Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 161:
Jess the hacker runs L0phtCrack's built-in sniffer utility which grabs SMB password hashes and stores them for offline cracking. Once cracked, these passwords can provide easy access to whatever network resources the user account has
access to.
But Jess is not picking up hashed from the network.
Why?
A. The network protocol is configured to use SMB Signing.
B. The physical network wire is on fibre optic cable.
C. The network protocol is configured to use IPSEC.
D. L0phtCrack SMB filtering only works through Switches and not Hubs.
-
Question 162:
John is a keen administrator, and has followed all of the best practices as he could find on securing his Windows Server. He has renamed the Administrator account to a new name that he is sure cannot be easily guessed. However, there are people who already attempt to compromise his newly renamed administrator account.
How is it possible for a remote attacker to decipher the name of the administrator account if it has been renamed?
A. The attacker used the user2sid program.
B. The attacker used the sid2user program.
C. The attacker used nmap with the V switch.
D. The attacker guessed the new name.
-
Question 163:
SNMP is a protocol used to query hosts, servers, and devices about performance or health status data. This protocol has long been used by hackers to gather great amount of information about remote hosts.
Which of the following features makes this possible? (Choose two)
A. It used TCP as the underlying protocol.
B. It uses community string that is transmitted in clear text.
C. It is susceptible to sniffing.
D. It is used by all network devices on the market.
-
Question 164:
Sandra has been actively scanning the client network on which she is doing a vulnerability assessment test. While conducting a port scan she notices open ports in the range of 135 to 139. What protocol is most likely to be listening on those ports?
A. Finger
B. FTP
C. Samba
D. SMB
-
Question 165:
You have successfully brute forced basic authentication configured on a Web Server using Brutus hacking tool. The username/password is "Admin" and "Bettlemani@". You logon to the system using the brute forced password and plant
backdoors and rootkits.
After downloading various sensitive documents from the compromised machine, you proceed to clear the log files to hide your trace..
Which event log located at C:\Windows\system32\config contains the trace of your brute force attempts?
A. AppEvent.Evt
B. SecEvent.Evt
C. SysEvent.Evt
D. WinEvent.Evt
-
Question 166:
Michael is the security administrator for the for ABC company. Michael has been charged with strengthening the company's security policies, including its password policies. Due to certain legacy applications. Michael was only able to enforce a password group policy in Active Directory with a minimum of 10 characters. He has informed the company's employes, however that the new password policy requires that everyone must have complex passwords with at least 14 characters. Michael wants to ensure that everyone is using complex passwords that meet the new security policy requirements. Michael has just logged on to one of the network's domain controllers and is about to run the following command:
What will this command accomplish?
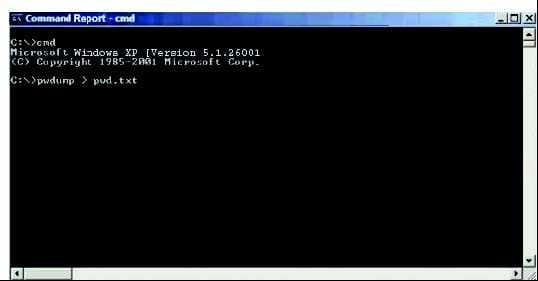
A. Dumps SAM password hashes to pwd.txt
B. Password history file is piped to pwd.txt
C. Dumps Active Directory password hashes to pwd.txt
D. Internet cache file is piped to pwd.txt
-
Question 167:
John Beetlesman, the hacker has successfully compromised the Linux System of Agent Telecommunications, Inc's WebServer running Apache. He has downloaded sensitive documents and database files off the machine.
Upon performing various tasks, Beetlesman finally runs the following command on the Linux box before disconnecting.
for ((i=0;i<1;i++));do
?dd if=/dev/random of=/dev/hda andand dd if=/dev/zero of=/dev/hda done
What exactly is John trying to do?
A. He is making a bit stream copy of the entire hard disk for later download
B. He is deleting log files to remove his trace
C. He is wiping the contents of the hard disk with zeros
D. He is infecting the hard disk with random virus strings
-
Question 168:
You are the security administrator for a large online auction company based out of Los Angeles. After getting your ENSA CERTIFICATION last year, you have steadily been fortifying your network's security including training OS hardening and network security. One of the last things you just changed for security reasons was to modify all the built-in administrator accounts on the local computers of PCs and in Active Directory. After through testing you found and no services or programs were affected by the name changes.
Your company undergoes an outside security audit by a consulting company and they said that even through all the administrator account names were changed, the accounts could still be used by a clever hacker to gain unauthorized access. You argue with the auditors and say that is not possible, so they use a tool and show you how easy it is to utilize the administrator account even though its name was changed.
What tool did the auditors use?
A. sid2user
B. User2sid
C. GetAcct
D. Fingerprint
-
Question 169:
You are the IT Manager of a large legal firm in California. Your firm represents many important clients whose names always must remain anonymous to the public. Your boss, Mr. Smith is always concerned about client information being leaked or revealed to the pres or public. You have just finished a complete security overhaul of your information system including an updated IPS, new firewall, email encryption and employee security awareness training. Unfortunately, many of your firm's clients do not trust technology to completely secure their information, so couriers routinely have to travel back and forth to and from the office with sensitive information.
Your boss has charged you with figuring out how to secure the information the couriers must transport. You propose that the data be transferred using burned CD's or USB flash drives. You initially think of encrypting the files, but decide against that method for fear the encryption keys could eventually be broken.
What software application could you use to hide the data on the CD's and USB flash drives?
A. Snow
B. File Snuff
C. File Sneaker
D. EFS
-
Question 170:
Which of the following is an attack in which a secret value like a hash is captured and then reused at a later time to gain access to a system without ever decrypting or decoding the hash.
A. Replay Attacks
B. Brute Force Attacks
C. Cryptography Attacks
D. John the Ripper Attacks
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.