Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 561:
Jeremy is web security consultant for Information Securitas. Jeremy has just been hired to perform contract work for a large state agency in Michigan. Jeremy's first task is to scan all the company's external websites. Jeremy comes upon a login page which appears to allow employees access to sensitive areas on the website. James types in the following statement in the username field:
SELECT * from Users where username='admin' ?AND password='' AND email like '%@testers.com%'
What will the SQL statement accomplish?
A. If the page is susceptible to SQL injection, it will look in the Users table for usernames of admin
B. This statement will look for users with the name of admin, blank passwords, and email addresses that end in @testers.com
C. This Select SQL statement will log James in if there are any users with NULL passwords
D. James will be able to see if there are any default user accounts in the SQL database
-
Question 562:
You want to perform advanced SQL Injection attack against a vulnerable website. You are unable to perform command shell hacks on this server. What must be enabled in SQL Server to launch these attacks?
A. System services
B. EXEC master access
C. xp_cmdshell
D. RDC
-
Question 563:
Kevin is an IT security analyst working for Emerson Time Makers, a watch manufacturing company in Miami. Kevin and his girlfriend Katy recently broke up after a big fight. Kevin believes that she was seeing another person. Kevin, who has an online email account that he uses for most of his mail, knows that Katy has an account with that same company. Kevin logs into his email account online and gets the following URL after successfully logged in: http:// www.youremailhere.com/ mail.asp? mailbox=KevinandSmith=121%22 Kevin changes the URL to: http://www.youremailhere.com/mail.asp? mailbox=KatyandSanchez=121%22 Kevin is trying to access her email account to see if he can find out any information. What is Kevin attempting here to gain access to Katy's mailbox?
A. This type of attempt is called URL obfuscation when someone manually changes a URL to try and gain unauthorized access
B. By changing the mailbox's name in the URL, Kevin is attempting directory transversal
C. Kevin is trying to utilize query string manipulation to gain access to her email account
D. He is attempting a path-string attack to gain access to her mailbox
-
Question 564:
Blane is a security analyst for a law firm. One of the lawyers needs to send out an email to a client but he wants to know if the email is forwarded on to any other recipients. The client is explicitly asked not to re-send the email since that would be a violation of the lawyer's and client's agreement for this particular case. What can Blane use to accomplish this?
A. He can use a split-DNS service to ensure the email is not forwarded on.
B. A service such as HTTrack would accomplish this.
C. Blane could use MetaGoofil tracking tool.
D. Blane can use a service such as ReadNotify tracking tool.
-
Question 565:
Harold just got home from working at Henderson LLC where he works as an IT technician. He was able to get off early because they were not too busy. When he walks into his home office, he notices his teenage daughter on the computer, apparently chatting with someone online. As soon as she hears Harold enter the room, she closes all her windows and tries to act like she was playing a game. When Harold asks her what she was doing, she acts very nervous and does not give him a straight answer. Harold is very concerned because he does not want his daughter to fall victim to online predators and the sort. Harold doesn't necessarily want to install any programs that will restrict the sites his daughter goes to, because he doesn't want to alert her to his trying to figure out what she is doing. Harold wants to use some kind of program that will track her activities online, and send Harold an email of her activity once a day so he can see what she has been up to. What kind of software could Harold use to accomplish this?
A. Install hardware Keylogger on her computer
B. Install screen capturing Spyware on her computer
C. Enable Remote Desktop on her computer
D. Install VNC on her computer
-
Question 566:
Which of the following represent weak password? (Select 2 answers)
A. Passwords that contain letters, special characters, and numbers Example: ap1$%##f@52
B. Passwords that contain only numbers Example: 23698217
C. Passwords that contain only special characters Example: and*#@!(%)
D. Passwords that contain letters and numbers Example: meerdfget123
E. Passwords that contain only letters Example: QWERTYKLRTY
F. Passwords that contain only special characters and numbers Example: 123@$45
G. Passwords that contain only letters and special characters Example: bob@andba
H. Passwords that contain Uppercase/Lowercase from a dictionary list Example: OrAnGe
-
Question 567:
Neil is an IT security consultant working on contract for Davidson Avionics. Neil has been hired to audit the network of Davidson Avionics. He has been given permission to perform any tests necessary. Neil has created a fake company ID badge and uniform. Neil waits by one of the company's entrance doors and follows an employee into the office after they use their valid access card to gain entrance. What type of social engineering attack has Neil employed here?
