Exam Details
Exam Code
:312-49V9Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:531 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V9 Questions & Answers
-
Question 301:
An investigator is searching through the firewall logs of a company and notices ICMP packets that are larger than 65,536 bytes. What type of activity is the investigator seeing?
A. Smurf
B. Ping of death
C. Fraggle
D. Nmap scan
-
Question 302:
An employee is attempting to wipe out data stored on a couple of compact discs (CDs) and digital video discs (DVDs) by using a large magnet. You inform him that this method will not be effective in wiping out the data because CDs and DVDs are _________ media used to store large amounts of data and are not affected by the magnet.
A. Magnetic
B. Optical
C. Anti-Magnetic
D. Logical
-
Question 303:
When performing a forensics analysis, what device is used to prevent the system from recording data on an evidence disk?
A. Write-blocker
B. Protocol analyzer
C. Firewall
D. Disk editor
-
Question 304:
What file is processed at the end of a Windows XP boot to initialize the logon dialog box?
A. NTOSKRNL.EXE
B. NTLDR
C. LSASS.EXE
D. NTDETECT.COM
-
Question 305:
Davidson Trucking is a small transportation company that has three local offices in Detroit Michigan. Ten female employees that work for the company have gone to an attorney reporting that male employees repeatedly harassed them and that management did nothing to stop the problem. Davidson has employee policies that outline all company guidelines, including awareness on harassment and how it will not be tolerated. When the case is brought to court, whom should the prosecuting attorney call upon for not upholding company policy?
A. IT personnel
B. Employees themselves
C. Supervisors
D. Administrative assistant in charge of writing policies
-
Question 306:
The following is a log file screenshot from a default installation of IIS 6.0.
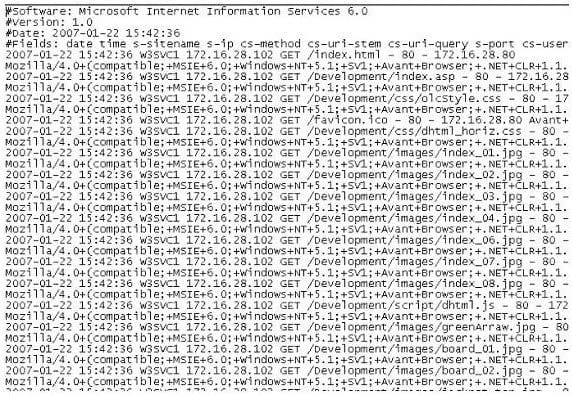
What time standard is used by IIS as seen in the screenshot?
A. UTC
B. GMT
C. TAI
D. UT
-
Question 307:
If the partition size Is 4 GB, each cluster will be 32 K. Even If a file needs only 10 K, the entire 32 K will be allocated, resulting In 22 K of___________.
A. Slack space
B. Deleted space
C. Cluster space
D. Sector space
-
Question 308:
The Recycle Bin exists as a metaphor for throwing files away, but it also allows user to retrieve and restore files. Once the file is moved to the recycle bin, a record is added to the log file that exists in the Recycle Bin.
Which of the following files contains records that correspond to each deleted file in the Recycle Bin?
A. INFO2 file
B. INFO1 file
C. LOGINFO2 file
D. LOGINFO1 file
-
Question 309:
Which of the following commands shows you the NetBIOS name table each?
A. nbtstat -n
B. nbtstat -c
C. nbtstat -r
D. nbtstat -s
-
Question 310:
Operating System logs are most beneficial for Identifying or Investigating suspicious activities involving a particular host. Which of the following Operating System logs contains information about operational actions performed by OS components?
A. Event logs
B. Audit logs
C. Firewall logs
D. IDS logs
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V9 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.