Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 611:
"Testing the network using the same methodologies and tools employed by attackers" Identify the correct terminology that defines the above statement.
A. Vulnerability Scanning
B. Penetration Testing
C. Security Policy Implementation
D. Designing Network Security
-
Question 612:
ViruXine.W32 virus hides their presence by changing the underlying executable code. This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.
Here is a section of the Virus code:

What is this technique called?
A. Polymorphic Virus
B. Metamorphic Virus
C. Dravidic Virus
D. Stealth Virus
-
Question 613:
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN
number and other personal details. Ignorant users usually fall prey to this scam.
Which of the following statement is incorrect related to this attack?
A. Do not reply to email messages or popup ads asking for personal or financial information
B. Do not trust telephone numbers in e-mails or popup ads
C. Review credit card and bank account statements regularly
D. Antivirus, anti-spyware, and firewall software can very easily detect these type of attacks
E. Do not send credit card numbers, and personal or financial information via e-mail
-
Question 614:
Neil is closely monitoring his firewall rules and logs on a regular basis. Some of the users have complained to Neil that there are a few employees who are visiting offensive web site during work hours, without any consideration for others. Neil knows that he has an up-to-date content filtering system and such access should not be authorized. What type of technique might be used by these offenders to access the Internet without restriction?
A. They are using UDP that is always authorized at the firewall
B. They are using HTTP tunneling software that allows them to communicate with protocols in a way it was not intended
C. They have been able to compromise the firewall, modify the rules, and give themselves proper access
D. They are using an older version of Internet Explorer that allow them to bypass the proxy server
-
Question 615:
This is an example of whois record.
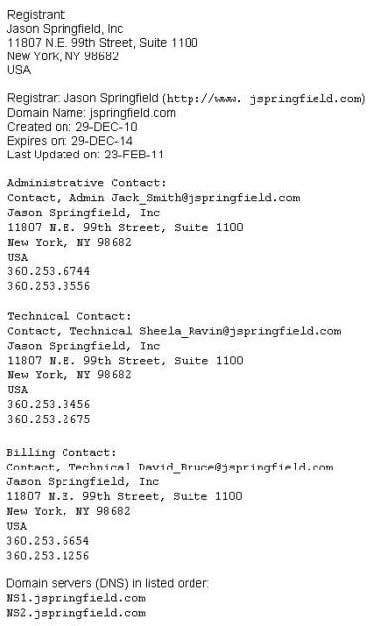
Sometimes a company shares a little too much information on their organization through public domain records. Based on the above whois record, what can an attacker do? (Select 2 answers)
A. Search engines like Google, Bing will expose information listed on the WHOIS record
B. An attacker can attempt phishing and social engineering on targeted individuals using the information from WHOIS record
C. Spammers can send unsolicited e-mails to addresses listed in the WHOIS record
D. IRS Agents will use this information to track individuals using the WHOIS record information
-
Question 616:
Blane is a network security analyst for his company. From an outside IP, Blane performs an XMAS scan using Nmap. Almost every port scanned does not illicit a response. What can he infer from this kind of response?
A. These ports are open because they do not illicit a response.
B. He can tell that these ports are in stealth mode.
C. If a port does not respond to an XMAS scan using NMAP, that port is closed.
D. The scan was not performed correctly using NMAP since all ports, no matter what their state, will illicit some sort of response from an XMAS scan.
-
Question 617:
An Attacker creates a zuckerjournals.com website by copying and mirroring HACKERJOURNALS.COM site to spread the news that Hollywood actor Jason Jenkins died in a car accident. The attacker then submits his fake site for indexing in major search engines. When users search for "Jason Jenkins", attacker's fake site shows up and dupes victims by the fake news.
