Exam Details
Exam Code
:312-49V10Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1006 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V10 Questions & Answers
-
Question 1:
NTFS sets a flag for the file once you encrypt it and creates an EFS attribute where it stores Data Decryption Field (DDF) and Data Recovery Field (DDR). Which of the following is not a part of DDF?
A. Encrypted FEK
B. Checksum
C. EFS Certificate Hash
D. Container Name
-
Question 2:
Pick the statement which does not belong to the Rule 804. Hearsay Exceptions; Declarant Unavailable.
A. Statement of personal or family history
B. Prior statement by witness
C. Statement against interest
D. Statement under belief of impending death
-
Question 3:
Which of the following is a responsibility of the first responder?
A. Determine the severity of the incident
B. Collect as much information about the incident as possible
C. Share the collected information to determine the root cause
D. Document the findings
-
Question 4:
Which of the following examinations refers to the process of providing the opposing side in a trial the opportunity to question a witness?
A. Cross Examination
B. Direct Examination
C. Indirect Examination
D. Witness Examination
-
Question 5:
In a Linux-based system, what does the command “Last -F” display?
A. Login and logout times and dates of the system
B. Last run processes
C. Last functions performed
D. Recently opened files
-
Question 6:
Which layer of iOS architecture should a forensics investigator evaluate to analyze services such as Threading, File Access, Preferences, Networking and high-level features?
A. Core Services
B. Media services
C. Cocoa Touch
D. Core OS
-
Question 7:
Which command can provide the investigators with details of all the loaded modules on a Linux-based system?
A. list modules -a
B. lsmod
C. plist mod -a
D. lsof -m
-
Question 8:
What is the investigator trying to view by issuing the command displayed in the following screenshot?
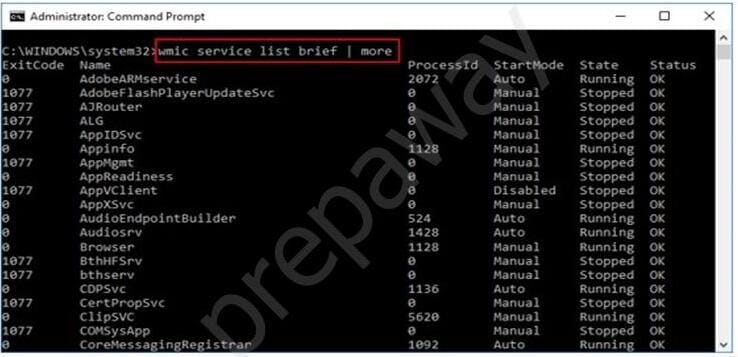
A. List of services stopped
B. List of services closed recently
C. List of services recently started
D. List of services installed
-
Question 9:
Which of the following file formats allows the user to compress the acquired data as well as keep it randomly accessible?
A. Proprietary Format
B. Generic Forensic Zip (gfzip)
C. Advanced Forensic Framework 4
D. Advanced Forensics Format (AFF)
-
Question 10:
Which of the following tool can reverse machine code to assembly language?
A. PEiD
B. RAM Capturer
C. IDA Pro
D. Deep Log Analyzer
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.