Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 211:
Which of the following algorithms can be used to guarantee the integrity of messages being sent, in transit, or stored? (Choose the best answer)
A. symmetric algorithms
B. asymmetric algorithms
C. hashing algorithms
D. integrity algorithms
-
Question 212:
Study the snort rule given below:
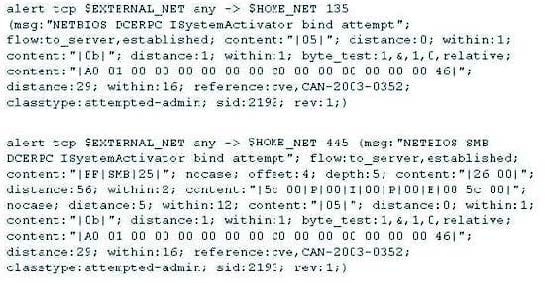
From the options below, choose the exploit against which this rule applies.
A. WebDav
B. SQL Slammer
C. MS Blaster
D. MyDoom
-
Question 213:
Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and key loggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his clients hosts and servers.
A. Hardware, Software, and Sniffing.
B. Hardware and Software Keyloggers.
C. Passwords are always best obtained using Hardware key loggers.
D. Software only, they are the most effective.
-
Question 214:
If a token and 4-digit personal identification number (PIN) are used to access a computer system and the token performs off-line checking for the correct PIN, what type of attack is possible?
A. Birthday
B. Brute force
C. Man-in-the-middle
D. Smurf
-
Question 215:
You are writing an antivirus bypassing Trojan using C++ code wrapped into chess.c to create an executable file chess.exe. This Trojan when executed on the victim machine, scans the entire system (c:\) for data with the following text "Credit Card" and "password". It then zips all the scanned files and sends an email to a predefined hotmail address. You want to make this Trojan persistent so that it survives computer reboots. Which registry entry will you add a key to make it persistent?
A. HKEY_LOCAL_MACHINE\SOFTWARE\MICROOSFT\Windows\CurrentVersion\RunServices
B. HKEY_LOCAL_USER\SOFTWARE\MICROOSFT\Windows\CurrentVersion\RunServices
C. HKEY_LOCAL_SYSTEM\SOFTWARE\MICROOSFT\Windows\CurrentVersion\RunServices
D. HKEY_CURRENT_USER\SOFTWARE\MICROOSFT\Windows\CurrentVersion\RunServices
-
Question 216:
John wants to try a new hacking tool on his Linux System. As the application comes from a site in his untrusted zone, John wants to ensure that the downloaded tool has not been Trojaned. Which of the following options would indicate the best course of action for John?
A. Obtain the application via SSL
B. Obtain the application from a CD-ROM disc
C. Compare the files' MD5 signature with the one published on the distribution media
D. Compare the file's virus signature with the one published on the distribution media
-
Question 217:
William has received a Tetris game from someone in his computer programming class through email. William does not really know the person who sent the game very well, but decides to install the game anyway because he really likes Tetris.
After William installs the game, he plays it for a couple of hours. The next day, William plays the Tetris game again and notices that his machines have begun to slow down. He brings up his Task Manager and sees the following programs
running (see Screenshot):
What has William just installed?
A. Remote Access Trojan (RAT)
B. Zombie Zapper (ZoZ)
C. Bot IRC Tunnel (BIT)
D. Root Digger (RD)
-
Question 218:
Spears Technology, Inc is a software development company located in Los Angeles, California. They reported a breach in security, stating that its "security defenses has been breached and exploited for 2 weeks by hackers. "The hackers had
accessed and downloaded 90,000 address containing customer credit cards and password. Spears Technology found this attack to be so to law enforcement officials to protect their intellectual property.
How did this attack occur? The intruder entered through an employees home machine, which was connected to Spears Technology, Inc's corporate VPN network. The application called BEAST Trojan was used in the attack to open a "Back
Door" allowing the hackers undetected access. The security breach was discovered when customers complained about the usage of their credit cards without their knowledge.
The hackers were traced back to Beijing China through e-mail address evidence. The credit card information was sent to that same e-mail address. The passwords allowed the hackers to access Spears Technology's network from a remote
location, posing as employees. The intent of the attacker was to steal the source code for their VOIP system and "hold it hostage" from Spears Technology, Inc exchange for ransom.
The hackers had intended on selling the stolen VOIP software source code to competitors.
How would you prevent such attacks from occurring in the future at Spears Technology?
A. Disable VPN access to all your employees from home machines
B. Allow VPN access but replace the standard authentication with biometric authentication
C. Replace the VPN access with dial-up modem access to the company's network
D. Enable 25 character complex password policy for employees to access the VPN network.
-
Question 219:
Which definition below best describes a covert channel?
A. Making use of a Protocol in a way it was not intended to be used
B. It is the multiplexing taking place on communication link
C. It is one of the weak channels used by WEP that makes it insecure
D. A Server Program using a port that is not well known
-
Question 220:
Erik notices a big increase in UDP packets sent to port 1026 and 1027 occasionally. He enters the following at the command prompt.
$ nc -l -p 1026 -u -v
In response, he sees the following message.
cell(?(c)????STOPALERT77STOP! WINDOWS REQUIRES IMMEDIATE ATTENTION.
Windows has found 47 Critical Errors.
To fix the errors please do the following:
1.
Download Registry Repair from: www.reg-patch.com
2.
Install Registry Repair
3.
Run Registry Repair
4.
Reboot your computer
FAILURE TO ACT NOW MAY LEAD TO DATA LOSS AND CORRUPTION!
What would you infer from this alert?
A. The machine is redirecting traffic to www.reg-patch.com using adware
B. It is a genuine fault of windows registry and the registry needs to be backed up
C. An attacker has compromised the machine and backdoored ports 1026 and 1027
D. It is a messenger spam. Windows creates a listener on one of the low dynamic ports from 1026 to 1029 and the message usually promotes malware disguised as legitimate utilities
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.