Exam Details
Exam Code
:312-50V10Exam Name
:EC-Council Certified Ethical Hacker (C|EH v10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:747 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V10 Questions & Answers
-
Question 251:
Attempting an injection attack on a web server based on responses to True/False questions is called which of the following?
A. Blind SQLi
B. DMS-specific SQLi
C. Classic SQLi
D. Compound SQLi
-
Question 252:
Which of the following is considered an exploit framework and has the ability to perform automated attacks on services, ports, applications and unpatched security flaws in a computer system?
A. Wireshark
B. Maltego
C. Metasploit
D. Nessus
-
Question 253:
Eve stole a file named secret.txt, transferred it to her computer and she just entered these commands:

What is she trying to achieve?
A. She is encrypting the file.
B. She is using John the Ripper to view the contents of the file.
C. She is using ftp to transfer the file to another hacker named John.
D. She is using John the Ripper to crack the passwords in the secret.txt file.
-
Question 254:
Craig received a report of all the computers on the network that showed all the missing patches and weak passwords. What type of software generated this report?
A. a port scanner
B. a vulnerability scanner
C. a virus scanner
D. a malware scanner
-
Question 255:
What is the most common method to exploit the "Bash Bug" or "ShellShock" vulnerability?
A. Through Web servers utilizing CGI (Common Gateway Interface) to send a malformed environment variable to a vulnerable Web server
B. Manipulate format strings in text fields
C. SSH
D. SYN Flood
-
Question 256:
You are the Systems Administrator for a large corporate organization. You need to monitor all network traffic on your local network for suspicious activities and receive notifications when an attack is occurring. Which tool would allow you to accomplish this goal?
A. Network-based IDS
B. Firewall
C. Proxy
D. Host-based IDS
-
Question 257:
Which of the following is a protocol specifically designed for transporting event messages?
A. SYSLOG
B. SMS
C. SNMP
D. ICMP
-
Question 258:
Emil uses nmap to scan two hosts using this command.
nmap -sS -T4 -O 192.168.99.1 192.168.99.7
He receives this output:
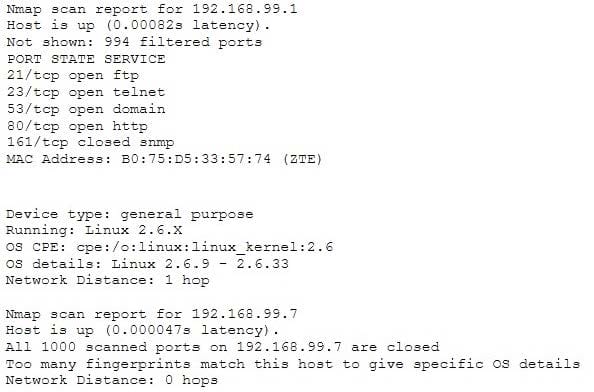
What is his conclusion?
A. Host 192.168.99.7 is an iPad.
B. He performed a SYN scan and OS scan on hosts 192.168.99.1 and 192.168.99.7.
C. Host 192.168.99.1 is the host that he launched the scan from.
D. Host 192.168.99.7 is down.
-
Question 259:
Which of the following programming languages is most susceptible to buffer overflow attacks, due to its lack of a built-in-bounds checking mechanism?

Output: Segmentation fault
A. C#
B. Python
C. Java
D. C++
-
Question 260:
Internet Protocol Security IPSec is actually a suite of protocols. Each protocol within the suite provides different functionality. Collective IPSec does everything except.
A. Protect the payload and the headers
B. Authenticate
C. Encrypt
D. Work at the Data Link Layer
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.