Exam Details
Exam Code
:312-49V9Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:531 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V9 Questions & Answers
-
Question 111:
What does the superblock in Linux define?
A. file synames
B. disk geometr
C. location of the first inode
D. available space
-
Question 112:
What is the following command trying to accomplish? C:\> nmap -sU -p445 192.168.0.0/24
A. Verify that TCP port 445 is open for the 192.168.0.0 network
B. Verify that UDP port 445 is open for the 192.168.0.0 network
C. Verify that UDP port 445 is closed for the 192.168.0.0 network
D. Verify that NETBIOS is running for the 192.168.0.0 network
-
Question 113:
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast. On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently. What could be Tyler issue with his home wireless network?
A. CB radio
B. 2.4Ghz Cordless phones
C. Satellite television
D. Computers on his wired network
-
Question 114:
Diskcopy is:
A. a utility by AccessData
B. a standard MS-DOS command
C. Digital Intelligence utility
D. dd copying tool
-
Question 115:
In the following email header, where did the email first originate from?
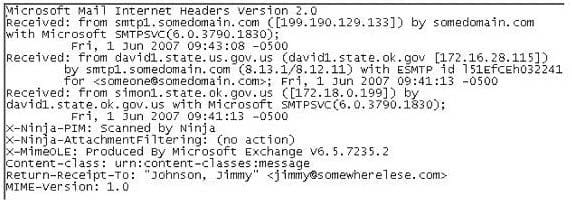
A. Somedomain.com
B. Smtp1.somedomain.com
C. Simon1.state.ok.gov.us
D. David1.state.ok.gov.us
-
Question 116:
The MD5 program is used to:
A. wipe magnetic media before recycling it
B. make directories on a evidence disk
C. view graphics files on an evidence drive
D. verify that a disk is not altered when you examine it
-
Question 117:
In a forensic examination of hard drives for digital evidence, what type of user is most likely to have the most file slack to analyze?
A. one who has NTFS 4 or 5 partitions
B. one who uses dynamic swap file capability
C. one who uses hard disk writes on IRQ 13 and 21
D. one who has lots of allocation units per block or cluster
-
Question 118:
What header field in the TCP/IP protocol stack involves the hacker exploit known as the Ping of Death?
A. ICMP header field
B. TCP header field
C. IP header field
D. UDP header field
-
Question 119:
You have compromised a lower-level administrator account on an Active Directory network of a small
company in Dallas, Texas. You discover Domain Controllers through enumeration. You connect to one of
the Domain Controllers on port 389 using ldp.exe.
What are you trying to accomplish here?
A. Enumerate domain user accounts and built-in groups
B. Enumerate MX and A records from DNS
C. Establish a remote connection to the Domain Controller
D. Poison the DNS records with false records
-
Question 120:
Jason has set up a honeypot environment by creating a DMZ that has no physical or logical access to his production network. In this honeypot, he has placed a server running Windows Active Directory. He has also placed a Web server in the DMZ that services a number of web pages that offer visitors a chance to download sensitive information by clicking on a button. A week later, Jason finds in his network logs how an intruder accessed the honeypot and downloaded sensitive information. Jason uses the logs to try and prosecute the intruder for stealing sensitive corporate information. Why will this not be viable?
A. Enticement
B. Entrapment
C. Intruding into ahoneypot is not illegal
D. Intruding into a DMZ is not illegal
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V9 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.