Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 341:
You have successfully run a buffer overflow attack against a default IIS installation running on a Windows 2000 Server. The server allows you to spawn a shell. In order to perform the actions you intend to do, you need elevated permission. You need to know what your current privileges are within the shell. Which of the following options would be your current privileges?
A. Administrator
B. IUSR_COMPUTERNAME
C. LOCAL_SYSTEM
D. Whatever account IIS was installed with
-
Question 342:
Sara is making use of Digest Authentication for her Web site. Why is this considered to be more secure than Basic authentication?
A. Basic authentication is broken
B. The password is never sent in clear text over the network
C. The password sent in clear text over the network is never reused.
D. It is based on Kerberos authentication protocol
-
Question 343:
Consider the following code:
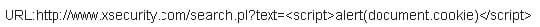
If an attacker can trick a victim user to click a link like this and the web application does not validate input, then the victim's browser will pop up an alert showing the users current set of cookies. An attacker can do much more damage, including stealing passwords, resetting your home page or redirecting the user to another web site.
What is the countermeasure against XSS scripting?
A. Create an IP access list and restrict connections based on port number
B. Replace "<" and ">" characters with ?lt; and ?gt; using server scripts
C. Disable Javascript in IE and Firefox browsers
D. Connect to the server using HTTPS protocol instead of HTTP
-
Question 344:
Annie has just succeeded is stealing a secure cookie via a XSS attack. She is able to replay the cookie even while the session is valid on the server. Why do you think this is possible?
A. Any Cookie can be replayed irrespective of the session status
B. The scenario is invalid as a secure cookie can't be replayed
C. It works because encryption is performed at the network layer (layer 1 encryption)
D. It works because encryption is performed at the application layer (Single Encryption Key)
-
Question 345:
What attack is being depicted here?
A. Cookie Stealing
B. Session Hijacking
C. Cross Site scripting
D. Parameter Manipulation
-
Question 346:
The GET method should never be used when sensitive data such as credit is being sent to a CGI program. This is because any GET command will appear in the URL and will be logged by any servers. For example, let's say that you've
entered your credit card information into a form that uses the GET method. The URL may appear like this:
https://www.xsecurity-bank.com/creditcard.asp?cardnumber=454543433532234 The GET method appends the credit card number to the URL. This means that anyone with access to a server log will be able to obtain this information.
How would you protect from this type of attack?
A. Replace the GET with POST method when sending data
B. Never include sensitive information in a script
C. Use HTTOS SSLV3 to send the data instead of plain HTTPS
D. Encrypt the data before you send using GET method
-
Question 347:
Say that "abigcompany.com" had a security vulnerability in the javascript on their website in the past. They recently fixed the security vulnerability, but it had been there for many months. Is there some way to 4go back and see the code for that error? Select the best answer.
A. archive.org
B. There is no way to get the changed webpage unless you contact someone at the company
C. Usenet
D. Javascript would not be in their html so a service like usenet or archive wouldn't help you
-
Question 348:
_____ ensures that the enforcement of organizational security policy does not rely on voluntary web application user compliance. It secures information by assigning sensitivity labels on information and comparing this to the level of security a user is operating at.
A. Mandatory Access Control
B. Authorized Access Control
C. Role-based Access Control
D. Discretionary Access Control
-
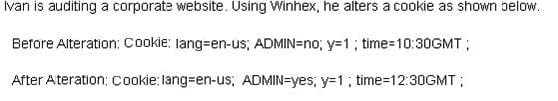
Question 349:
Ivan is auditing a corporate website. Using Winhex, he alters a cookie as shown below.
Before Alteration: Cookie: lang=en-us; ADMIN=no; y=1 ; time=10:30GMT ;
After Alteration: Cookie: lang=en-us; ADMIN=yes; y=1 ; time=12:30GMT ;
What attack is being depicted here?
A. Cookie Stealing
B. Session Hijacking
C. Cross Site Scripting
D. Parameter Manipulation
-
Question 350:
Jane has just accessed her preferred e-commerce web site and she has seen an item she would like to buy. Jane considers the price a bit too steep; she looks at the page source code and decides to save the page locally to modify some of the page variables. In the context of web application security, what do you think Jane has changed?
A. An integer variable
B. A 'hidden' price value
C. A 'hidden' form field value
D. A page cannot be changed locally; it can only be served by a web server
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.