruptions to normal business activity?
A. Disaster Recovery Plan
B. Business Continuity Plan
C. Contingency Plan
D. Continuity of Operations Plan
-
Question 510:
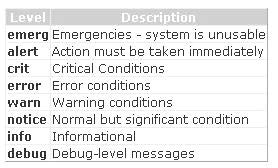
Adam works as a Security Analyst for Umbrella Inc. The company has a Linux-based network comprising an Apache server for Web applications. He received the following Apache Web server log, which is as follows:
[Sat Nov 16 14:32:52 2009] [error] [client 128.0.0.7] client denied by server configuration: /export/home/htdocs/test
The first piece in the log entry is the date and time of the log message. The second entry determines the severity of the error being reported. Now Adam wants to change the severity level to control the types of errors that are sent to the error
log. Which of the following directives will Adam use to accomplish the task?
A. CustomLog
B. ErrorLog
C. LogFormat
D. LogLevel
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-38 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.