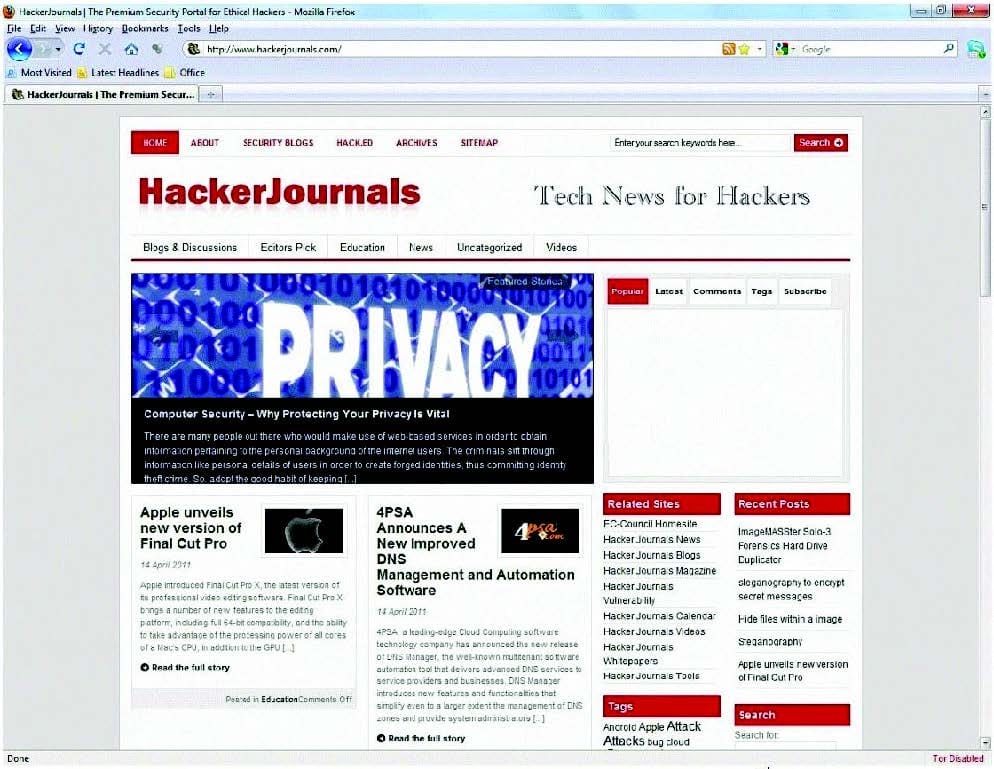
This is another great example that some people do not know what URL's are. Real website: Fake website: http://www.zuckerjournals.com
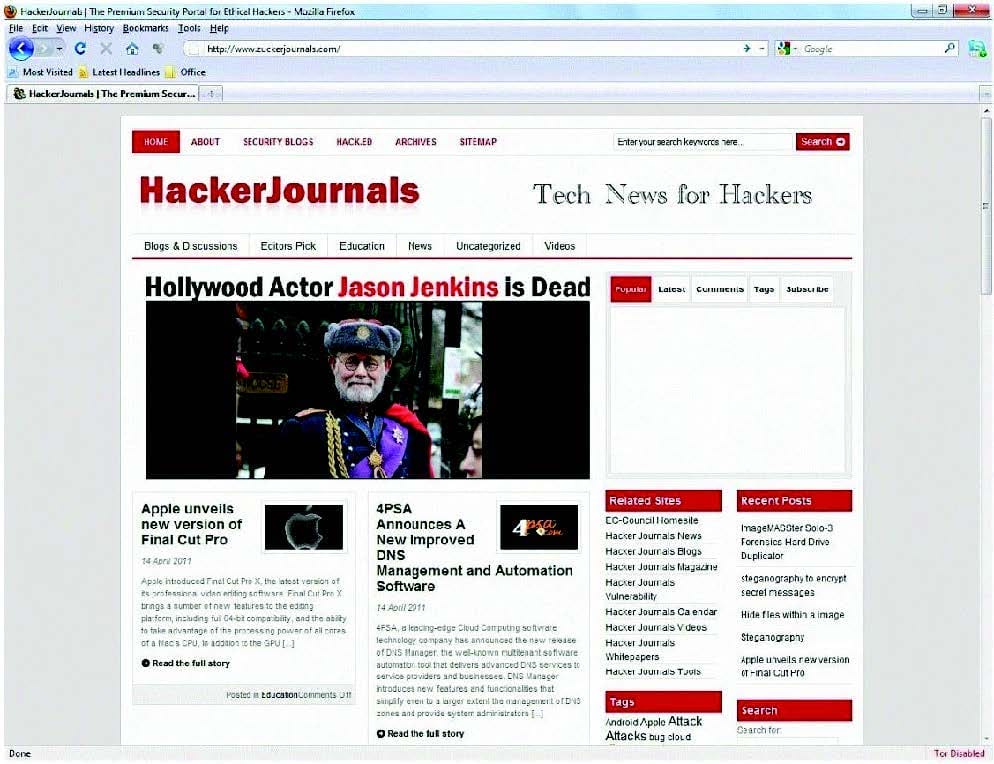
The website is clearly not WWW.HACKERJOURNALS.COM. It is obvious for many, but unfortunately some people still do not know what an URL is. It's the address that you enter into the address bar at the top your browser and this is clearly not legit site, its www.zuckerjournals.com
How would you verify if a website is authentic or not?
A. Visit the site using secure HTTPS protocol and check the SSL certificate for authenticity
B. Navigate to the site by visiting various blogs and forums for authentic links
C. Enable Cache on your browser and lookout for error message warning on the screen
D. Visit the site by clicking on a link from Google search engine
-
Question 618:
Frederickson Security Consultants is currently conducting a security audit on the networks of Hawthorn Enterprises, a contractor for the Department of Defense. Since Hawthorn Enterprises conducts business daily with the federal government, they must abide by very stringent security policies. Frederickson is testing all of Hawthorn's physical and logical security measures including biometrics, passwords, and permissions. The federal government requires that all users must utilize random, non-dictionary passwords that must take at least 30 days to crack. Frederickson has confirmed that all Hawthorn employees use a random password generator for their network passwords. The Frederickson consultants have saved off numerous SAM files from Hawthorn's servers using Pwdump6 and are going to try and crack the network passwords. What method of attack is best suited to crack these passwords in the shortest amount of time?
A. Brute force attack
B. Birthday attack
C. Dictionary attack
D. Brute service attack
-
Question 619:
What is the default Password Hash Algorithm used by NTLMv2?
A. MD4
B. DES
C. SHA-1
D. MD5
-
Question 620:
What is the IV key size used in WPA2?
A. 32
B. 24
C. 16
D. 48
E. 128
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.