Exam Details
Exam Code
:312-50V11Exam Name
:EC-Council Certified Ethical Hacker (C|EH v11)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:528 Q&AsLast Updated
:Apr 17, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V11 Questions & Answers
-
Question 181:
John is investigating web-application firewall logs and observers that someone is attempting to inject the following:
char buff[10]; buff[>o] - 'a':
What type of attack is this?
A. CSRF
B. XSS
C. Buffer overflow
D. SQL injection
-
Question 182:
Elliot is in the process of exploiting a web application that uses SQL as a back-end database. He's determined that the application is vulnerable to SQL injection, and has introduced conditional timing delays into injected queries to determine whether they are successful. What type of SQL injection is Elliot most likely performing?
A. Error-based SQL injection
B. Blind SQL injection
C. Union-based SQL injection
D. NoSQL injection
-
Question 183:
Alice, a professional hacker, targeted an organization's cloud services. She infiltrated the targets MSP provider by sending spear-phishing emails and distributed custom-made malware to compromise user accounts and gain remote access to the cloud service. Further, she accessed the target customer profiles with her MSP account, compressed the customer data, and stored them in the MSP. Then, she used this information to launch further attacks on the target organization. Which of the following cloud attacks did Alice perform in the above scenario?
A. Cloud hopper attack
B. Cloud cryptojacking
C. Cloudborne attack
D. Man-in-the-cloud (MITC) attack
-
Question 184:
A penetration tester is performing the footprinting process and is reviewing publicly available information about an organization by using the Google search engine.
Which of the following advanced operators would allow the pen tester to restrict the search to the organization's web domain?
A. [allinurl:]
B. [location:]
C. [site:]
D. [link:]
-
Question 185:
A large company intends to use Blackberry for corporate mobile phones and a security analyst is assigned to evaluate the possible threats. The analyst will use the Blackjacking attack method to demonstrate how an attacker could circumvent perimeter defenses and gain access to the Prometric Online Testing ? Reports https://ibt1.prometric.com/users/custom/report_queue/rq_str... corporate network. What tool should the analyst use to perform a Blackjacking attack?
A. Paros Proxy
B. BBProxy
C. Blooover
D. BBCrack
-
Question 186:
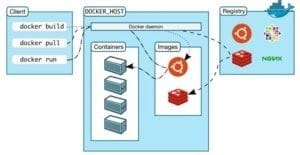
Annie, a cloud security engineer, uses the Docker architecture to employ a client/server model in the application she is working on. She utilizes a component that can process API requests and handle various Docker objects, such as containers, volumes. Images, and networks. What is the component of the Docker architecture used by Annie in the above scenario?
A. Docker client
B. Docker objects
C. Docker daemon
D. Docker registries
-
Question 187:
What kind of detection techniques is being used in antivirus softwares that identifies malware by collecting data from multiple protected systems and instead of analyzing files locally it's made on the premiers environment?
A. VCloud based
B. Honypot based
C. Behaviour based
D. Heuristics based
-
Question 188:
A regional bank hires your company to perform a security assessment on their network after a recent data breach. The attacker was able to steal financial data from the bank by compromising only a single server. Based on this information, what should be one of your key recommendations to the bank?
A. Place a front-end web server in a demilitarized zone that only handles external web traffic
B. Require all employees to change their anti-virus program with a new one
C. Move the financial data to another server on the same IP subnet
D. Issue new certificates to the web servers from the root certificate authority
-
Question 189:
Which of the following is the best countermeasure to encrypting ransomwares?
A. Use multiple antivirus softwares
B. Pay a ransom
C. Keep some generation of off-line backup
D. Analyze the ransomware to get decryption key of encrypted data
-
Question 190:
Tony is a penetration tester tasked with performing a penetration test. After gaining initial access to a target system, he finds a list of hashed passwords.
Which of the following tools would not be useful for cracking the hashed passwords?
A. John the Ripper
B. Hashcat
C. netcat
D. THC-Hydra
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V11 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.