Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 371:
Jimmy, an attacker, knows that he can take advantage of poorly designed input validation routines to create or alter SQL commands to gain access to private data or execute commands in the database. What technique does Jimmy use to compromise a database?
A. Jimmy can submit user input that executes an operating system command to compromise a target system
B. Jimmy can utilize this particular database threat that is an SQL injection technique to penetrate a target system
C. Jimmy can utilize an incorrect configuration that leads to access with higher-than-expected privilege of the database
D. Jimmy can gain control of system to flood the target system with requests, preventing legitimate users from gaining access
-
Question 372:
A particular database threat utilizes a SQL injection technique to penetrate a target system. How would an attacker use this technique to compromise a database?
A. An attacker uses poorly designed input validation routines to create or alter SQL commands to gain access to unintended data or execute commands of the database
B. An attacker submits user input that executes an operating system command to compromise a target system
C. An attacker gains control of system to flood the target system with requests, preventing legitimate users from gaining access
D. An attacker utilizes an incorrect configuration that leads to access with higher-than-expected privilege of the database
-
Question 373:
Central Frost Bank was a medium-sized, regional financial institution in New York. The bank recently deployed a new Internet-accessible Web application. Using this application, Central Frost's customers could access their account balances, transfer money between accounts, pay bills and conduct online financial business through a Web browser. John Stevens was in charge of information security at Central Frost Bank. After one month in production, the Internet banking application was the subject of several customer complaints. Mysteriously, the account balances ofmany of Central Frost's customers had been changed! However, moneyhadn't been removed from the bank. Instead, money was transferred between accounts. Given this attack profile, John Stevens reviewed the Web application's logs and found the following entries:
Attempted login of unknown user: johnm Attempted login of unknown user: susaR Attempted login of unknown user: sencat Attempted login of unknown user: pete''; Attempted login of unknown user: ' or 1=1-Attempted login of unknown user: '; drop table logins-Login of user jason, sessionID= 0x75627578626F6F6B Login of user daniel, sessionID= 0x98627579539E13BE Login of user rebecca, sessionID= 0x9062757944CCB811 Login of user mike, sessionID= 0x9062757935FB5C64 Transfer Funds user jason Pay Bill user mike Logout of user mike
What type of attack did the Hacker attempt?
A. Brute force attack in which the Hacker attempted guessing login ID and password from password cracking tools.
B. The Hacker used a random generator module to pass results to the Web server and exploited Web application CGI vulnerability.
C. The Hacker attempted SQL Injection technique to gain access to a valid bank login ID.
D. The Hacker attempted Session hijacking, in which the Hacker opened an account with the bank, then logged in to receive a session ID, guessed the next ID and took over Jason's session.
-
Question 374:
When a malicious hacker identifies a target and wants to eventually compromise this target, what would be among the first steps that he would perform? (Choose the best answer)
A. Cover his tracks by eradicating the log files and audit trails.
B. Gain access to the remote computer in order to conceal the venue of attacks.
C. Perform a reconnaissance of the remote target for identical of venue of attacks.
D. Always begin with a scan in order to quickly identify venue of attacks.
-
Question 375:
Which of the following activities will not be considered passive footprinting?
A. Go through the rubbish to find out any information that might have been discarded
B. Search on financial site such as Yahoo Financial to identify assets
C. Scan the range of IP address found in the target DNS database
D. Perform multiples queries using a search engine
-
Question 376:
Your boss is attempting to modify the parameters of a Web-based application in order to alter the SQL statements that are parsed to retrieve data from the database. What would you call such an attack?
A. SQL Input attack
B. SQL Piggybacking attack
C. SQL Select attack
D. SQL Injection attack
-
Question 377:
Exhibit:
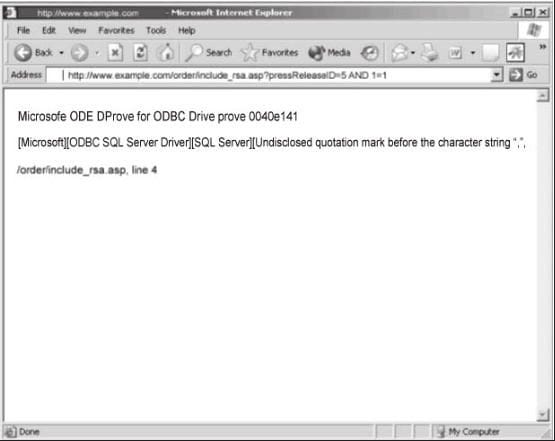
You are conducting pen-test against a company's website using SQL Injection techniques. You enter "anuthing or 1=1-" in the username filed of an authentication form. This is the output returned from the server.
What is the next step you should do?
A. Identify the user context of the web application by running_http://www.example.com/order/include_rsa_asp?pressReleaseID=5ANDUSER_NAME() = `dbo'
B. Identify the database and table name by running:http://www.example.com/order/include_rsa.asp? pressReleaseID=5ANDascii(lower(substring((SELECT TOP 1 name FROM sysobjects WHERExtype='U'),1))) > 109
C. Format the C: drive and delete the database by running:http://www.example.com/order/include_rsa.asp?pressReleaseID=5 ANDxp_cmdshell `format
c: /q /yes `; drop database myDB; -
D. Reboot the web server by running:http://www.example.com/order/include_rsa.asp? pressReleaseID=5AND xp_cmdshell `iisreset reboot'; -
-
Question 378:
Bob has been hired to do a web application security test. Bob notices that the site is dynamic and infers that they mist be making use of a database at the application back end. Bob wants to validate whether SQL Injection would be possible.
What is the first character that Bob should use to attempt breaking valid SQL requests?
A. Semi Column
B. Double Quote
C. Single Quote
D. Exclamation Mark
-
Question 379:
Bill is attempting a series of SQL queries in order to map out the tables within the database that he is trying to exploit.
Choose the attack type from the choices given below.
A. Database Fingerprinting
B. Database Enumeration
C. SQL Fingerprinting
D. SQL Enumeration
-
Question 380:
Bank of Timbuktu was a medium-sized, regional financial institution in Timbuktu. The bank has deployed a new Internet-accessible Web application recently, using which customers could access their account balances, transfer money between accounts, pay bills and conduct online financial business using a Web browser.
John Stevens was in charge of information security at Bank of Timbuktu. After one month in production, several customers complained about the Internet enabled banking application. Strangely, the account balances of many bank's customers has been changed! However, money hadn't been removed from the bank. Instead, money was transferred between accounts. Given this attack profile, John Stevens reviewed the Web application's logs and found the following entries:
Attempted login of unknown user: John Attempted login of unknown user: sysaR Attempted login of unknown user: sencat Attempted login of unknown user: pete `'; Attempted login of unknown user: ` or 1=1-Attempted login of unknown user: `; drop table logins-- Login of user jason, sessionID= 0x75627578626F6F6B Login of user daniel, sessionID= 0x98627579539E13BE Login of user rebecca, sessionID= 0x90627579944CCB811 Login of user mike, sessionID= 0x9062757935FB5C64 Transfer Funds user jason Pay Bill user mike Logout of user mike
What kind of attack did the Hacker attempt to carry out at the bank? (Choose the best answer)
A. The Hacker attempted SQL Injection technique to gain access to a valid bank login ID.
B. The Hacker attempted Session hijacking, in which the Hacker opened an account with the bank, then logged in to receive a session ID, guessed the next ID and took over Jason's session.
C. The Hacker attempted a brute force attack to guess login ID and password using password cracking tools.
D. The Hacker used a random generator module to pass results to the Web server and exploited Web application CGI vulnerability.
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.