Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 451:
An Employee wants to bypass detection by a network-based IDS application and does not want to attack the system containing the IDS application. Which of the following strategies can the employee use to evade detection by the network based IDS application?
A. Create a ping flood
B. Create a SYN flood
C. Create a covert network tunnel
D. Create multiple false positives
-
Question 452:
Blake is in charge of securing all 20 of his company's servers. He has enabled hardware and software firewalls, hardened the operating systems and disabled all unnecessary service on all the servers. Unfortunately, there is proprietary
AS400 emulation software that must run on one of the servers that requires the telnet service to function properly. Blake is especially concerned about his since telnet can be a very large security risk in an organization. Blake is concerned
about how his particular server might look to an outside attacker so he decides to perform some footprinting scanning and penetration tests on the server. Blake telents into the server and types the following command:
HEAD/HTTP/1.0
After pressing enter twice, Blake gets the following results:
What has the Blake just accomplished?
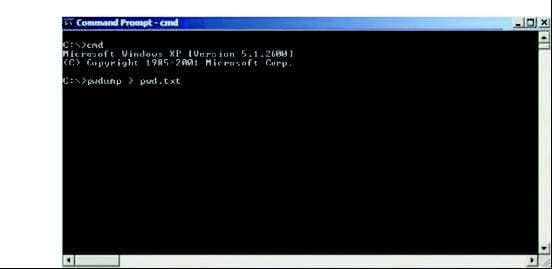
A. Grabbed the banner
B. Downloaded a file to his local computer
C. Submitted a remote command to crash the server
D. Poisoned the local DNS cache of the server
-
Question 453:
What is the advantage in encrypting the communication between the agent and the monitor in an Intrusion Detection System?
A. Encryption of agent communications will conceal the presence of the agents
B. The monitor will know if counterfeit messages are being generated because they will not be encrypted
C. Alerts are sent to the monitor when a potential intrusion is detected
D. An intruder could intercept and delete data or alerts and the intrusion can go undetected
-
Question 454:
What is the purpose of firewalking?
A. It's a technique used to discover Wireless network on foot
B. It's a technique used to map routers on a network link
C. It's a technique used to discover interface in promiscuous mode
D. It's a technique used to discover what rules are configured on a gateway
-
Question 455:
An Evil Cracker is attempting to penetrate your private network security. To do this, he must not be seen by your IDS, as it may take action to stop him. What tool might he use to bypass the IDS? Select the best answer.
A. Firewalk
B. Manhunt
C. Fragrouter
D. Fragids
-
Question 456:
There are two types of honeypots- high and low interaction. Which of these describes a low interaction honeypot? Select the best answers.
A. Emulators of vulnerable programs
B. More likely to be penetrated
C. Easier to deploy and maintain
D. Tend to be used for production
E. More detectable
F. Tend to be used for research
-
Question 457:
Exhibit: Given the following extract from the snort log on a honeypot, what service is being exploited? :
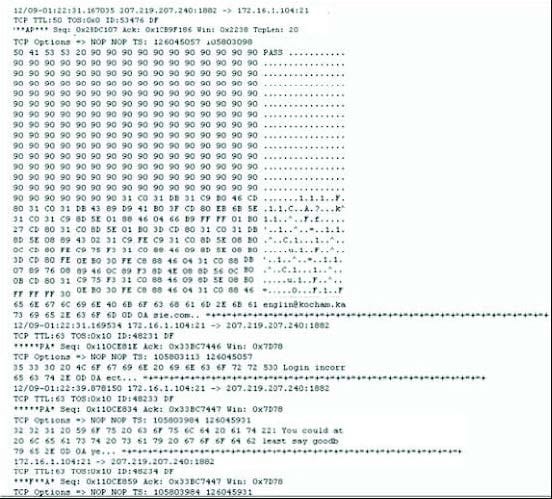
A. FTP
B. SSH
C. Telnet
D. SMTP
-
Question 458:
Exhibit:
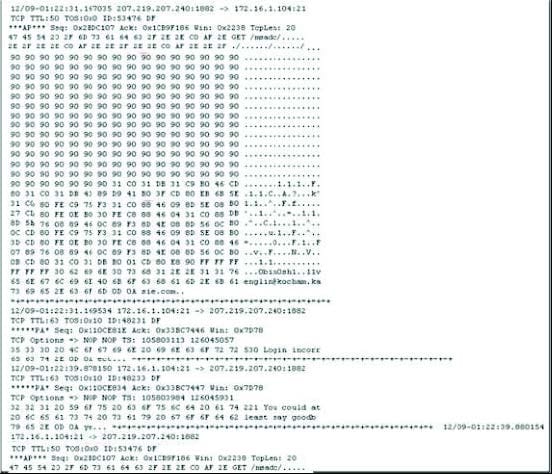
Given the following extract from the snort log on a honeypot, what do you infer from the attack?
A. A new port was opened
B. A new user id was created
C. The exploit was successful
D. The exploit was not successful
-
Question 459:
Which of the following countermeasure can specifically protect against both the MAC Flood and MAC Spoofing attacks?
A. Port Security
B. Switch Mapping
C. Port Reconfiguring
D. Multiple Recognition
-
Question 460:
A program that defends against a port scanner will attempt to:
A. Sends back bogus data to the port scanner
B. Log a violation and recommend use of security-auditing tools
C. Limit access by the scanning system to publicly available ports only
D. Update a firewall rule in real time to prevent the port scan from being completed
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.