Exam Details
Exam Code
:312-50V10Exam Name
:EC-Council Certified Ethical Hacker (C|EH v10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:747 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V10 Questions & Answers
-
Question 631:
In the software security development life cycle process, threat modeling occurs in which phase?
A. Design
B. Requirements
C. Verification
D. Implementation
-
Question 632:
A computer science student needs to fill some information into a secured Adobe PDF job application that was received from a prospective employer. Instead of requesting a new document that allowed the forms to be completed, the student decides to write a script that pulls passwords from a list of commonly used passwords to try against the secured PDF until the correct password is found or the list is exhausted.
Which cryptography attack is the student attempting?
A. Man-in-the-middle attack
B. Brute-force attack
C. Dictionary attack
D. Session hijacking
-
Question 633:
What are the three types of authentication?
A. Something you: know, remember, prove
B. Something you: have, know, are
C. Something you: show, prove, are
D. Something you: show, have, prove
-
Question 634:
The following is part of a log file taken from the machine on the network with the IP address of
192.168.1.106:
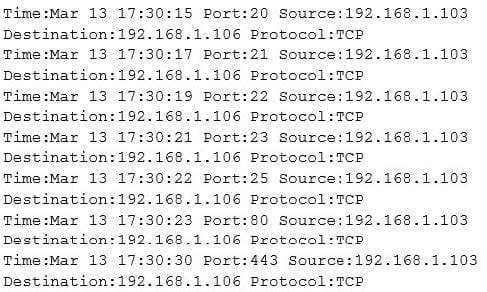
What type of activity has been logged?
A. Port scan targeting 192.168.1.103
B. Teardrop attack targeting 192.168.1.106
C. Denial of service attack targeting 192.168.1.103
D. Port scan targeting 192.168.1.106
-
Question 635:
What is the main difference between a "Normal" SQL Injection and a "Blind" SQL Injection vulnerability?
A. The request to the web server is not visible to the administrator of the vulnerable application.
B. The attack is called "Blind" because, although the application properly filters user input, it is still vulnerable to code injection.
C. The successful attack does not show an error message to the administrator of the affected application.
D. The vulnerable application does not display errors with information about the injection results to the attacker.
-
Question 636:
A recently hired network security associate at a local bank was given the responsibility to perform daily scans of the internal network to look for unauthorized devices. The employee decides to write a script that will scan the network for unauthorized devices every morning at 5:00 am.
Which of the following programming languages would most likely be used?
A. PHP
B. C#
C. Python
D. ASP.NET
-
Question 637:
Which of the following techniques will identify if computer files have been changed?
A. Network sniffing
B. Permission sets
C. Integrity checking hashes
D. Firewall alerts
-
Question 638:
Which of the following parameters enables NMAP's operating system detection feature?
A. NMAP -sV
B. NMAP -oS
C. NMAP -sR
D. NMAP -O
-
Question 639:
Which of the following open source tools would be the best choice to scan a network for potential targets?
A. NMAP
B. NIKTO
C. CAIN
D. John the Ripper
-
Question 640:
What is a successful method for protecting a router from potential smurf attacks?
A. Placing the router in broadcast mode
B. Enabling port forwarding on the router
C. Installing the router outside of the network's firewall
D. Disabling the router from accepting broadcast ping messages
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.