Exam Details
Exam Code
:312-49Exam Name
:ECCouncil Computer Hacking Forensic Investigator (V9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:531 Q&AsLast Updated
:Apr 11, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49 Questions & Answers
-
Question 1:
What is the investigator trying to analyze if the system gives the following image as output?
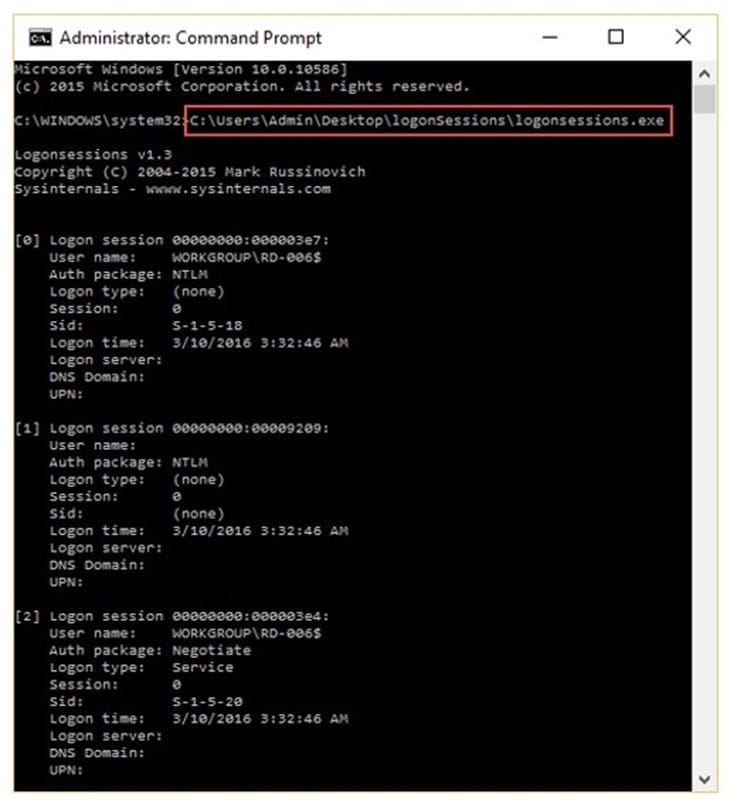
A. All the logon sessions
B. Currently active logon sessions
C. Inactive logon sessions
D. Details of users who can logon
-
Question 2:
Which of the following is found within the unique instance ID key and helps investigators to map the entry from USBSTOR key to the MountedDevices key?
A. ParentIDPrefix
B. LastWrite
C. UserAssist key
D. MRUListEx key
-
Question 3:
What technique is used by JPEGs for compression?
A. TIFF-8
B. ZIP
C. DCT
D. TCD
-
Question 4:
Analyze the hex representation of mysql-bin.000013 file in the screenshot below. Which of the following will be an inference from this analysis?
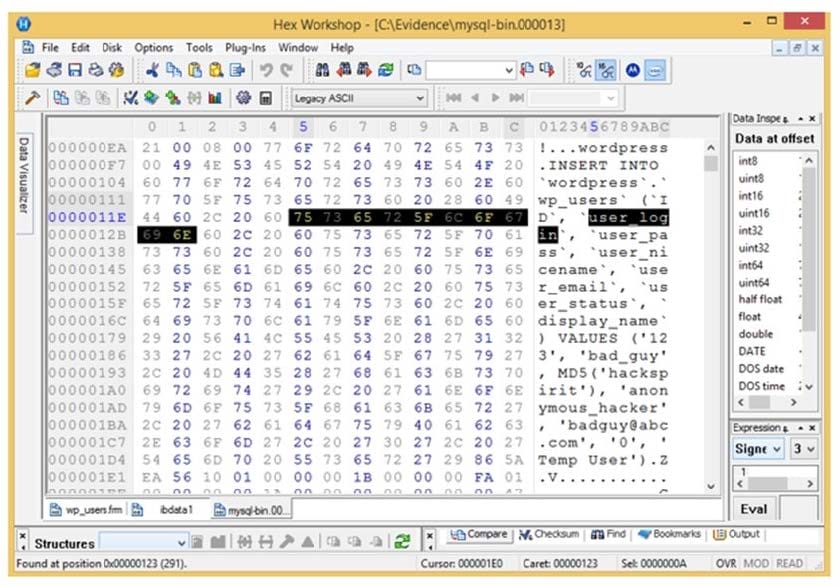
A. A user with username bad_guy has logged into the WordPress web application
B. A WordPress user has been created with the username anonymous_hacker
C. An attacker with name anonymous_hacker has replaced a user bad_guy in the WordPress database
D. A WordPress user has been created with the username bad_guy
-
Question 5:
Brian needs to acquire data from RAID storage. Which of the following acquisition methods is recommended to retrieve only the data relevant to the investigation?
A. Static Acquisition
B. Sparse or Logical Acquisition
C. Bit-stream disk-to-disk Acquisition
D. Bit-by-bit Acquisition
-
Question 6:
Which of the following is a precomputed table containing word lists like dictionary files and brute force lists and their hash values?
A. Directory Table
B. Rainbow Table
C. Master file Table (MFT)
D. Partition Table
-
Question 7:
What is the capacity of Recycle bin in a system running on Windows Vista?
A. 2.99GB
B. 3.99GB
C. Unlimited
D. 10% of the partition space
-
Question 8:
For what purpose do the investigators use tools like iPhoneBrowser, iFunBox, OpenSSHSSH, and iMazing?
A. Bypassing iPhone passcode
B. Debugging iPhone
C. Rooting iPhone
D. Copying contents of iPhone
-
Question 9:
Which of the following does Microsoft Exchange E-mail Server use for collaboration of various e-mail applications?
A. Simple Mail Transfer Protocol (SMTP)
B. Messaging Application Programming Interface (MAPI)
C. Internet Message Access Protocol (IMAP)
D. Post Office Protocol version 3 (POP3)
-
Question 10:
An investigator is analyzing a checkpoint firewall log and comes across symbols. What type of log is he looking at?

A. Security event was monitored but not stopped
B. Malicious URL detected
C. An email marked as potential spam
D. Connection rejected
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.