Exam Details
Exam Code
:312-49V9Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:531 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V9 Questions & Answers
-
Question 351:
Shortcuts are the files with the extension .Ink that are created and are accessed by the users. These files provide you with information about:
A. Files or network shares
B. Running application
C. Application logs
D. System logs
-
Question 352:
How do you define forensic computing?
A. It is the science of capturing, processing, and investigating data security incidents and making it acceptable to a court of law.
B. It is a methodology of guidelines that deals with the process of cyber investigation
C. It Is a preliminary and mandatory course necessary to pursue and understand fundamental principles of ethical hacking
D. It is the administrative and legal proceeding in the process of forensic investigation
-
Question 353:
Determine the message length from following hex viewer record:
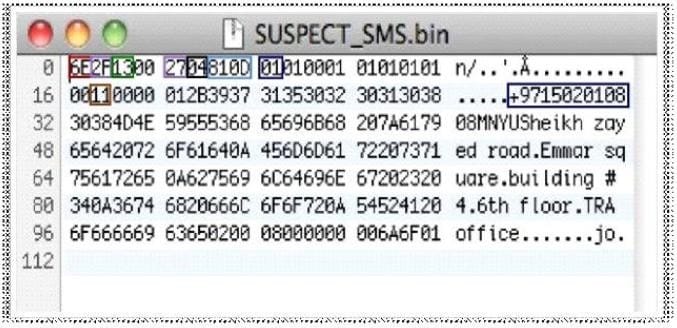
A. 6E2F
B. 13
C. 27
D. 810D
-
Question 354:
In Windows 7 system files, which file reads the Boot.ini file and loads Ntoskrnl.exe. Bootvid.dll. Hal.dll, and boot-start device drivers?
A. Ntldr
B. Gdi32.dll
C. Kernel32.dll
D. Boot.in
-
Question 355:
Consistency in the investigative report is more important than the exact format in the report to eliminate uncertainty and confusion.
A. True
B. False
-
Question 356:
All the Information about the user activity on the network, like details about login and logoff attempts, is collected in the security log of the computer. When a user's login is successful, successful audits generate an entry whereas unsuccessful audits generate an entry for failed login attempts in the logon event ID table.
In the logon event ID table, which event ID entry (number) represents a successful logging on to a computer?
A. 528
B. 529
C. 530
D. 531
-
Question 357:
Event correlation is a procedure that is assigned with a new meaning for a set of events that occur in a predefined interval of time.
Which type of correlation will you use if your organization wants to use different OS and network hardware platforms throughout the network?
A. Same-platform correlation
B. Cross-platform correlation
C. Multiple-platform correlation
D. Network-platform correlation
-
Question 358:
Jason, a renowned forensic investigator, is investigating a network attack that resulted in the compromise of several systems in a reputed multinational's network. He started Wireshark to capture the network traffic. Upon investigation, he found that the DNS packets travelling across the network belonged to a non-company configured IP. Which of the following attack Jason can infer from his findings?
A. DNS Poisoning
B. Cookie Poisoning Attack
C. DNS Redirection
D. Session poisoning
-
Question 359:
Ron. a computer forensics expert, Is Investigating a case involving corporate espionage. He has recovered several mobile computing devices from the crime scene. One of the evidence that Ron possesses is a mobile phone from Nokia that was left in on condition. Ron needs to recover the IMEI number of the device to establish the identity of the device owner. Which of the following key combinations he can use to recover the IMEI number?
A. #*06*#
B. *#06#
C. #06r
D. *1MEI#
-
Question 360:
Physical security recommendations: There should be only one entrance to a forensics lab
A. True
B. False
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V9 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.