Exam Details
Exam Code
:312-38Exam Name
:EC-Council Certified Network Defender (CND)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:653 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-38 Questions & Answers
-
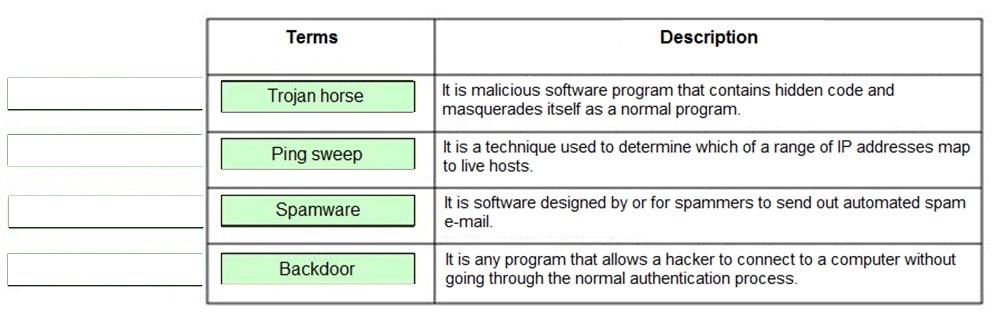
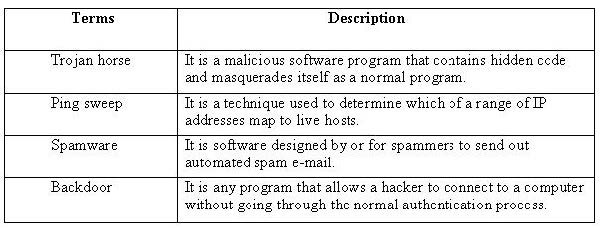
Question 611:
DRAG DROP
Drag and drop the terms to match with their descriptions.
Select and Place:
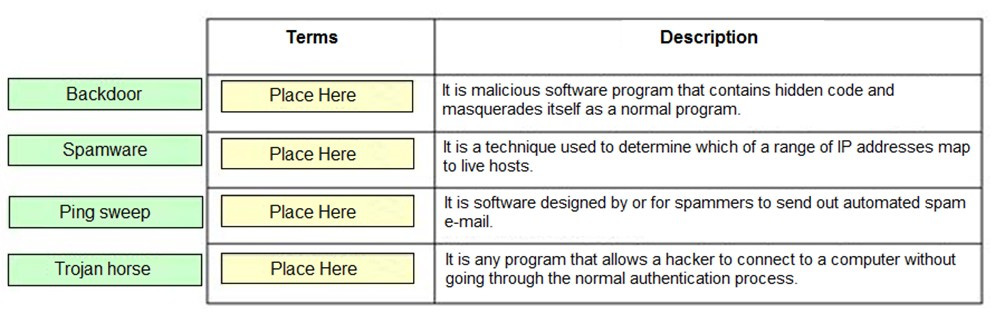
-
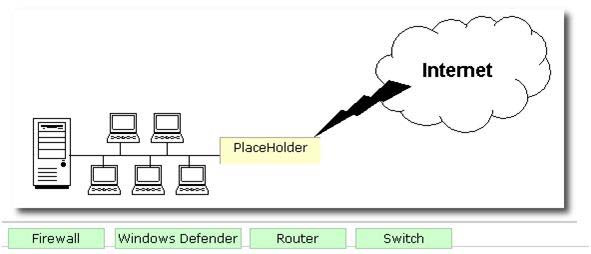
Question 612:
DRAG DROP
George works as a Network Administrator for Blue Soft Inc. The company uses Windows Vista operating system. The network of the company is continuously connected to the Internet. What will George use to protect the network of the company from intrusion?
Select and Place:
-
Question 613:
Choose the correct order of steps to analyze the attack surface.
A. Identify the indicators of exposure->visualize the attack surface->simulate the attack->reduce the attack surface
B. Visualize the attack surface->simulate the attack->identify the indicators of exposure->reduce the attack surface
C. Identify the indicators of exposure->simulate the attack->visualize the attack surface->reduce the attack surface
D. Visualize the attack surface->identify the indicators of exposure->simulate the attack->reduce the attack surface
-
Question 614:
Leslie, the network administrator of Livewire Technologies, has been recommending multilayer inspection firewalls to deploy the company's infrastructure. What layers of the TCP/IP model can it protect?
A. IP, application, and network interface
B. Network interface, TCP, and IP
C. Application, TCP, and IP
D. Application, IP, and network interface
-
Question 615:
To provide optimum security while enabling safe/necessary services, blocking known dangerous services, and making employees accountable for their online activity, what Internet Access policy would Brian, the network administrator, have to choose?
A. Prudent policy
B. Paranoid policy
C. Promiscuous policy
D. Permissive policy
-
Question 616:
Which command list all ports available on a server?
A. sudo apt nst -tunIp
B. sudo netstat -tunIp
C. sudo apt netstate -Is tunIp
D. sudo ntstat -Is tunIp
-
Question 617:
Which BC/DR activity works on the assumption that the most critical processes are brought back from a remote location first, followed by the less critical functions?
A. Recovery
B. Restoration
C. Response
D. Resumption
-
Question 618:
Emmanuel works as a Windows system administrator at an MNC. He uses PowerShell to enforce the script execution policy. He wants to allow the execution of the scripts that are signed by a trusted publisher. Which of the following script execution policy setting this?
A. AllSigned
B. Restricted
C. RemoteSigned
D. Unrestricted
-
Question 619:
Fargo, head of network defense at Globadyne Tech, has discovered an undesirable process in several Linux systems, which causes machines to hang every 1 hour. Fargo would like to eliminate it; what command should he execute?
A. # update-rc.d -f [service name] remove
B. # service [service name] stop
C. # ps ax | grep [Target Process]
D. # kill -9 [PID]
-
Question 620:
Which of the following refers to the data that is stored or processed by RAM, CPUs, or databases?
A. Data in Backup
B. Data at Rest
C. Data in Transit
D. Data is Use
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-38 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.