Exam Details
Exam Code
:312-50V10Exam Name
:EC-Council Certified Ethical Hacker (C|EH v10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:747 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V10 Questions & Answers
-
Question 141:
Which type of security feature stops vehicles from crashing through the doors of a building?
A. Turnstile
B. Bollards
C. Mantrap
D. Receptionist
-
Question 142:
Which of the following commands runs snort in packet logger mode?
A. ./snort -dev -h ./log
B. ./snort -dev -l ./log
C. ./snort -dev -o ./log
D. ./snort -dev -p ./log
-
Question 143:
While reviewing the result of scanning run against a target network you come across the following:
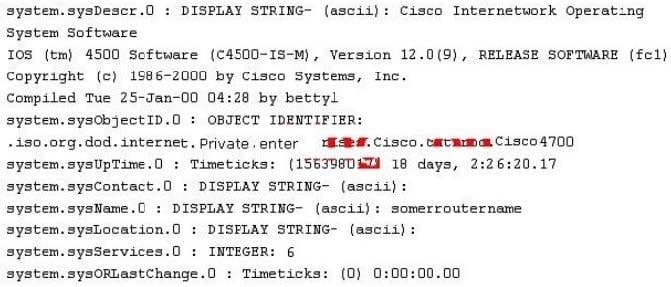
Which among the following can be used to get this output?
A. A Bo2k system query.
B. nmap protocol scan
C. A sniffer
D. An SNMP walk
-
Question 144:
Supposed you are the Chief Network Engineer of a certain Telco. Your company is planning for a big business expansion and it requires that your network authenticate users connecting using analog modems, Digital Subscriber Lines (DSL), wireless data services, and Virtual Private Networks (VPN) over a Frame Relay network. Which AAA protocol would you implement?
A. TACACS+
B. DIAMETER
C. Kerberos
D. RADIUS
-
Question 145:
A server has been infected by a certain type of Trojan. The hacker intended to utilize it to send and host junk mails. What type of Trojan did the hacker use?
A. Turtle Trojans
B. Ransomware Trojans
C. Botnet Trojan
D. Banking Trojans
-
Question 146:
The practical realities facing organizations today make risk response strategies essential. Which of the following is NOT one of the five basic responses to risk?
A. Accept
B. Mitigate
C. Delegate
D. Avoid
-
Question 147:
Which among the following is a Windows command that a hacker can use to list all the shares to which the current user context has access?
A. NET FILE
B. NET USE
C. NET CONFIG
D. NET VIEW
-
Question 148:
In an internal security audit, the white hat hacker gains control over a user account and attempts to acquire access to another account's confidential files and information. How can he achieve this?
A. Port Scanning
B. Hacking Active Directory
C. Privilege Escalation
D. Shoulder-Surfing
-
Question 149:
Which Type of scan sends a packets with no flags set?
A. Open Scan
B. Null Scan
C. Xmas Scan
D. Half-Open Scan
-
Question 150:
What kind of risk will remain even if all theoretically possible safety measures would be applied?
A. Residual risk
B. Inherent risk
C. Impact risk
D. Deferred risk
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.