A. Neil has used a tailgating social engineering attack to gain access to the offices
B. He has used a piggybacking technique to gain unauthorized access
C. This type of social engineering attack is called man trapping
D. Neil is using the technique of reverse social engineering to gain access to the offices of Davidson Avionics
-
Question 568:
Here is the ASCII Sheet.
You want to guess the DBO username juggyboy (8 characters) using Blind SQL Injection technique.
What is the correct syntax?
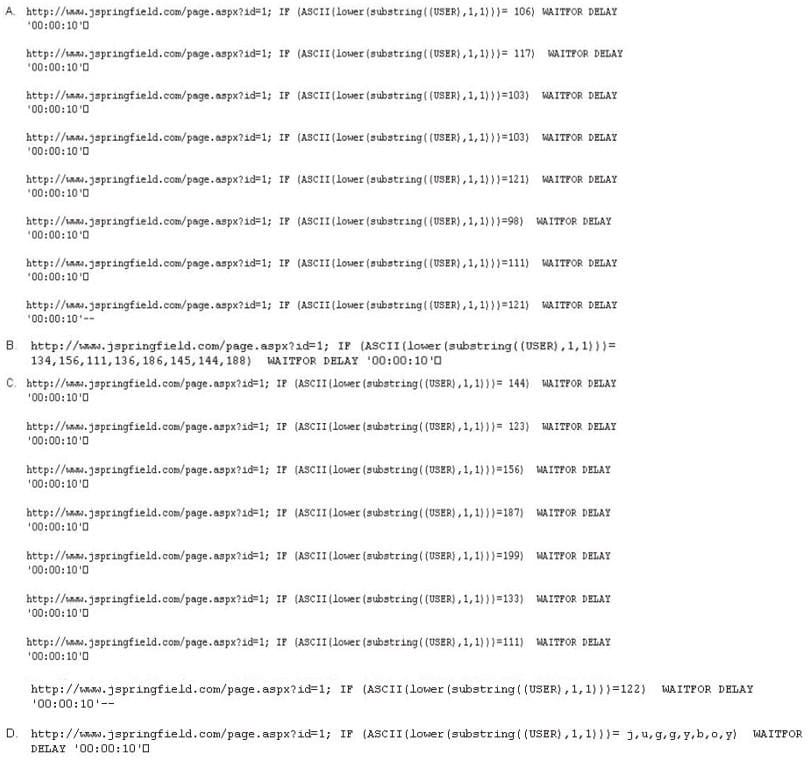
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 569:
How do you defend against ARP Poisoning attack? (Select 2 answers)

A. Enable DHCP Snooping Binding Table
B. Restrict ARP Duplicates
C. Enable Dynamic ARP Inspection
D. Enable MAC snooping Table
-
Question 570:
Wayne is the senior security analyst for his company. Wayne is examining some traffic logs on a server and came across some inconsistencies. Wayne finds some IP packets from a computer purporting to be on the internal network. The packets originate from 192.168.12.35 with a TTL of 15. The server replied to this computer and received a response from 192.168.12.35 with a TTL of 21. What can Wayne infer from this traffic log?
A. The initial traffic from 192.168.12.35 was being spoofed.
B. The traffic from 192.168.12.25 is from a Linux computer.
C. The TTL of 21 means that the client computer is on wireless.
D. The client computer at 192.168.12.35 is a zombie computer.
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.