Exam Details
Exam Code
:312-49V9Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:531 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V9 Questions & Answers
-
Question 411:
Web applications provide an Interface between end users and web servers through a set of web pages that are generated at the server-end or contain script code to be executed dynamically within the client Web browser.
A. True
B. False
-
Question 412:
Which of the following commands shows you the names of all open shared files on a server and number of file locks on each file?
A. Net sessions
B. Net file
C. Netconfig
D. Net share
-
Question 413:
BMP (Bitmap) is a standard file format for computers running the Windows operating system. BMP images can range from black and white (1 bit per pixel) up to 24 bit color (16.7 million colors). Each bitmap file contains header, the RGBQUAD array, information header, and image data. Which of the following element specifies the dimensions, compression type, and color format for the bitmap?
A. Header
B. The RGBQUAD array
C. Information header
D. Image data
-
Question 414:
Windows Security Accounts Manager (SAM) is a registry file which stores passwords in a hashed format. SAM file in Windows is located at:
A. C:\windows\system32\config\SAM
B. C:\windows\system32\con\SAM
C. C:\windows\system32\Boot\SAM
D. C:\windows\system32\drivers\SAM
-
Question 415:
Which table is used to convert huge word lists (i .e. dictionary files and brute-force lists) into password hashes?
A. Rainbow tables
B. Hash tables
C. Master file tables
D. Database tables
-
Question 416:
Data is striped at a byte level across multiple drives and parity information is distributed among all member drives.
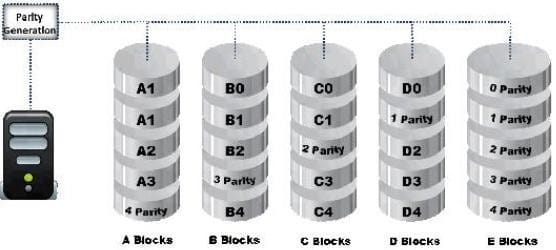
What RAID level is represented here?
A. RAID Level0
B. RAID Level 1
C. RAID Level 3
D. RAID Level 5
-
Question 417:
If a file (readme.txt) on a hard disk has a size of 2600 bytes, how many sectors are normally allocated to this file?
A. 4 Sectors
B. 5 Sectors
C. 6 Sectors
D. 7 Sectors
-
Question 418:
Which of the following file in Novel GroupWise stores information about user accounts?
A. ngwguard.db
B. gwcheck.db
C. PRIV.EDB
D. PRIV.STM
-
Question 419:
Which of the following statements is not a part of securing and evaluating electronic crime scene checklist?
A. Locate and help the victim
B. Transmit additional flash messages to other responding units
C. Request additional help at the scene if needed
D. Blog about the incident on the internet
-
Question 420:
Which of the following Steganography techniques allows you to encode information that ensures creation of cover for secret communication?
A. Substitution techniques
B. Transform domain techniques
C. Cover generation techniques
D. Spread spectrum techniques
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V9 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.