Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 261:
Exhibit:
ettercap NCLzs --quiet
What does the command in the exhibit do in "Ettercap"?
A. This command will provide you the entire list of hosts in the LAN
B. This command will check if someone is poisoning you and will report its IP.
C. This command will detach from console and log all the collected passwords from the network to a file.
D. This command broadcasts ping to scan the LAN instead of ARP request of all the subnet IPs.
-
Question 262:
Steven, a security analyst for XYZ associates, is analyzing packets captured by Ethereal on a Linux Server inside his network when the server starts to slow down tremendously. Steven examines the following Ethereal captures: A. Smurf Attack
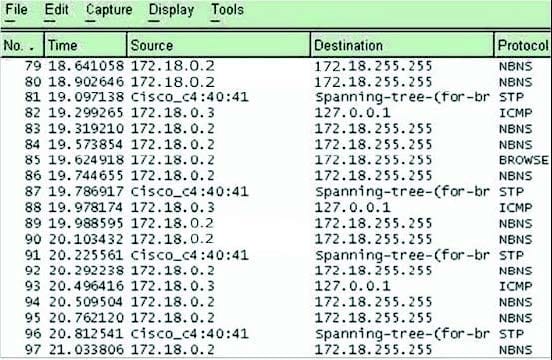
B. ARP Spoofing
C. Ping of Death
D. SYN Flood
-
Question 263:
Smurf is a simple attack based on IP spoofing and broadcasts. A single packet (such as an ICMP Echo Request) is sent as a directed broadcast to a subnet on the Internet. All the machines on that subnet respond to this broadcast. By
spoofing the source IP Address of the packet, all the responses will get sent to the spoofed IP Address. Thus, a hacker can often flood a victim with hundreds of responses for every request the hacker sends out.
Who are the primary victims of these attacks on the Internet today?
A. IRC servers are the primary victim to smurf attacks
B. IDS devices are the primary victim to smurf attacks
C. Mail Servers are the primary victim to smurf attacks
D. SPAM filters are the primary victim to surf attacks
-
Question 264:
Bryce the bad boy is purposely sending fragmented ICMP packets to a remote target. The tool size of this ICMP packet once reconstructed is over 65,536 bytes. From the information given, what type of attack is Bryce attempting to perform?
A. Smurf
B. Fraggle
C. SYN Flood
D. Ping of Death
-
Question 265:
Hackers usually control Bots through:
A. IRC Channel
B. MSN Messenger
C. Trojan Client Software
D. Yahoo Chat
E. GoogleTalk
-
Question 266:
The SYN Flood attack sends TCP connections requests faster than a machine can process them.
Attacker creates a random source address for each packet. SYN flag set in each packet is a request to open a new connection to the server from the spoofed IP Address Victim responds to spoofed IP Address then waits for confirmation that never arrives (timeout wait is about 3 minutes) Victim's connection table fills up waiting for replies and ignores new connection legitimate users are ignored and will not be able to access the server
How do you protect your network against SYN Flood attacks?
A. SYN cookies. Instead of allocating a record, send a SYN-ACK with a carefully constructed sequence number generated as a hash of the clients IP Address port number and other information. When the client responds with a normal ACK, that special sequence number will be included, which the server then verifies. Thus the server first allocates memory on the third packet of the handshake, not the first.
B. RST cookies The server sends a wrong SYN|ACK back to the client. The client should then generate a RST packet telling the server that something is wrong. At this point, the server knows the client is valid and will now accept incoming connections from that client normally.
C. Micro Blocks. Instead of allocating a complete connection, simply allocate a micro-record of 16- bytes for the incoming SYN object.
D. Stack Tweaking. TCP can be tweaked in order to reduce the effect of SYN floods. Reduce the timeout before a stack frees up the memory allocated for a connection.
-
Question 267:
Peter has been monitoring his IDS and sees that there are a huge number of ICMP Echo Reply packets that are being received on the External Gateway interface. Further inspection reveals they are not responses from internal hosts request but simply responses coming from the Internet. What could be the likely cause of this?
A. Someone Spoofed Peter's IP Address while doing a land attack
B. Someone Spoofed Peter's IP Address while doing a DoS attack
C. Someone Spoofed Peter's IP Address while doing a smurf Attack
D. Someone Spoofed Peter's IP address while doing a fraggle attack
-
Question 268:
Peter is a Network Admin. He is concerned that his network is vulnerable to a smurf attack. What should Peter do to prevent a smurf attack? Select the best answer.
A. He should disable unicast on all routers
B. Disable multicast on the router
C. Turn off fragmentation on his router
D. Make sure all anti-virus protection is updated on all systems
E. Make sure his router won't take a directed broadcast
-
Question 269:
Eve decides to get her hands dirty and tries out a Denial of Service attack that is relatively new to her. This time she envisages using a different kind of method to attack Brownies Inc. Eve tries to forge the packets and uses the broadcast address. She launches an attack similar to that of fraggle. What is the technique that Eve used in the case above?
A. Smurf
B. Bubonic
C. SYN Flood
D. Ping of Death
-
Question 270:
Henry is an attacker and wants to gain control of a system and use it to flood a target system with requests, so as to prevent legitimate users from gaining access. What type of attack is Henry using?
A. Henry is executing commands or viewing data outside the intended target path
B. Henry is using a denial of service attack which is a valid threat used by an attacker
C. Henry is taking advantage of an incorrect configuration that leads to access with higher-than- expected privilege
D. Henry uses poorly designed input validation routines to create or alter commands to gain access to unintended data or execute commands
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.